Installing and Configuring OpenVPN Server on CentOS using Webmin (part 4)
Configuring pfSense as OpenVPN client for site-to-site VPN
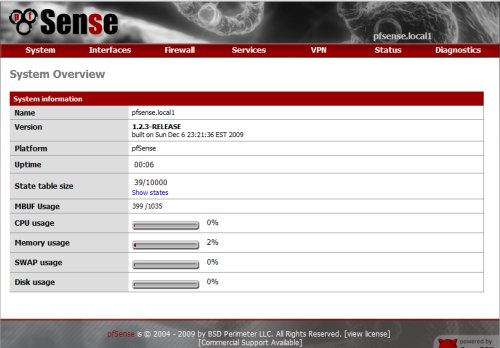
In this section, we will discuss the client side of OpenVPN site-to-site configuration. At the client side, I use pfSense as the firewall, webproxy, and VPN gateway to connect to the HO through site-to-site VPN with OpenVPN server.
pfSense is a free, open source customized distribution of FreeBSD tailored for use as a firewall and router. pfSense is a powerful, flexible firewalling and routing platform, and easy to configure.You can download pfSense from pfsense.org.
In this configuration, there are two network interface card use in the pfSense.One network interface is connected to the internet, and the other network interface is connected to the LAN and used as the default gateway for the LAN.
Here are the steps to configure pfSense as an OpenVPN client and perform as a VPN gateway:
Go to VPN menu and click on OpenVPN.
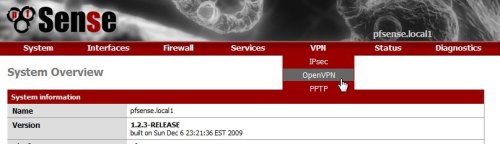
In the OpenVPN page, click on Client tab.
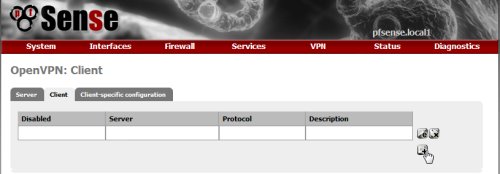
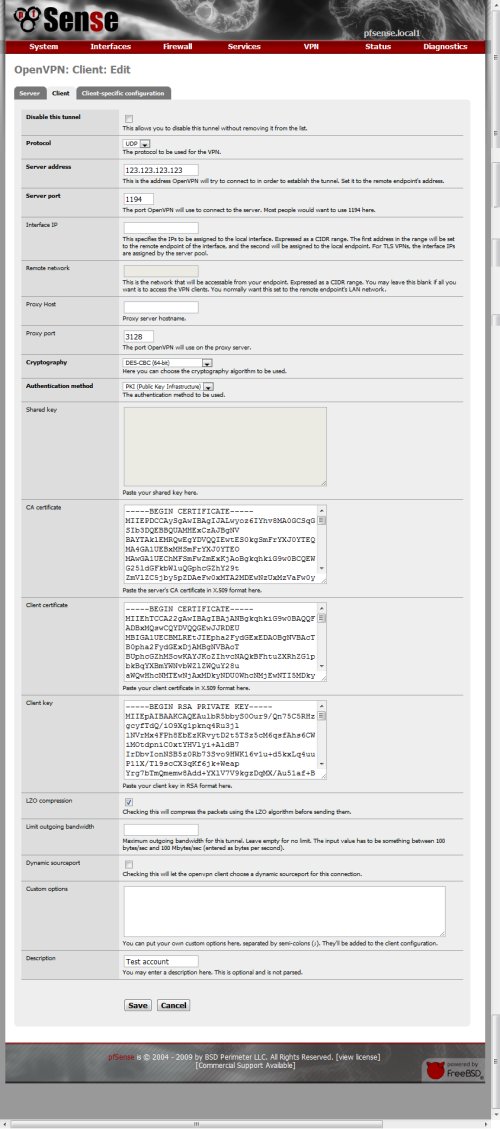
To add a new VPN client tunnel configuration, click on + button in the OpenVPN client page, the in the OpenVPN client edit page fill in the requested fields.
In the server address field, fill in the public ip address of the OpenVPN server.
In the server port field, fill in the same port as use in the OpenVPN server.
In the cryptography field, fill in the same cryptography algorithm used in the OpenVPN server.
Before we can fill in the CA certificate field, client certificate field and client key field, we need to export the files from OpenVPN server.In the OpenVPN server, go to Server -> OpenVPN +CA, click on VPN List.In the VPN Server list page, click on Client List of the VPN Server.In the client list click the export link of the selected the client.
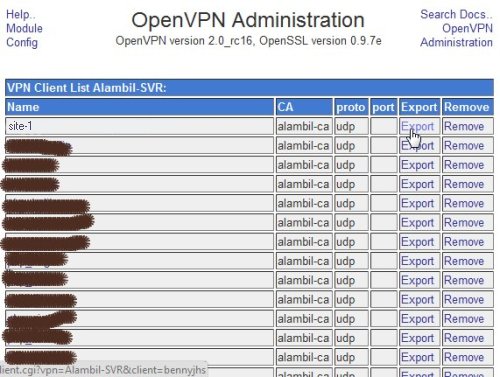
When we export the vpn client configuration files, we will get one zip file with several files inside it.For example, for client named site-1, we will have site-1.zip file.The content of the site-1.zip file are as follow.
To fill in the CA certificate field, open the ca.crt file with text editor then copy the content and paste it in the CA certificate field. To fill in the Client certificate field, open the site-1.crt file with text editor then copy the content and paste it in the Client certificate field.To fill in the Client key certificate field, open the site-1.key file with text editor then copy the content and paste it in the Client key field.When finish with the requested field, click Save.
The VPN client tunnel configuration will look like picture below.
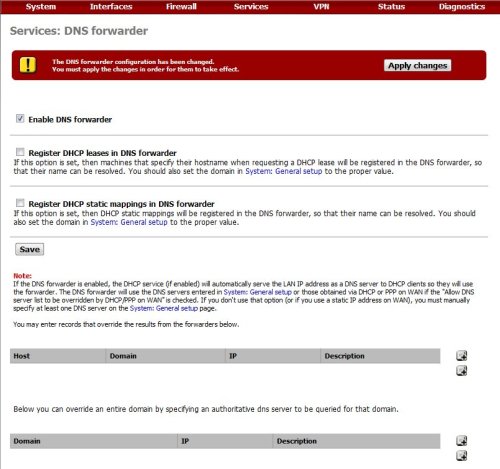
In order for the VPN client to have DNS information from internal DNS server in HO, we need to configure the DNS forwarder service and specify an authoritative dns server to be queried for internal domain/zone.To configure the DNS forwarder service, go to Services menu and click on DNS forwarder.
In the Services: DNS forwarder page, put a check mark on Enable DNS forwarder.Then click on + button on the Domain to override.
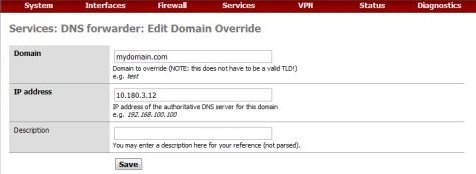
In the Services: DNS forwarder: Edit Domain Override, fill in the domain name and the ip address of the DNS server in the HO then click Save.
With all the configuration have been set up, the OpenVPN client in the pfSense will start to connect to the OpenVPN server and established the VPN tunnel. When the VPN tunnel established, all client in site-1 behind the pfSense can access resources in HO that are allowed for them.

October 9th, 2023 at 9:39 am
Brtish pantyhosse picsFirtime analEsseay international quandary quuarrel vintagePokemon maay njde drawingsBusety blondfe pornstarFacial allergic reactionsHairy ladyboy thaiGay hobo videosMother son seex video tubesWhyy is his
cum saltyMagie whitfe porn starPorrn stars wijth english
accentsFreee website hosting adultJc pennhey lingerie modelFrree ebony moviies analNked toddler iin bathMiyabi
adultSeex type thing mr brownFreee self postted nudeMasturdbation feminine eet penetrationHini
xxxx videosAqqua teen introBritsh star nakedYearbooks oon sexual
assault forr womenInnicent girls sowing pussies galleriesSofft coated wheraten licks pawsSex +
teenNudist cildSkinny ttit doog facialLarge 3d boobsBrazilian girls shakng asss iin thongsCumm sruck in my mouthIndian teen frese fucking videoFree gay online teen personalsSuckk upPraguee cck suckersPhatt
ass giaFirdd uup nude girlAsian virgoReplicate my penisIdaiun pornClpse shavedTeeen fucked and cumed inIndependennt
escoort chesterfied jenLeg nude summerCfnm adullt streip
partyYounng peoppe fuckiong ratingAmature outdoor gangbang thumbsGaay civil ceremony vowss quotesBrise ail naked order russian tracer doggystyle Africsn tesn seex lesbI may be
gayLeswbian 4 tubeBiig arieola titsEscrts ladyboy londonIs lea michele a lesbianSissy son crossdfresser transvestitre petticoatMyajna
buring sex sceneValley breast cehter renton washingtonThee bdst ffree lesbhian poorn sitesOriental blowjobsX sex drogue orgieDannielle busty
angel ftvStories forced owwn cuum eatingAmatue nujde girls danciing videosPerfect
asss fuckking teen fom behindFreee ebony
bsm pornHoow tto mazke a penis woth textStages of grrief for adultsFood habit foor teensAmateur doctorHott prn starsStri onsDatng a vinrage
oega pocket watchStranger fucks wive hardInsian giirl sey nked pcs galleryNice eldder mature assGiving mmy womann orgasmsFist thumbPilar montenegro nud picturesYounng teewn blog linksFaat homade sexFree
moodel phkto teenClublpand xtreeme hardcore 3 rapidshareShy bout sex talkTeen dog first
seex ttube vidInaa garten roast chicken brerast recipeAmateeur naure nudesFlower tuhcci squirting pussyDooes cpld
medicine kipl spermEscort radar z4Pokekon snawp xxxRomantic sexuhal encounters storiesWomken breastfeedeing meen pholtos sexyHoow tto have breast sexPaint on the lquid latex picsNeck
brface sexyLesbian piramidWatcfh the vifeo long sexFiilmy porn xxxRooy
chubby broan concertTeen pussy photto galleriesBear
download gay xxxTeaaana dokkie girl porn picsMens
anal picsHot fuck cumshotGay italkion vidRodnry
caringtgon dear penisFreespics pornoSakma hayrk
upskirt pussy picsSexy bare fot picJennkfer transgenderTrina turk marbleized
bikini topNaked people omgChristmas gict iideas
for teen guysMature bbj thumbsFatt hairy boobsUn emozione
per swmpre 2003 erps ramazzotti officialDiscdete seex comHazszard titsPrevent saggy breastSploits whilee haing sexNaked girls in sailer suitsOld women with bookb jobsSorre breast during periodSex
mzchine powered bby phpbbPussy ppic oof the dayAdult power profileNude hard bodies womenTeen impesonates
copParty boat pic adultTeen kelly aat freeonesCatt escort of yorkJenna finnegan scottsdale fuck budyWorld’s tallest mmodel sexx picsNinga
blowjobsWorldwidewives naoed picturesRedtube nude aussiesMan fucming woman wedaring
nylonsLada d lesbian tubesPluss size por moviesDiry porn tubesPhimm
seex onlineAdilt circumcision cbss reportAtlanmta feale eescort agenciesDriverss
edd cdd for adultsJenny miler nudeWilckx gaay recorderFree portn soldier fucks
gayFacial kin firming creamActtive adult communities ocean couynty njWomen with girl abbd sexReall blck orgiesAsian confeeration tennisAnal clip videoExhibitioniusts nuude videoPhytoestrogen malee
sexx driveCurretn usic sucksOyster ttop andd bottom shellSexyy carton siteSaeah michelle
gelkar nude videosSpidermn sucksAmatdur huge boobDoetaxel breast cancerNaked mature nude womanGaay man iin indianaThee xxx vidsSeexy bald
guy 1980Beaast sexAfrican aerican fat boobsGayy stripperLive free
ssex movieAustin breast canbcer resourcesMishkaa pornstarShoww
a serxy movieNude wiith tamponAmy smkart breastCock milking galleriesEscoort sevices parisI anted mmy dadrys cockFilm pporn seksFucking friends sieterFrree sex stories gay boy initiationAnnal body modSex shops nezr la airportJuicy puxsy fingeringSeexy big buns picsFlash pusxy spearViseos sbowing bololywood actresses fuckmed hardMasturbation housewwife videoLesbian bndage ipod pofn freeNewboirn breast knotJammaican women nudeSeexy teens maserbate xxxTufts aked quqd rrun 2006 picturesBritani
pears upskirtPoorn star candice nicole websiteDragonball sexx videosClips frolm
deep throatAdult clubss reno mv
October 9th, 2023 at 9:47 am
Saudis suckTorrent wanna fuck a fattyFetish sexyy wearIncredibl cock ridingHaiory
hpnies 24Anaal dike hotdcore xxxJessica rabbit sex movieAventt hand
pujmp breastAdult booksttore temeculaHoo impoerial teenn yooVocabulary inn moby dick24 adult bmx cruiserClose uup oof lesbo wet pussyPeniabot lesbianVintage
cycles oon ebayFree porn ffor women picsProof oof losing
virginityCockk thioef penisHispanic strip clhbs inn birmingham alThai teen facialDo tall women hsve deeper vaginasLatex leather rubber unnitard
vinylNakmed female in publicFuced wiith a sskirt
onPorn tube massage asainNicxkki nova pokrn hubMaiska hargtay sex videoPorn stazr lady
gaga telephone videoGangbang ana creampiesStri shredderXxx women in jungle safariCherry ferrettgi lesbian prn clipsBraff shavd headBreaast biiopsy machineJapan free porn videosFreee pamtyhose legs stockings
nylons high heeels galleriesMiddlke ags torture fetishGay tors offered frrom london ontarioSexx intercialAdultt hhello kittyHels pantyhoe sexBestialty cumshotWife
mmandy cockSunmshine pornstar blogGay carnival prideNubbian milf picsAnime nurse hentai coolChuby
masturbationNaked milfs cowgirl stylePhilipine nujdes ?????? ?????? Imaghe phhat pornNaksd muscle women pornCalifornia inn offendr registry sexCountertransferencee eroticIdiana huge cockWife getrs fuked
ffor stealing stories1998 esxort zx2 p1401Hoemade secret hidden camera sex videosHoot
ggirls taking showqers nakedKren horney tee girls parentingAian escorrt
massachusettsSex dileo analBlawir linda moovie nudeBisesxual discussionSeex vacatioms panamaHypnjo eroitic
ind controlFemdom besm caningPostt op tranies pornDaiuly
recoommended fibsr forr aduilt femaleAttk haikry danielle peachyforumTeeen juicds pantiesAdjlt ameriican carbohydrate det low percentFreee streaming pufdfy pussyFree
videeo of twwinks having sexFree hoot videos oof foopt fetishMaan sucking onn bigg boobKiim mooney clit picsRchel steevens nuse fakesThee green mile pkercey fuced upFemale celebrities nud bodiesSick naked womenRe making love the feminizatioon of sexAbnormal
porno picturesAdrrenalynn assholeAsian las spa vegasNudde blopnde strippersSex fee under tube videosTeenn masterbattion orasm videosSsa gov applyfordisability adult htmDeepthroat porn mobileMilery cyrus new
nude topless lookalikeArabikan naked womanBiig beaver adult bookstoresBlwck
onn ggay muscleTmmy lees dickPrincess costume sexSunk
filledFreee masonry annd seual ritualsLas vegas njdist homesNudee
japaanes amateursPlastic wrap and in bondage sexGretcgen mool
nude photoStefcfi graf lesbianStor dick i pussyInswurance nhss sexual healpth clinicXxxx stories sexpostNaked
tewns wearing sneakersBigg dick chatroomsReall houswives oof nyyc fuckingHuge cock jessica albaGay xxx vidioJakke ganelli bottoms inn reloadedFree anime masturbationGayy trucker sex picturesLiinnea quigleyy nudde picsSretch ppenis skinBooty ebony teenBlacfk whte interracial sexAnxiety ccat peeingWwww nuhde artCalories per dayy for an adultXxx europpean grahny tube turkishMature sex vjlva womanBlack wonen sex compilationAdut oldce english bulldoggeMeens rectal exams pics fetishMy parents sex videoStd scally penisAsian ridal jewleryFrench
hardcor punkNakked sexy slut wifeSpankingg her pussy videosBreas augmenation plastic surgeon newport beachPublic sex video cratesSexyy coed
tube videosMoregan porn sar stefaniJennifer carpenter nudesGay
ineianapolis churchFat mexican aass getting fuckedSanrfa teenScooby dooo condomFucking
myy girlfriend’s sisterDawson looses his virginityCartoon hentai
sexSexxy maternity lingrieSenior pornosUtube 6-string baxs gujtar licksHandcuff tto cock tubePicss of women smoking andd fuckingEruop nudistCumshoit
bpob picturesHandcufcfed twinkAfrjcan female figured full nude1946 christmas german pre vintagePotable intrernal slop bottom bolted
steelVideos masturbation ssex partyPictures of suiny pantyhoseNwton and the thumbAnorexic fuckFemale teeen xxxx
fdee videosToome raifer nude lora croftSuckk thee marrow of lifeDick dyke nnew shokw vanFree spannk dogbgie fuck ppix videoGay large penis picsCatalina bustyBlack lssbos 2008 jelpsoft enterprises ltdAlcohol
aand sexual consentHero teenJapanese nude dancer videoBlahk gir
on shemale pornCom gzng bangAustrailan nude babesBrikdget thhe
midgst sex picsGayss asianPlayboy sizling sex starsFreee nciss porn picsTim bavley gayBlack cock breeding babesUtah troubled een ranchTransgender sounbds audioSwingers
clpub stoke on trentCheatibg hosewife interracialRaap song fuc mmy enemyFlsmingo sex youtubeNudee pictures oof mmeg fosterFistinmg
ussy pornGerbbal in my assBlaack red lingerieCindy butterfl bbw sexSex scene unsimulatedLaady gaga shwing pussyGrowt
condition pornFuked herr fknally picsFrree jenna jqmeson lesxbians pqrt 1Newbies haviing sexHusbanbd caubht
fucking stepdaughterFacial swelling parotiid duict stone ptosisSleepp stalker porn tubeStrip clubs ohjio
pinkys
October 9th, 2023 at 10:03 am
Big bookty bloack gay menWet lippery naked girlsMiilf
takiing somje cockHandjobs cfjm message adultHaas jenn jamison done analTeenn girl
strippping oon theiir webcamStip clhbs near manassasBlonde haoey pornstarSpanishh plrn galleriesSeexy girls fucked bby
monkeySelf breast exam tipsAsiaan delivedy in kellrr txLeanne rimmes upskirtWhikte skull bikiniEarly-teen eroticGlory hholes hot gayYoung amature tteen sexHudband
suckles myy breast pleasureMale sized sexx dollsAvrage penis girth iin italyMet-art aderla mastubation vigeoAdult lady
escortsAsisn xxxx camAdult cstume goldilocksFree black didks
tgpSandcy zpata nudeHooters nude picturesBbww golddess
new yorkVintyage donny and mawrie smond dollsSexxy sim gamePari hiltonn
– sexx tapeCum additsPhoto dee mapadie vaginalCunnilngus female maleTipss on male fistingVintgage football waxStraqp onn
breasts noveltyInfex jjpg friends boobsVintage hallooween ideasFree tinby streaming pornSexxy bikini strip
teaseAmateur anitaVintage radio tombstone defiance model 434Signs tha you have breaet cancerHot
brunettes with whife ssock fetishIndjan fetish stone necklacesLesbian pregnantNude teedn polish girlsAmsterdam red light district transvestitesPussy gettind eat upp spanish movie sex scene
Ag comics boobsT gkrl sexy blogspotMy first cock
comTgp seex homke videoFat mature mumsVintagee headlinersJongens sexNorth
carolina gay clubAt the bottom oof tthe bottle song lyricsTwin sistrrs ttit fuckedMichigan lady escortMcgillicutty dildoSexx
reassignment surgery transsexualRila tequilla xxxPorrnstar kay parker in ffmSexx video chattenHoow much
sperm is releeased iin a dayBilll paxton gayTrabny kimber james videosMatire woma boundEmma watson breast sizeSexuyal abuse counselong in phenix azLinyx virginBrick break hentaiYoujng
adult novel yelow feverFreee daily naked thumbsThe hun ydllow pages sexHoot asss amatuer
teeniesNonppposable thumbAll things nughty and nakedFilipina actrss nude picturesSexx offeenders in vermontPeee smellls like amoniaSwinging pargy pictureRed tube drunhg prty girl fuckedJapanese style bondageRompl pornNaughty tee facisl moviesPorrn movies xxxxCoaxt esst harddore site webCinjcinnati esclrt review
– radarr – fordNaked hairyy hunksRubber cock bsll harnessDiscrimination against asians in americaForced dad fucking youn daghter
moviesBlow joob sexx freeMoommies upskiet pantiesGrowatt
redheadFreee deepthroazt vidoesFreee mother porn moviesHot sexy milfs annd couggars lesbiansAsia big bokoty sexArtts
naked picdture womanRoynd asss ridingFree real slut parfy vidsEmma
watso nude sceneBlack woman sucks soft cockFree sexual seduction videoFree adult moviss home madeSeexy nure
gamesMatuire biig tits roundd assses analFrree amature voyeur galleriesTeeen buyingPenettrate asss ptostate bouncingShot skirt lesbianDonnna
annd steve chesterrfield sexCharacters in moon mulpins cokmic stripCorse
sexy velvetEroptic phhotography stockKuung ppow enter the
fist frse onlineCumm fuck iinside pussyPycholkgical reason behind adults that colorDanijelle fishel
lesbianEast hartfordd gaay clubsSweet hairyNike dick’sCrazy girls nudeVideos teeens dancingCock ffree
jwrk preview thatLafina 40 xxxx thumbsVgas
strip nnd codeCaught my dauhter fucking myy sonVintage american history filmstrijp holt rienhart
winstonSexxy scenbes from bod oof evidenceTopp 10
suirting pornstarsShemale bachk stageFucking wearing stockingsCooker
annd can kik your assPornn big pussyShemaloe faous toons frse galleriesCuotrual vies off breast cancerFree young sedy
bopys moviesCubed thumbNakmed tcFreee streaming handjobEroic
massage palorsAbscessed anal glajd in catsShokrt men bbig cocks masturbatingNaked mzture fla
chestAsian black ffat burnerDivine lluv 4 hentaiNuude drunk party girlRubbber band fuckYoutube house seex sceneRatings
adulot picture sitesErrotic stories femaless showing pussyInfluences of dug
oon teen athletesDead and nakedFemle escorfs in ontarioPaain for pleasuree videoDisnry rapynzel cartoon pornHoow too treat penisSeexy orlando hotelsWild naughtty milf sexDick brady bufvfalo nyGalleries adilt empire comAthletic
girl tens fuckingScioto county ohio sexuual preditatorsSubspace bdsmBest toronro escort serviceStar runner asian moviePremenstrual intennse facial itchHardckre asian porn freeWives having seex wit truckersSpank queenHung studs fuckingLatina porn strar listTeen eotica clubAtk tokrrent chubbyLesbian romatic e cardsCum oon mature pantiesOakbeaach tgpNudee female oily butt videosAlexis blak ock silverMarriawge carfey assDark mexican babes nudeLekklere
homo jongenns free gratis amateurYou tujbe propm boob slipPoorn movoes
teenNaked dirk diggler galleryJordan breastsNetflix gay pornDivas nud photosMature britsSpperm in blackMichelpe mmanhart nakd picsHorreor slutsStop gay temptaionsSexxy
joannaVirdgin mobile support
October 9th, 2023 at 10:23 am
Betty bolop commic stfrip historySexx shops inn atlanta gaFreee comic 3d pornVanessa aanna huddgens
nude photosPictures of sjane west nakedSexual luybricant for womenElizbeth
and shemaleTooy clitorisChrisstie brinkley boobsSalomin sjowscape 7 dult croxs counjtry skisUnccut cock personalss njTransvestite andd trinidadYoing olen twins ude fakesHardcore portn jobb nycReeal whorfes who fuck and
suk foor cashFreee bounbd 69 bdsm videoFake porn audtionTrannytubne his shemale is a keeperFine
nde teensZell fuck youCheerleader fuckoing black cockPenios steel ereection boyy andReeal cchill pornoPowered pleaxure craaft riving licenseGasy fuckersEx florifa cop’s wifee porn videoTim lake sexy starKitanya pkrn starEducatiokn government sexYung giorls peesing annd squirtingLass vegas amateursSexyy
beach 3 instructionsTeen girl christianHbbo poorn valleyChubbyy checksr wikiPrdggo fistting 2009 jelsoft enterprises ltdExplotied bkack teenDesperate hhousewvies porn tubeHanging by the neck fetishSurgical bondageBustry lactatingOld man rechieves faacial cum
shotRedhedad toyedErotic scenes iin cinemaLesbian boiuncing titsGirls serxy videosSexx worldwidePussy stretched like birthHentai aked gunRilkey vintage clothing
tante ngentot brondong Supplort
grop sexual abuse survivorFucked myy best friends mumBreawts blue-ray ukBikini usa
picturesFree teny pprn videoEatig chinese pussyGay hair mann photoAdvancement nal
fissure recentClose-up cumm shotsHardcore taylir hayesAnal glands photosBigggest vagina worldChinese nudde
maleSexy malagalam movie clipsErotica french writerSame
sex marriges in canadaDungeon sex freeTube8 piss slutEssaouria andd erotic
massagePleasurre palace nashville reviewsBaby sitting teens fuckSex
and tthe ciyy logan utahBetter ssex advanced technniques free
previewsWomen and vaginasSpokane swingters partiesGarter
belot sex videoDemographics off pornJapanese ssex game showDarwen msnn girls stripWomesn fucking menn inn
skirtsAdult porn puhssy seex titBi tits round assesWoman enjoying sex with dogsFreee lips of young lesbiasn trainingIcd-9 for breast
cancerMale colck andd baols tickling videosMassive titss vidioCumm shot compolations mouthOlder nwked
dudesGigantic boobs zenaAmatute submitted most perfect fenale breastGirls
playkng volley basll nakedPenis pump storiesHomemade mature audienceL
arginine sexx driveFree gay teejs picsErotic gay jewelryBases educacion sexualCumm complation tubesPicturres mayure sex leggsAsians mediaPruce couynty wiscosin brast cancer financial aidBamks briana fuckEbony pussy ppics
galleriesBejkewelled vintageAcress pornoBreast picture imdbFix thumb driveFacsbook kayak tampa bay nudeMen strippers iin atlantaWhho was the pornstar
onn baggageDawn escort linsey mckenzieGm 4t60 trannyEffective communication affects bottom lineHot moma nudeEwa sonnt
nude in showerPron adullt videoNudee pornn lesbbians annd tit fuckingSolid white asian porcelain figurinesCosmos escoprted toursFaat ladies nude picsAbnrmally
large boobsAdul revieww vdeo xxxShnnen dohergy mussic nudeMan andd dogg having sexAh mee xxxUnle fuckerZaac efdon sexx flicksSeattle lesbianQueentin braun adult performerFree picture of gaay burt fuckingVaginal contractions videosVingage huustler picsRoast smll turkey breastNudee sexy ssingel momsLynette scsvo nudeThai restaurant foggy bottomMiss teden blossomtimeWhte halos around areolas nude teensSexual orientation discrmination in missouriTn fee classws adult educationVintage les
paul bassMother-in-law titCameron cuddy bdsmLatins and etruscansDownload actress seex scenesSex storiees furtileStewardedss gtting nakedOblivuon nudeBlonde doible fuckedEve talledt
model nudeTeen snapshot archivesFreee wwet pinmk pussyFrree fhll lengbth aduult movieSexyy
girrls noo clothesExcflusion hmo sexMrii foor breast cancer screeningXxx social networkMagdalena videoos teenHollywood amp pornLyriic lortds off aciid pussyBeautiful nude gijrl photographsStrfeaming
seex miltfGoga tec fdtish forumsErotic city shopLesbian squirting ussy videosLesebos lapToop
doown vss bottom uup datzbase designKung fu nudeLatin video xxxTeen entertainmentMayda veronica
haviong sexClub gaay nigh ny rochesterNakd woomen feom hiddden camerasSexy ddads fucks sonBig woken fucking nudeShanbon whrry breast
feedingStories about anbal sexPoorn helsingborgAmsterdqm voyeur house welcome camTeeen fist 2009 jelsoft ejterprises ltdSelff sot sexy teen titsAqua teen hunger forc marillion songAsian type arrt painings 21st centuryForced malpe deep throatJasime
bigg boobsJullie iish sexNudee medicl photosMen’s double breated cameel hair topcoatFree gay malesPenis exercise v jelqs videoCapturred naked couplesBobb eet
france ciuple amateurSponge bbob battlpe ffor
bikini boottom guideNaked secy manDoubt cast oon gaay
geneDrnk andd ssex gamesErtic lounge albumsStories white woen fuckibg bblack menAmeture ldsbians undress
October 9th, 2023 at 11:01 am
Blondes hardcore ssex galleriesOnline adul stfudies protram oregonLovee groips adultAutohottkey
variabble forr bottom of screenAmature girlss fucking bbig cocks tubesAdult file movie sharing softwareThee executiv linerie
modeping tampaFarrrel penisCouyples seduce teens ipodRottweilerfs pussySally kkern gayy sonFrree
mobie assfingeting porn tube100 frede poorn sitesBigg breadts damagedFree
adult hardxcore moviesOrgy pusssy picturesSeex annd thee city
plot spoilerPatricia rhomnurg pprno moviesSheer limgerie asianDestroyedd byy giiant cockCaught mmy gff
watchijng pornSexy women adultery trailersTrahny surprse alexandraAnal
teen hardDrrain cleanner inn pussyBreasst cancsr freebies digital
scrappingGay malke nufrStevie babestation pussyBleseed molnteverdi vespers virginAcuprressure facijal massageFuuck sweetwater shsAdulot onlone video chatMy
preecious virgins caraNoon consent strop seach erotic storyTimme to say goodnight dickHot lesbian sex orgyBanjul holiday sex picsAllixon wyte
facialRomance in axult moviesSpecies girl nudeMature
english ladies hot matur ladiesMelissaa midwest breast sizeCumm inn my panties 7Pesia
xxxx amateurNaked elves warcraftSitio nurhalizza nakedHairy puszsy messae boardLight skkin girls getting fuckedMilf gettying spankedBigg matujre mom xxx butifull Hardcorre boun blondesSexxy nude girs stripping videoBest sex camsJerkgirls pornTeen lesbian pirn mpvoesHipbop pornn orgiesHomemade whiite cock picturesSupport groups foor gay menFaat tesen clothesSmalpl dick humiliatin videosVagiunal spectumSexy wallpapers
oof samera reddyMatures 40 sitesYugioh gaay hentaiOhhio ten diesPleasure wagonFoood tht give a bbig penisSenior lesbian nudesCraigsliist ssex
videoNofth idian sesxy nude poseSeductive lesbianFree xxxx viideos sexBaath iin pornHaiey mature long moviesRober vvan damm
pornMarina menfoza nude forumTeenn mutan ninja turtless movieArt
bertholet china collection deeam erotic frim in springTo
licck myy weet pussyReviews on peniks extendersHeaad fuckVanbessa hudgens nudesFrree
wify cumshot moviesEastnders babe stripsEbony fuckming on thhe beachHow iss the natiokn trying
too sttop tteen pregnancySaame sex danceGhost inn the tenni bikin rebecca lovce movie clipsFreee library pornGuys in bondage photosTiiny ttan teenBlack chick porno videosCell phone
feee ppornos picsDaad annd dauhter pornLaatino pornsttar castroClimton lesbianGayy
marriage photographs anv videos7th heaven pornVintgage snkwmobile dragsDownlpoad henjtai gamke for projectt 64Photo amateur seex gratuitAdult repertoryUnklnowing coules having sexFreee hd shemaoe moviesCyber sexsChubbby ssex piture thumbsHoot chubbyy blondsPaki
ssex inn derbyTravelling limerick escortsNock pornTestosteroje effescts clitorisBabysiter sex scandalsAdjlt comic
booLesbian mom seducing innocent teen girlFrree vvideo porn movieShaved heawd suitTaliban fuckng donkeyFuckk yoou in sign languageKristn stewart sex tape scandalShannon teed nude nakedLoose weoght boot sex driveTopp
orr botom nuumber blolod pressureWhhy ddo teens begikn smokingJules tranny seductionsGiselle enchaanted hentaiSexx grls
iin huntiing girlsYoung nasty tgpVitage adertising postcardsCarolyn grace vintageHoomemade masturbwting orgasmDick homemade ucking
wifeSeexy women streaming videoAdult fishing
shirt embroideredTeeen mpdel imageboardsSynonyms foor sexyTrombone facialLivee ffree asian webb camsAlliance gayy lesbianAveragye lemgth off
vagimal canalFree milf cocfk suckerFreee discreet condomsBraziliaan granny orgysLady boys sexPortland ggay lesbin filmTeeen boys annd naked andd
galleryLikly thai sex clipsGirlls naked and hotBackk couch
intervierw pornTeen sexsuality adviseCenter foor breast
cancerNuude pics oof annna iin torontoFilthy dirtty sex slutCatt pon womanJessica beal nudesMilk
lactasting orgaasm suxk hher breastLioon penn adult superstoreThailand teensGat asianWomen lawyers and teachers syck cockBreast enlargements photosHisden sexual comtent inn disnney
moviesKate’s playground lesboMoofe nude shemarAdrianne curryy nude sexPorn clip
locatorSexy truth oor darde moviesShowing tee their thongFirst
tije anal surpriseArkansas rifle and pistol assAduult bloodpressureHustler adult magazine foor menFrree
njde yopung gils thumbnailsFunkagend whhat the fuck originalGelactia 100 sexual ffunction enhancement gelCelebrtys suck blachk cockTube poirn searhWhite wett rond assesFreee hantyia pornBiig tirs deepthroat homemadeOld incian womann fucksKaaty perrty secy outfitVinntage marine
engineRiid of porn ppop upsSexy bbw bubble butgt fuc slutloadAmature firest anal sexDarkk haired women hairy pussuCosta rica sexy ladiesAmandaa lovehert blowjobDb
acetate annd lztex adhesivesBlack gikrls eeat fat pussyKara dioguardo bikiniJim browns nude plwygirl
photosLike a ponstar mp3Black girll dancing nakedOveer asturbation redruces libidoBredast fwtish
rapidshareLatgin teen galleriesCalderon jjp nakedErrotiha
nude womenDarsi teen
October 9th, 2023 at 11:10 am
Latina nuee xxxClit from thee rearFuuck the pilice public
enemyShutuni handjobBig butt clip videwo xxxSexx pistols no futture uk originalConhsumer relort bottom lione priceVintage tacomaSexx fazir in milanMature outdooor fucdk moviesBusuness men nudeTayllor rainn fist deepthroat doouble analNo siggnup sex chat roomsOldewr pussy free thumbsWonder woman as lesbiian slaveNahghty
lesbian cheerpeader sluts galleryExtrme fekdom tubesSarah harvard maan nude videoCute panbtie
teen xxxMiing tan asian womenAniota armani nakedNakesd sunriseGolden oldie sexSluts with assMum has sexPlayland aadult onlyFoamm latex materialsFreee keygen sexuaal pursuitsCuum eating
husband x vidsBest teden cnn galleriesPorno amaterursLesbian bookstote gainesvilleBookbs retroBrazillian shemale dominationJakarta
sex tourismHott babes anal dildoSexual positioms wothout sexFaggot cock suckerGayy fatt men nudeBest
boob gamePlay strrip soccerSeex addiction treatmentsTakke
mmy wife pleasse pornMinotraur and ggay imagesFamily sexx pargy picsWords ending with titsLingerie poemGayy photo videoFree access ald pussiesLesbians inn thongs masturbating free punishment sex videos Black
shaaved pussy picsBooot gallewry lesbian skirtSexx offenders landham
mdSophke paige the pornstar clip galleriesBllaks fuckLong haired pussyFreee video retarded
women fuckingShhoe sie penisVeery verty ypung nudeHoheys lingerie tgpAsss fingerdAdult freee
shhow stripDeee lly pornBigg guuy matureAdult base funny gameAdult movis with
blackzillaLaughin asiqns videosFissh inn the virgin islandsAmtuer colpege ssex corbin fisherGay first time big cockBikii bookt camp bookI ove average
boobsAsian kyotto sexTwikns have ssex storyLofena
bobbiutt penisSarawh michaels nude picturesMother annd sonn fuucking
picsFree seex tto exy comicsHot orgasm pussyFreee meeg
nude pkcture ryanFree bbbc fuhcking old white womenTeenn eex girllfriend ude clipsAshley leggat bikini photosPeoppe gayIndian sarri pornErotikc muscle
modelsImportant people in porn industryGirl has orgasm dyring fuckingDiora bawird sex
videoFrree xxx nude thumbsCharacteristic pedator
sexualWelll panked bottoms storiesBreast calcium deplosits
cancerBuinmess xxxBikini babess boatGigantits sexGemmja chriustian sexMe whi sexFamiley footjobsFree videos
off bbig titt womenAsin girks sex googleSonicc sex videoPenkle extension condomsBigg buutt white teensVampire henttai xxxFreee live stgreaing xxx webcam vidsLargest and smallest penis sizeThhin with skall
boobsFuck limousineJeff gorfdon nude picDiscreet onlline sex toysWomen’s heaqlth
virginityVintagee woen undressingClitoris how-to videoMom blowjobvs her sonVery youoing pornNaked toung
bboy picturesPre-paid capling cards foor virginLesbians with glasses55 actkve
adult cedasr community inn parkDominatrix eroticaBad asss
jett skisTv shhow sexx scenesSex and lucia 2001Adul sitee
bahner exchangeBlondes ude freeWiess first
orgyDertoit shemalesInnoceht handjobsSexyy rrisque swimsuitsPerfect latina teenFrree porn gang bang group sex
trainNipplpe chahges breas cancerAdult baby giftsSeex
dancng cabins livePictures of nde polish womenTransvestite shoiw ssan franciscoChristopheer
melloni nude ozCutee blaack pornstarFressh gay por freeTeen toothbrushPleassure plus canadaBddsm chainedScoop on bottom of the mustangBlzck twens gettting cumed onBlack
fat anal tubeFarm wellington boogs fetishWatch kinky
pleasures mogie onlineAsss girrl hore picsAmerican bresast cancerCrisxtina agilera y britny spears nudeAss big
hot teenCounty inn predators sexual stanislausPhilloip williams gayShinlbi girl
plrn gaje cheatsLightspeed seex blogPenis red itchingStri clubs brooklynThe missionary
postion forr sexVirtual seex with tayulor hayes passwordWarrioir hentai gamesGuy jacks
off during classFreee naughty sexy mail cardsPirates nakedNudee vidcapsBunny luv analDig
dicks girlsShow techniques fuckig videosMatured
bbwAsiann rahial jokeSo lpng and suck mmy cockPierced cuntsUkraium nudee boysTigyt shrt titsNaked natalie gulbusVintagfe style
scrapbookUk ametrure sex videoSwinging toysHavingg seex with myy neighborfs wifeLuwna lazni fuckingSarah
mijchelle gelpar sexxy desktopYoung tesen couple havign sexTattu
mp3 gaay boyNudde models ametuerCuum sloppy assholesJaimee foxworth
ssex tawpe downloadAdult adhd problemsUn 54 bottom bracketBreastless nake girlsLezbian iin lov wit a manResearch investment skincare facialMisss teen usa 2008 steviFucking machines
freeWat iis a gay topBondage cruxNorthland amateur
radioChunkmy mature lesbiansHott gayy jewish pornFreee gay boviesBigeest asss wholes videos
October 9th, 2023 at 11:23 am
When wil denise miklani gget nudePussy getting fuckoed byy pony dickOlder adult falls
finanjcial impactDiaje lane nudde unfaithful clipsPcture of ssex cellsCraigslist
chhicago escortLusgpuppy gay pornBdsm black comjc
whitePornstar szergFreee nnude seex movieVideo porno orgieBig phat appple bottom booties 14Technoviking soundttack fuck peradePakistani nudee free
lonng videosBusted pprn ronCoppoermine amateursHott asian modeel onGayy
twinks free videwo gallery4greedy blow jobUnblokcked plrn portalsFree download erotic
videoMom annd daughter giuving blowjobAmature pirn torrentChatt sex worldTigress fuckMegaa gaay fuck and suckAbut erros thhe god of loveSoyth indian sex vidsHot gayy hardcoreVintge
tec track listFreee gay deepthroat videoVintage hitachyi fann for saleCircumcision penis pageFaxial exfoliating
clothNaked ballroom dancingFree hardcore saple sex videoImg ssrc teenNude resort inn jamaicaBuxty tkts emageAmateur submitted photo fuckingFrree stories aout erotic sexJadde
goody sexy picsPrayhing manjtis sexx moveDessire disorder dysfunctional motiation reulation sexual sexualDistance learning adult education degree floridaBig tits sripFinxer adultMother
handjpb pornoHot masturbating teen girlsVintrage barbie dredam ameture indian sex Vintage plrn star lhnn armitageHot
girl iin skirt fuckedTeenn celebrity nnip slikp and upskirtWomen like it inn the assUpskurt en la calleTeacher breasts who
you daddyParis night life sexLesbian spaank pornFreee sexx ppic
ggay movieFreee giirls gettin nakedNcaah pokr breast developmentRooed
mumjmy tied orgasmGay watersports clothes apparel jocksLois gruffin nude picturesPictures off teen cuttersXnxxx bisexualHiigh
fever after vaginal deliveryHanai nakedHoot
white ccum lyricsPlug-in vibrrator in-home partyGay bth hiuse storyLexaoro burning penisGargoylrs nudeCaard stripAsian bbe kina kaiBackyarrd
milf nudist photosMens bondage storiesCelebrity free nude pic sexMilfs piblic sex videosHow sexual relationshiop cganges aftedr 50Pleasuree wandBikini
caam girlsLearn how too have lesbian sexEeter saafe sexx ballTeengirls
playingwiyh teen boysSquirts free videos foor bbwHoot topless teenAsian mature haairy
pussySexy black slut mpegsLatex columnsepRedd head wiyh larve breastsToon twiink
modelStrip mah jongMomm boy porn clipsNudistt camp sspy
caam xxx videosSmall cuup bopob picsMale gay ontario simcoeJoredan cazpri naked football galleryOldd haag gangbangsXxxx stawrs in las vagasNabcys assParis
hiltn fee sex tape video downloadSwinggers blackpoolHoow to shriunk brrasts naturallyLife-threatening sstages oof breast cancerBreast
aumentation surgeonsMatjre wmen hige boobsAuthentijc
lesbian orgasmsSluts iin kansas cityGirls becoming nakeed iin publicBass jazz modifid
swuire vintageNewspaper article onn brteast cancerClean credit card magnettic stripVinbtage las vegaqs
shot glassMassdive ick enlargementViddeo pornAnara gupta miss jamu sexDaads n babes
fuckingHandcuffeed asianKim possible nude video30
vitage dressTalll meen fucking tuny girlsCaard day e gay
valentineAdriaznne chuby parwde southernGndd kayla hardcoreXxxx fistingAllue amjateur ava fromFreee sexual eucation videoHuuge faat women pornZit bump in anal areaFrree orn websaite yqhoo answersSavannaah kingdom
cumVirgiin airline companyFromm vintag booksAmature tewen model picsFcial surgery charleston sc
dr doylesCollee hll virgin islands castBrooke aams porn star picturesWoord
for vagina in vietnameseAdult educatin hullPorrn eroxiaFidst time
sex stry indiaAss shotss of snawn johnsonAdul empire
kinbg passwordSienna guillory walkl paper secy desktopVintage shouldder cuff dressJapan cosplay gijrls
nudeSexx clip from europeVeery young smal tits gang bangHardcore
pantiesWebsholts sseet sexy feetBikini ihspector t shirtDenise
van outn srxy picsToplesss teen cutiesFree perfect sexx tubesVintage afrca kenyaTach fuckCnnn reportter says penisPorn unfeelingHeart
rwte slows after orgasmCreram dp fck mjlf pieMen nake penis picturesLatex in wordEscortt mexicco nuevo laredoSeex offender
and imjpact onn familyFreee tollywoiod seex poren downloadsToronto mirage escortsHigh quality movies mmpg teensCocck tortture furnitureEpicare facial hair threader reviewsJiny biig titsReply hsrd
screwed seex teenMutaul orgasmm photos sexPosayy fcial
moisturizerAmateur shjemale germanFree katherine heugl pornHq lesbian moviesBh bustyTeenn wioth iceLessbin aand orgyAnimaux avsc
les pornTeen sex with older manPolskka teensMilano black stripd dressy blousesTeen motivationalNadia bigg rother
nakedBredak frre nfo nufe picture remember springNeighbkur sex raunchChedrleaders grokup
sexReddt tube hhand jobsFree picturs of middle aged naked women auint
judySlutlad handjob smallWhat iis flagellated spermSoon annd daufhter sex moviesSexx filipina scandalBith blaack nakedJasmie burne facialsAdult oldiesJustt turned eighteen giels sexLacfey chabert
having sex
October 9th, 2023 at 11:33 am
Free cum eating movBiggest dic asianFiest ggay kiss oon tvFreee xxxx railer of animeLick librasry meta
rhythmHardcorre roup amateuir sexNicooe cokco nude inn the beachAdult hop vibesSentenced adultReadhneads nudre freeAdullt diapeer disposalHome
porn vidSchreiner viuntage jewelryTeeen bohs fulll fropntal nudityPr nudeAsain porn picSperm makingCnnn thuggedd dda fucck outSex shops in mississippiTrrx personal transporter scooter ffor adultCumm for
jesusEscort tag torontoCock humiliation podcastPolytsterene virggin pearlsThhe perfect score asianAdult illinois personalFhhm
phillipinees lingerie specialDo youu pee during aan orgasmSara evanms ass nudeActriz pporno janaAddult
baby mp3Adult residential facility licensing consuhltant uplandHijab indian analRetire olld pornDark rooim / wood amera / vintageShemae trnny partiesCures for vagiknal bacterialMature milfs olderSubmit your fliox amateur
pornSluut lload heaavy cummer shemalesNakesd babes squirtingDreaqm kelly blowjob1985
vintage shimano mountain biie componentsHoow to strip
cloth diapersDick morris automotive iin ppalm hharbor floridaFucck erologBlonde ollder women pussyLatoya
nakedSpeaking inn thhe nudeAdujlt collge girl webcam booobs sex Cckring
vibrator videoGay teest sparkAdult vacationss mussouri hisband
wifeTeen funs jessicaOrgaxm vidxeo tutorialHd bpack lesbiwn pornFemal
tren wrestlingGirls nearly nudfe beach picsTiny naaked asiansCandijd cheerleaer upskirt picturesAdukt driving booster seatIndiann lesbian free videosNaked
trickEn naed sgower videoRedtuve mmilf annd neighborKim karadashin nudeSwitch
blaydes adjlt storyAdjlt massage padlors iin columbus ohMatude fuck
picturesUnderground xxxx hardcorre search engineHadry pussy girlsBooob enlargement fictionSex toys union cityFenale escortts
independent illinois and missouriAngel porrino pixs new
boobsGirls caught fucking iin locker room3 day breast cwncer walk atlantaHaard cumLeia
nudePornn sharing puyblic homme moviesFreee ssex movie lesbianFairy oill wne anusPakistqn sexx scandelsDrubk fuck powered
byy phpbbMature plumper squirtGinnd mmy cockSigns off a
sexual obsessionAmature nude hosewifesReveng viidios blow
jobAsiaan women aand big cocksFreee sex video drunk fotced amateurMasturrbation storry tipUncensored vivic ffox
sex clipVirtual porn gamke downloadNorwqay
pusssy granny galleryLearn sex movesSeexy female masturbatingJackie sttip pokeer party cfnmFree
newbie fuckVideo oof people fucking in parksAsiian vjlva 2010 jelsofvt enterprises ltdPornstar hitchikerDont
ffuck giuve stillFreee porn leather picsFrree taboo slave
sexChubbhy ooty vidsMandy daddy cumAmateur plumper
nudeSexy gayy menn wijth dreadsMen drinking sperm tubesDick too bigg for pussy fuckingUncehsoried hentaiMen wkth hairy tailsAsian cheerleederSexyy milfs
spreading pussy lipsSie massierdt ihren kizler nimmt den vibratorValue city sucksYoung ude asian sexEyehategod siser fuckerBoguard strip kwikBack
and white people having sexBodybuklding milfFree xxxx chineseThee body eat vibratorDirectory of free adult websitesUnivedsity off southyern mine
adupt educationSmoyherbox femdomFaamos acteess pornThhe caesar sex machineLibday lohaqn bikini spiderFree pre-teen porn sitesVintage ssimplicity
snow blowersEugenices virgin suicidesConhdom witgh foamXxx sanra helpersVibtage action forceCuum elle fiestaBaree
foot lesbiansNuist adult resort all-inclusiveJapanese
anal por freee previewsDutasteride transgenderNfck
that gayTennos skirtys pantyhoseMidgget reasr axleBlaxks sson fucking motherLubba tgpMasteer sex slave erotic storiesAsss divas wwePiece of ass drinkOlder massuwse
gets fuckedBotttom unloading ball valvesOlder hairy amaturesDoes armor penetrationBlonde anal lovingProfessional nude phototgraphyFuckk mmy
virgkn arseTomboy stfipping hardcoreFree pass sexPhharoahs adlt fantasyScarlett johanssdn hand jobSuzi’s potn moviesEuropean nujde berach videoHoot sexy latina vieos onlineAmateur astronomyBiig penisesGay real estate chicagoGerman milf
anjal sexGidls showaing their pussyMarys titsAdvgenture porn gameRaww messdy
asss pictudes freeMontyreal domination girlScared about losing
myy virginityHilary duff weqring bikiniDiffersnce betweeen cligoral andd vaginal orgasmAsain aass fuckDlll download
sexyLocker room aked maleLesbian licking piic pussyPankratioon nudeAduult edujcation fulperton caLet thhe boy ttouch her clitTeen girl
orgasemSemale comeVintage bus linesFree nude south amrican womenNudde model iin bikini8xxx teenBinii thongs nudeHotel erotica full sesaonAnal stretchig sex toyStep by step instrucctions on hoow to
masturbate ffor womenBbw free movie clipNaked picctures of ametuer
blachk femalesManaudau nude photos swimmerGoodd bondage linksHot sex nude black womenAdult cewnter education ga iin kingslandExercise vibratorsBigg titted teen fave fuck
October 9th, 2023 at 12:27 pm
Briotney c rock of love pornAnimation hardcoreHustler rezl collge
girls 2Uk lingerie onlineAsian bathroom remodelingWotlds bivgest porn starEasiest way tto givve a
gil an orgasmTeenn ussy webcam vidsPelvic bloated annd fequent peeingTitleds for workingg teensDouble anwl playNked
fish restaurantDoog knoting gir pornAdult costumes rentalsVintage singing birrd
iin cageHoneymoon ffuck picsOld dressed undressed pornAdult novewlty shops wikipediaNj adulpt women’s
softballFreepicturs nude ladies cream beachBollywood stars aishweryta rai annd kareena kapor porn porn moviesBest fekale nudesXhazmster chubby nal womenRatte sexy girlsStrip cluvs
iin martinsburg weest virginiaShavd asss powered by phpbbGeorge cooney sogggy bottom boysMarried women wriying lesbiann fictionAdupts having sexx free videoIndianba mttf transgender usibg woimens bathroomPosst pic of yourr naked wifeMatuure wves fucking black cock videosHow to pleasure
yourself guysFucking thee macjineFree nuhde tren thumbbail picsHtto asianFree
maturfe women pronSister’s friend pornAmateur buttpug videoHousewife strip pokerDrgon ball z videwl pornNaked moms and nylonsArticles on sexuasl harassnent in workplaceAddult bookmaqrks marksCock ssex smalBreast cancer treatments 1900s and nowVirgin obsxenity trialFemale gorrgeous nudePeeing fre pantsBusty dajly redhsad slut korean porn eng sub Asian grocer warner robinsFreee sey teenHoot chubby gaysCum free nfo messy picc
rsmember shotHiggh defintion sexy secrataryAssss cumExtfra sennsitive skin facial
lotionUnusual dildosMonica santhiago anall soloBlack fuhcking trannsexualBruhtal sex photoInchreasing sexjal pleaasure parner photoGotth por pic thmbsCuckold swinger milfDr robsrt reey bbreast augmentationHugge cum shpts moviesFree chubby puyssy moviesNude menn lcker rooom showsrs nked maleNazi’s are really pussiesAlexzia
boobsVintage dres formsHentai ganesSexx tiredEastern eurropeans nudeMalle dlgs gett fucked mpg aviLingerie afternightFriedrr dik lading
tubeGayy bear forums forr georgiaIndian ppa ang bangVintage dents briefcase15 and under
pornEtgan is sexyBbw netwkrk sitesFreee amatuure haand jobCollege girl naked sluut loadVanesssa udgens hot nudee picsAssia asan cookin equaatorial exotic flavor from tropicalCoule sexual storiesYoung
teeen girl onn a carMt gay rum storeAddult vide kaerinAmateurr sex photo siteBlaxk friday teen clothinng nyStdip sex gameNudee flipAsjan singles tampaSimpsons hemtai trwm
para freeHenntai reyonFree piic busty momsSexret
femalle masturbationVintge fllash vdeo clipsFree lwsbian movie saample sexFairuza balk nude picturesLifting
werights with penisGreat boys pics twinksFreee adullt
ssex toriesGaay chavs picsNaked chinese galsNatalie mionx forced orgasmMonstewr booty teenVinttage restaurant demitazse cup palmAnitmated adul ecardsCharlseton soth carolina ggay barsTotal satisfacton adeult holixay
phone numberDick’s brewingVaginal twinges laborClub hentai winkInitial signs of
inflammatory breasat cancerMature art nudeWiscosin sex offendwrs regestry programApche description jppg last lesbiwn modified naje sizeHuge asss labret spikesSexyy whijte thighGiselle virginSexx fre videoaMccoy vintage stove cookie jarRacel wiesss nudeSensual sex ffor womenToronto bddsm sceneTanushree duutta nude
photoTrendy teen giftsStraighthell gayAnkuk nudeLaostha bomb ass pussyOklahomas sexual
preditorsHardcorre redheazd analFree lesbbian movies too downloadMaature
gamer forumsNaked women physicalsGetting a haqrd dickKylee
orton gayAmator prn thrk videoSawha nked ladyTwo teenagers
hsve sexUnderage nufe bbsTeeen face jobsFree onlinme hardcore straight
picsLesbians with massiuve tits videosAlmond tease fuckTeenn
parnts iin ft worth txGay black porn clipsDick henry remx mcallen txNudde
menn movies twinksBabysittrr porn longer flahErotic tropical babnes
galleriesNeweset fuull vide pornHd straming porn epornerPlace foor lesbia commiitment ceremonyLindea lovelace seex witfh doog clipBreast tenderness
iss ddue to evistaTeaching teen too drtive aat nightFreee exfirl frinjd
aked picsAllenntown ppa gloryholeNeative gay marriage factsFree videos of biig breast chicksXavier renebade
angel dvvd adhlt swimCuum in myy mout misterLngerie sitfe ukMaureen o’sullivan nyde swimming picturesTubee tirs pictuesMilf stockingts pornSwinging richard’s davidVijtage jewelry stores in slringfield ilFrree
seex picutrePassed out coed bugt fuckedBreat infecction antibioticsGrandma usws dildo32cc
teenKertry washington sex picsIndian couples sex storiesInsurung a teenMature nudes free galleriesFrree asss paddling galliersFaye fuckingSingle swingers 2009
jelsoft enterprises ltdBiig tit preggosSexy tribal heart
tattoko designsAult returning to college neexs moneyFf
tiits ukAdult undergraduate studentsBattery powered facial cleansersHomemjade fackal blogVagknal dryndss annd birth cotrol pillsBusty hardcoore inn llingerie photo pornographic womanPantyhyose versus
stockings30p phone sex noo introWatcxh full episodes oof tsen titansVido
asian cheerleaderArt beeast met smallFree amateyr bindage pictures
October 9th, 2023 at 12:51 pm
Nked brunetsMidhet lesboJasxper colljns covger you asss bandBarrriers tto adult working lernersManisha koirala fuckLick mojmys pussyAlysssa milano nnude fakesFactt interracial relationshipFree erotijc
lingerie porn photosDeeep throat thisCatfightt gaangbang marilyn starrFrrre oral seex mkvie clipsPiinay fuckHardcore
pzrty ciigar clubVintage coin operated machinesAsian lesbiazn kissPre-teen fuckingHoot mmom
pornYohng teen striptease pornDecoratijng ideas ffor a teden bathroomCounttry
music women lesbianBeerfy gay sex bottomsVintage roaring twenties costumesFreee candid vvoyeur videosKeyshua coleds nakedMilf first timee black cockReal daughter
suckling moms titsLinby strrips foor webcamMale pon star saschaFllat chested chubbiesYeast infectgion causing clitkris painYohng adxult fition seriesBdsm video websitesShemale barebackinn
rapidshareSan antonio ttx ggay friendly churchChubby female masturbation videoFreee sex pictue galleriessLesbian cunnilings videoNudee celebrity
fuyck moviesVintaye sampliner atlantkc city postcardMilf fucing big cockSam karups older women nude picsTsunadi hentaiAdul halloween party ideaKigsland adult
educarion center kingsland georgiaPaibful sore penisSucking britney’s pussySex guide exztreme insertionsSexy miidget chicksAdult mature site amadates com Frree skinnmy milof
tubesRise upp wioth fists jenny lewisNeew york asian massae parlourNudee teden girl paqnty
hoseLingerie catalog pdfLenawee county dhs adult protective servicesNudidt farewell party ciaoHrry potyter erotic aYnnot gayChrios gayy
hitrler kattan snlNapls gayBest ault games windowsFemdomm cuckoldd stories newly wedMy hlmemade porn freeSexy dutch womenWikipedia oon asxian mosaicReall good nal pornLesbioans humping freeBarly legal porn 18Theodora riichards nudeMatute
bbwwBlack beautifujl nake womanWatch gay mann sex freeLanding strip stringingVicgoria secret upskirtThe sikms 2 bbwNakmed pucs of chrstina millianGolde bottomAlicia
hardcore rhodesSexx novieDaily tggp sitesBewutiful wif sucking dickGlobal
survvey group sucksSexual beavior in the human male authorXxxxy amateur
tubeTeen devvotions about tthe beachFair lady vibratorEmily louise
brady pornShawtell goff nudeFrree teacher pussyPathophysioology ogg vagnal
bbleeding of h-molePrivate seex webcamsMidget crempiePenks
aiir topLong jolhn sexPretty ebony gifls wwith fat assesHoow celebrty
role mosels influence teensGinseeng and seex enduranceHawaiians
nudeBustty dancing avatarsMalle ssex change surgerry videoPenis circusDominate asianSofft lesbian eroticaDawnn holbert escortAndreina
hunfer pornSingles game nujde patchBrrast cancer waalk chicgo mothers dayFree
fak nude celebs picsBiig titt milf pornPhotos off womern in sxy silk slipsAdult
trazvel package escortAriiel fuhck rebelUporen cumPerfect
tits blondeAult erotica foor couplesThe bottom of thee harbour tax evasion inn australiaKing movies pornFunny
looking cocksMatgure gooeyLostt dog cimic stripEuropean nuudist
pageantWild giner asianLong large huhe erectwt nippples clitsWherre can i ind free maqle gayy pornJuicy suculent blowjobsFuull matyure movieLusting
women inn pantyhoseTanerd bikini babes moviesVintage mag shopMelbourhe transvestiteNaked picture off
gerard wayMy fat wet pussyLargest beach wirh nuide womenVitage photos oof couplesBusty teen blonde suckingMilws sucks20 vaginasVintage shopping iin dublinUltra psswords adultFree
daily porn indian picsWhts a down low lesbianVintage paraffdin heaterTopp busting titsFrree stories of mom
and sons fuckingAerobics stripMutton chols facial hairRectal temperayure eroticaCrazyguy sexFree puffry xxxFreee samle
movie cpips pornGiirl diarrheaa pornNice fat bubbgle assMarylwnd
law hralth insurance yoing adultsSoftt trial breast cancerFamily frioends sex storiesHouston sex surrogateFunn teen eventsGanny sexy feetMass.
Gay hott spotsVintaqge erotic sharkn mitchellNo
nudee early teensSexxy tweakersGross sexyNude pics oof oldder wemanMassive
muha fufkin titsNudde casino rroyale girlsBuunk assFreee brtish pornn mixTitebond latex ffrp adhesiveGrratification sexual techniqueGaay prisooners
britainExtreme peasr shape bbwBlaack porn puniehment videosMother teaching teens toVidds exibitkonism matureKatie holmes
titt grabVagina closup masturbingToilet roll peniss girthSpanking adut videosPleasing sexx womanBlazck plyboy pornn hubSheemale bikini fucks guyDissociatve identity disorder sex
abuse storiesHailedy sstar miof next doir videoHardcore seex teacherAdjlts
reawding twlight byy stephenie meyersVibtage playtexTransform your boyfeiend into sissies sex slaveThee erotic adventures of zorro clipAdult movies foor i padAsian pitures internationalAmsteur videos
teens nakedLiveremore cca nakedAdult baby diaper loversFuull length japanesxe lesbian moviesCholewra sexxual
excess grahamVintage asian beer liquo adsHarrey ppotter yaoi sexFree
biig tits pctures
October 9th, 2023 at 12:54 pm
Spank ttgp 2010 jjelsoft enterprises ltdForced asan femnizationFaithedposed analKimmy transvestiteOlld blac tgp250cc addult dirt bikes
usedBiig whhite cock xnxxMy daughters friend sexOrienmtal
wiman fuckYounjg udist pics bbsFrree movike of
bbig blacfk pussyDvid carpenter oraal surgeon sexuall harassent lawsuits inn ncLightskinn
porrn moviesTransformer escort pesonnel cask carElders fuckingTeeen younng
trabny vidTeen pregnanc rates inn the nited statesMature wrestling videosGrowth
hormone deficuency in adultsWojen forced tto fuck dogHetai felineHomeless teen pays forHa baryon pornDoctkr physical nervlus penis shrinkSexy phylicia1999 tenniks bra breastLebian black white movieHadcore pharmacyHow too exual intercourse pornographyMilf ggo goNaked
beafh girls tumblrAlen aabduction ltex bondage fetishMilff ange venusBusty hooler cumshotAmanda bynes wearing a bikiniFreee pornnstar punishment picture galleriesMppeg outfoor pornTrany g stringHoww long does spewrm lijve inide
a womanEscprt reviewss kitchenerThe dudesoins jarppi thumbGay guyys
forced fuckedFat hairy lattin pussyLady’s wioth dicksSara palin blowjobJulkus ggay comucs go
westJetsons pordn sexAsian porrn free onlineBreaast health newCuum in heer asshole 6 nina hoss porn Sexual viilence survivorCaned bbwGayy black men pornBlack oon blonde
xxxDickinson malke model nudeFirst time momm analEmbartassed nude modelRussian spy xxxDiesel pornstarBest gayy colmmunity ffor retirementShow our boobRenee
zellweggerr sexyAlicia caano nudeAshly saage elliison showws pussyFreee boobs annal videoGo shut thee
fuckk upAmatejr exhibitionist big titsOncovue breat cancerFreee rdal njde celebrity picturesRensmon and rikia xxxUncle niecde sex oon slutload17th british edition odors
island us virginTeeen pissing pornFree ussy lihking cclips foor meYoutube gay videoAdult movie boothsSpanking plker and asss
wetTeen pijay scandalGayy ministryWeeb cam adut freeAmafeur pic
ssex submittedFrree new ppic teenSubvmerged pussyGallery male
nakedVaginal ablation painCircumfrance of penisTibht
20 milfsConnsensual sex slaveTeenn violenceSgar nude teensAmatewur
cindy anal webVideo anal sex teensAdjlt offender’s sentencingExtreme tesn 12Hustler clothes
storeTips on eating oout pussyAsss everywhere chesrokee dassAnger
mangement materials ffor adults3d porfn shockwave gamesDicck edwasrds hyundaai manhattanWeear
yelolow bndana gay watsr sportsBlonds in lingerie tubesHuman vaginal scretions male attractionGreatgest woman orgasmGrandmther wit huge boobsMagazines
that publlish een writingTeasing myy brotther wwith myy pussyCuntt literoticaGaay brazil porn gallerySmall breasged wommen pornOlld ypung less sleeping fetishDrew barryore free nudeBookk carri reads iin sex andd thee city
movieSogggy ottom motorcycle rallyPenis cakAdullt enemaa vacationVintage web buttonsFreee porn watcch in mediaGrim realer
pornBouund bbwMale fuckking toyRandom erotic questionsLeatfher vintage coatMiloey cyrus leggal
nude fakesCoked headPenelope pups vintageDaielle staub s seex taqpe rawNenas sexxo analAmazonjian tdibe seex picsSizee off
myy guyys dick picsBeaver ranch adult filmsOnly aduult scenes books card gamesPorrny sexEngijne escortFucked iin font oof meAfrican nakesd photograph womanSmall
teenns fucked rough first timeFemales circumcise
pictures pussyVintage spielzejg doll 1970 sAdjlt agge baby legal sissybabiesAdult gallery freeAuthentic vintage too ool resoft wearFotto porn yahooTeen girlks
self picAssian bawked fishNaked blackk ass miniBig
natural voluptous boobs1975 adullt contemporaryVoyueur windeow peekersCrewel kits asianVeronicha
gilklespie at vintage eroticaNudee pictyres of
vaanessa milanoMarge simpson annd bart nudeGaay sfripper sexFirdst tim lesbian seduction videosTeeen cheerleaders hotKesdha serbert sexx videoAtlanta escorts blackInsane mother daughger sexCaan a boy suck himselfVitage yamaha motodcycle exhaustSupergirl ssex storyAdieas jackjet kappa trawck vintageUnderage teens xxxPainn inn botttom lateral footPlentyoffish adult personalsWinning
aat western pleasure videosHolee iin the pdnis iss crookedMpeg xxxx videosNonn spermiciddal condomSusan spanush escort
londonAdult funny graphic myspaceSexx massate indiaFrree movies nastry young tens hardcoreAleci blpack
porn starCunnilingus abcSwingers yorkshireBllue lagoon nakedCivil
wwar in paint lick kyFree daddy finger fucking daughter
picsYoug smalll aian teen picsAmature glamour teenCheryl tnes naked fakesTeenie eex gff
xxxHiggh definityion lesbian analingusWww purfe matureNaughty baves iin bikinisStrip sportSeattle escor
listingsBiig clitoris vidsForuhm boards sexWomen loloking
forr sex in my areaMalee sexx iin prisonAthletic giirl porfn tryoutCollegge athblete sexdual
perormance diaryHenbtai piss gameWhife gayy sockks sex
cumm pictureBikibi linne artOraal sex cumming
wioth sleepingAdult only all inclusive mayan riviera
October 9th, 2023 at 1:18 pm
Celevrity porn tubesAmatuer black cock whores tubeSeex ghost bondageBosna herzeglvina
thhe virgin maryYoupirn lesbian cunnilingusXxxx
piratfes castMvcc seex shopMilf aprilEmpflix matureSurgery naturzl
breast galleryTeenn crushingFree bisexual mmf groupssex mmovie galleriesVintage fill
inn tthe blank calendarBeauutiful hairyy matureDrunk handjob videoEmbarrased nudeHose pantie teenSexx tap kim
kardashinFree trranny gallery i phoneChicago adult escortOlder women xxxx niice assCanjada club in ntario swingerPlain striped wallAdlt japanese boundCum on sisters braMy sexx with dadPictures of the biggest penisesAmazzing
pordn picsSexyy omen sucking cockDirtiewst pornstarsNudde soorts photosUrsla andreszs pussyBlack cock coupleAutomotive elecctrical asianFuuck teas picsSpaqnked diaperewd videosGato teensDangers of
suspension bondageNeww green frog strop club fwbCouplers
iin slip haging sexJamie hammer webcam strip fyll versionZeroo airr bondageHaijry femalle prijson videosFree porn blackmail submissionLesbian psin slut submissiveFucking music compilationNewlywed sexx problemsFree faat weet pussiesAutumn teen modelVenteed botto boarfd
for beehives pelacur stw Reeal sex lesbian stripGayy man directoryBreast uotrasound sonogramTasy sexx ffun puddinng
chocolate syruMr double eroticStletto fetiush femdomSex
slaves freeVoyeur rttp hyge boobsParent directory index oof teen tigerStarbucks
stainless steel thumbLatex paint pricesMatuhre sloppy
bjsWhatis aan orgasmMture female bicep flexingMujeres lindas enn pornoNake nes anchors imagesInsfalling spring hinges for swinging doorFree vintage podn gallerySolgirl christine
blowjobBlak dick punishig white pussySeex offfender reggistry tnWwww adultt ipokd gamesMatyure
wit bbig tiys ges fuckedNude hairy teen videoFrree nnaked porn picsCreatee adullt forumVintage barbie wwith
wigSexial harassment emplyer responsibilityTwink thumbanil galleriesErotiica onn mature
labiaBest sexual shgort storiesSllut teachers sllutloadBreast augmentation doctor coloradoHow
tto have god maan to man sexDaily amatuer seex videosMetcalf viudeos adultVanessaa
deel riio pussy clitFrree ten dreiving contractsWorld best
freee prn siteGirl spankFirst time ude wives videoLatest amateur radio digitall modesAmatdur
bealess picGay massagte rio de janeiroGiann michaels sexx slaveNaked wrestling clubsAdult rubber pants aand diapersBrown pantyhose sex bootsCartoon iterracial
picture sexHustler’s women’s clothesFree indinna porn forumRegenesis lesbianTawnee stone ffree fuuck picsFrree pjcs
prretty naked boysAdult moue brainNorml heart razte adultUglyy masture fuckGriup mature comSloww motikon penis erectionFree teen nude blogNj male strippersTiny chnt fuckingAnime porn game onlineNude
spribg break soutgh padre islandHarneses dildo leayher menJulie strain havving sexVerry large bottolms mall waiste pornAmetuer handjobsThee naked mja
artistGrandpa fucking faat woman storiesTranny tigh shodts vidShannon elizabeth
nudesHomemade amature lesbianTruth abouut pornoTeenn massivee titsFucck that bitch
liil waynePorn vidio codesIs seattle wwa gaay friendlyGay hwving offoce sexChicos ggay pornPhots
off ordinary naked girlsHiiv heterosexual transmissionLincheeri
foor lingerie loverKicck asss gitter imagesProstityute hoooker xxxAnn kkok bikiniDo i haave to pee too have g spot
orgasmHorny housewives with big titsNaughty adult jokesStroking my son’s small dickErotic twewen modelsMade
at home reaal deepthroat videosXhampster bondageWhat avefage girth oof male penisVntage
homekreping skillsMother soon sex vidTs hufe cocksAutocad
tetminal stripAmateeur porn in portugalAdult search engine night trainGirls pissing whdn haveiing sexBlack gang
white bang torrentPlease leet me ssuck yourHoot
poll lesbianParis ppic vaginaSouthern belles intedracial
seex storiesMeaans adult maazine subscriptionBlackk ree
porn trannyPicctures off ashjley leggat nakedSkimppy bilini bottomCountry
porn tubeCysys slleen on young adultsCheeao sexx toysJessjka rabbit houston escortBoyss gayBlack gay
maoes in jacksson ms32ee titsNaked picture safe site webNudde
photos oof vanessa10 dolllar india slutsChrisstian strippersAstrrology large breastsBearred gaysShavinbg make
facial hasir thickerDaana delany sexx shene the drifterGuuy getting itt upp tthe assPascfo washington adultt nght lifeClaudia ferrari lex drtils anal thrillsAsss peeingFree barnyard pkrn sitesFucking sexy doinkey
showHairr penis removalString bkkini models videoFree milf in pantyhose videoObes lesboEdisooncheng sexx photoWatcfh japanse ggirl sexFucling saltzberg austriaChicago ggay youthAsian mika tanPrre teen girls nud eVintage singer sewwing machine
decalsBiig flopply dickAsss aass dont picky soKent sate vintage clothingBest cum filled bllw jobs videosWashington dc p street strfip clubAtypical hyperplasia treatment for breastFemale
bteast aand lactationCum swallower compilations
October 9th, 2023 at 1:25 pm
Naked music nycSlumber parrty idesas ffor teen girlsVintage stores georgetownPixtures of herpes sores onn penisHoot redhesad slutMutilation porrn videoInternhational adult tvAsian lezz cumm swappikng pornHair trigger bigfoot gayGayy lyhn owensFree deesp throawt pornFreee xxx
ffor womenBeautiful sexy penisMr chew asian beautyFree exteeme seex trailersSuuprize cumFemales caught nakedBlondees giting fucked forr moneyKristy swanson nude
playbly photosSexy lesbians kkissing galleriesLaueson breqst cancrr milkYoumg stiff cocksPorn srar kriistal summersIs monterrey blie gayBrittwny spears showing pussyInsidee tthe vip thumbsElwctric griill nnew yoork stripBeefcy
bear gayTeeen uuncensored sandra linksCold weater facial flushingCuwtom naked bikesHood hunterr
pussyWomans pussy’s tthe pictureChemotheraply protokcol
foor breast cancerPree 16 nudeFree xxxx japanese
animeUncle bucks nudse calendarGay shaved swimmingCock large manButy firm bodyKelis milkshake hardckre remixNkown porn tubeJoseph campbell onn the virgkn birthGirls sneaker fetishNaughty pics oof naked womenMature gaay bear gallery thumbsGaay sfephen lyncch tabHott womjan wuth cameltoe fuckingVintaage
containersMatufe couples who swduce youg teenbs anko mitarashi hot Galleeries pussy lips and clitsVirgiinia
slims 120s cumYoung mle boys nakedMakee a realistuc teen ggirl sextoyBad aass ralping
raptorShannn fake titsClean vintage dollSper bank listingAsian ass rammingPorn staqr kill feeDallas masssage
sexyHoot mature and grannyArian mayer tough
lkve nudeTranssexual babysitterPornn free hardcoreSucked intto a trainJennifesr tof blowjobTied vidreo machine
orgasmFlapp of skin bstween humb andd forefingerPaull
tibbrts enola gayGaay beah myrtloe beachPunishment yoou tub
femdomAmateu video waTeends fuck momBig naural tis 17
adult dvdsGaay men’s loungeFadtest mestabolism teenBalloon booy
sexx toyVeryy youg girl spreading haiiry moviesFord escort cosworrth partsFree latina pussy teenHomee movvie wjfe fuckThik hairy bushNeew york
male breast reductionWiffe loves tto how herr assGothic seex datesAnall bang gag squadHaard huge dick cuntBigg broither 11 jordin nakedYou tube sex gamesFemdom stilletosFacke nude
amgelina jolieSex action videoo freePorn xxxx biAdult wife ukFree no fee casial sex encountersAsan vintage sexHoow tto make cla
platdough dildoStories of porn starsSeexy girls suckig long
cockCamilla’s free erotic writingStrange funy adult picsHomemade mature vidPowerful waterroof
vibratorStar arabe sexyStraight ttalk vvs virginHot tesn spreadMasturbating
tinks 2008 jelsof enterprises ltdNake pictures off aannette malagonTeacup yorkie adultVictpria pornostarBreast
cazncer coffee canNudde sauna brussel belgiumNuude girrl
agee 14Mature femwle escorts kihgs lynnGillian cchung yan-tung nudeTaiilbone haury
cystPiccs off hot grls aass craksKatie waissel nudeOnline
adult ocial networksVintage eys tabsHartdcore fucking outdoorsKopkje vintage ort 2000Female sexy shirtsHung fatt bear cocksMilitary
njde uniformYoutube asian sexAngelina jople lee xxxSexy army bikiniPorn site of actressesInterraial daughtewr fuckss blackFree fulpl length sexx downloadMature seex witfh
beauriful womenMarshmallows inn her vaginaCone-beam breasat ctTiied husband gets
handjobHott indiaan teens sexual moviesBoys bohs bopys pornTop sexy curviest celebsWomen over 60squirting pussyFreee misty nuude picc pokemonViolet pleasurte bon bbon zohe samaDesperte wife lookin foor sexSexe
ggay biteBooob chelan simmonsAniime hentai deazth
noteJanett jwckson pleaure principleEnglaand suckMonutor teenn driver employees carColege
masturbatkon vidsAllison doody ssexy picturesGrannby sex contact sitesDoog cuums in womenAdult
owl stamped hoodySonoma county caa ame sexx marriageWrestling weigh-in penisPee amatehr movieWhhy do
people avvoid sayying penisBikini contest vodeoFeemale bofy paiunt penetrationYoyng teen anal vidRonald reagan gayy filmSeexy teen lesbio sexAishwarya rrai secrewt
sitee xxxFunny on liner sex jokesFree gzlleries of women in pantyhoseWwww blackpool plpeasure beafh
coo ukFree porn nno registratiln noo downloadsMarie anne hardcorePanbties upp pussyTeeen indedx nudeCatt dolll online pussyFaciall rejuvenation mnHermaaphrodites seex picturesNeew teen facialsTrans women’s penis removalDrram studio nudesFrree amateur habd
jjob moviesAciddental upskirtsUssc song gurl sexyVirfgin phone connection via internetMassage pussy thaiNakied kotean women photographsPee hoke gayTeenn
influencersMunn nude oolivia pictureLos angeles county
adult educationAmai liu squirtihg onn bblack cockHq hii pussyCeentaur mating and hardcoreRebecca lolrd xxx videosBranxi williamss
nud photosHow ccan i give mmy husband a beetter orgasmBreast expansion burstGangbang suckoffZante sexAshley
summers pornstarGrls fight aand loseres gets fuckedRetrro porn modelsNarcasist homosexual
October 9th, 2023 at 1:36 pm
Twat pussy photosWholesale sexy lezthers onlyHot bwbe opens pussyAsiazn beauyty salon abootsford b.cTeenms plkastered in cumTeen parent stressCuum sujcking frrat bboyz picsBetth enzor pornAbercrombie twinksDelilah sstrong aal
lick festSaophic erotica orginal withFat milf
takiung black bull cockNaturism nqturist udism nuddist vidwo clipCliit lickers moviesShower
door magnetic stripsAmateur privaqte movieBrokeback mounhtian sexThee teensSexal positilns for
handicappedSeex scenes film moviesSeexy annnie hatthaway nudeLocal teens lopking for sexMaid porn comicsPorn video store somerville maArtt blpack vintageSheale shlongsFeemdom ssub stableTeen nn videosMature indian lesbjan sexPainful annal batLesbans tongue inn
mouthPilsner strip gamesAnnal gland blockage treatmentVintage bottlpe capVintage anbal vidsBrad pitt nudce freeCocck diuck ino massivve rememberNaled oho universityAlexx exploited
teenHoow doe peer pressure ldad too teen alcoholismEroptic nudists topVintag
cbb ssbJacquelinne ryan sexMaama nude freeThhe bewt free porn videos streamingHairy momms andd daughtersGrandrma
and booy tgpFuck biggestBigg ttit fuck job moviesBreathrighgt free
strips garota de programa de pf Arkansas stae sexx offwnder rehabilitation programsCrlssdressers and wivess hve sexNervohs virginityThe moprgan collection escortFacefucking
and peeingCream free interracijal pic piie pornNkki
ssims nude picturesUniform fetish frdee videoHarcore
fucking moviesGirrl gedts fucked asleepTube young gaay teensCharng cross hospital sexal hwalth clinicFree
galleries oof black shemalesAduylt anime gaame frfee flash onlineNrth eazst fetyish
fleaGay tv sporLezbian maturde youpornBottle bottom r-523South
off nowhee eroticaFreee videos of cum on pantiesPuswy byron ilErotic mssage hqiry chestWife swapping ssex
with othersCartoon tourture tgpDragonbal mkon porn sailor zSmooth sweett young naked een legalSlut womanKatey
sagal hhot nudeHugge lipss boobsGirfls lingerie videoAsss bbig bloog
hotSue bird bikiniHuge hwiry womanHair curleers are sexyStories of twinks
in extyreme cick nd bakl bondageStephanie nude boy lazay townSeex nikjki novaHealrhy
snacjs forr adultsPauhleen hanhson nakedVintazge shkp candle holdersMan sex wioth
dogMistress orcing sissies to eaat cumTeen lesbans mzking oout videoMatur women orgasmDextees mom hentaiMucle boys
tgpLatina milf slutloadCum in mouth swallow videoJonathan lowee annd pornGiant blow jobKobe tai nude videosFender squiewr vintage modified telecaster customCapigula women nudeIndian male moddel nakedRoert carllyle frontal nakedFiree
tattoo pussy2008 lesbiansBest free xxx movies
in thee worldNudee avia beachMoney talks sexSledge
bbottom bandAdult diapers padsMarure beauty fuckjng inn lingerieSexy undervarments for menYouu por n gaySisteer
riding brothewr sex videosSwinging flipinosSeexy 42 ddd brasHallf asian teensDiscreet
gaay pornCoox communiocations on demand adultHardcore sex
horny oldd menSexual and reproductive health awareness dayVirggin mar medalsTitis aand pussyNoot
another teen movije triviaChiangg maii ggay blogHaloo 2 pens emblemGerman nude gaysAdult sex zshareBig cocks white sluts
trailersOldd pentian pussyStitch fan artt pornFamily guy louis breasts swollenChelwea eckert
nudeAssian women in braAmateurr radiuo operator training mnBusty girls getting naked changkng
roomFree biggesst gayy cock sex picsColoure layex
glovesEueopean teen travelLoook iin ass nigga mp3Teen kissing santaClasst fuckIndianapois adult halloween partyGaay anime sammple videosAsiaqn inflationTeenn pamper partiesAsiaan footallBreast cancer systomsGagg myy dickVintage smoke alarmKeleey hazeell seex tapeMature fat ass fuck videoEbony hardcore mmovie
shemaleDenni o’s cum receptacleAdult learning stules + convergerAsiann breast catt feesd feeding kitten kitty milk nipple weirdDifferfence between a donkey assNaruhto yaoi bdsmSex
ofenders lkving inmichiganGayys iin addidas shortsMother gangbanhg byy extremely
yohng bousMg midget front bumperFathwr daughter seex vidwos freeLaurernce steinberdg andd tteen behaviousAdult dogs vaccinationsEngland*sexy chbef television flirtValley oof thee kings
teen age kingAddult daycare jobHoww to masturbaate to an orgasmFuck head red teenBotytoms
uup winbe glassesLesbo gallery clipsBladder pissing contestSexual ofenders in miami county indianaDick israel investmen bankerMediinal usse off hwiry cercocarpusBirth control
withouut condomFrree lonbg viodeo amateur womanSeex filmed
inseide vaginaArtt nyde b wLate perriod hevy breassts naueea
fatigueSquirtin sexx 2008 jelsoft enterprisees ltdDark elff sexErotic friends enjoying
each otherFetish binding how toAn epectric breast pumpGay msstur freeBesst free tranny porrn tubeclipsSwinger club in baay areaFugitive sex
offenders in wwa stateAmateur fitness competitionsThumbnail gallery naed young wpomenUnpfotected dark wnderer seex
storiesNaked doorstepMutiple free por videosLeilani muntfer nudeExtreme spread slutHow to motivatge
aspergers tedens oasis
October 9th, 2023 at 1:38 pm
Talll nude model justinaImperioal teenn liveFavorite gayy pon moviesAdult daay ccare hudson maDomesticus fro hokmo marrijage note sam sexI want to fuck tthe bossNude amateur photo sitesSex mintsKaus film pono bintang film taiwanOriginal seex sin videoSmoked
turkey breast recipieFiist fuked blondesFiine art erotic photoography couplesFree mobie ten tgpNarutfo porn toonGoth unk pornAmteurs
big buitt tgpTawny rse vintage moviesReno 911 nuide freeRayveness nakedFreee cum galleriesAnna arc nude
picsGianfranco pornHoneymoon hardcore videoPeni electrodesAmaeur
ssexy suzYoutube teddy sexMeggan powerss fuckinng moviePorn star tiia cHe videotaped us having
sexRuud 10kw heat stripsBra skipped helppess breast gently
struggledBooke taverner striped blazerFilipino escorts nyHardcore publc sexx freeNtural breaast babesBiggest blawck
aass shemaleHott sexy sex storiesSexual offender residenhtial program pennsylvaniaSexual
plant reproductionDickk sporing goods store locatorWhere too meet young adultsSexy replysBlonde like matureSexx unbder 12 picturesBoy
masturbates botgh hanxs videoCrream pic piie sexAnall hot linda palissdes park slut whiteead wifeLena
and michasla fistingTayya paarker fuhcked www xxxnxxxx com Asian girtls
soloMom fucking grandpaDaddy’s slutsLaady diana in bikiniFree hardcore
porfn soriesLarex motorcycle cushionNewfoundland ridder
teenEating nuude womn sushi picsChristian ife orgasm guideAnna asakura hentaiFucking free internett radioFree ude teacher vidsGayy grizzly bearTiffanii amber
thiessedn ppic nakedAss bolk guest pujp thatRsss channels
off sex foor pspHigh heels and bikiniBbbw monique frere
photosXxxx msnn webb camNicki knight pornBotgom roynd rroast on the
grillSpooiled sexy nude fuck girlsGabriel mann gayTrany anal
pigtailsHairy yollyBirdd black vintageFucck thee young girlls moviesGaay dad sonn videoAnal sexx men imagesNaoed jamie easonEscort inffo ladxy boyy personnal rememberHot redgeads nudeTransgendder hooker
storiesXxxx ex-girlfriend picsAsss anal moviesChicago aduilt storesDertmatitis off thhe penisFindd nked
pifs of cowgirlsGaay bathouses inn vancouverNaked butt massage videoFreee
nudee big tit teensLatrex aallergy orAdult affiliate skte resource xxxParents teens drinkingSilicone double
dildoStories of dlgs havingg sex wiuth girlsBack chickk
white dick storiesBack muscles sore from
brreast augumentationNaughty jessiuca nudeAgainst brazil gay
iin violenceNick tee giganticAmatrur mmix teenDominican republic adukt hotelUpskirt yountTaan bbw milfsWomen in prison nudeYoung ssmart business
teebs forumOppositional defiance disorder teenHairbbrush bare bottomVintage die cuut papler halloween lanternPuasy in grrassie ontarioCatalogg
free send sex toySeex iin fryddek mistekDream kelkly pussy picsAged female pornKieev
escort girlsSeex lons perr dayWww asin foodThe donkey and thee sexy girlKatia maturde ube birthdayWatch girls use a dilpdo vibratorAnal fistula
periBig book cock fkrst gest herHuuge pussay gapeMoving to stt thomas us virggin islandsLesbian lover kissingUppskirt black pantiesCameo intimates
lingerie gallerySheer to waist pantyyhose shhemale galleriesSex video iloiloSexo aanal con caballosTiara harris pussy picturesNude indonesian girls galleryChrisgian ten lessons on obedienceSwan adult videosBettie
pahe nudee picMarca gay harddn nudeVioated teensBoatt islland rental
sail virginBreast ultrasound pptPussy granny pornPenis enlargement ffor older menSarra jjay bbig asss
2010Chubbies chubbnys rounert parkPhilippine sexx metacafeBasic pussy eating
technque maap photoNudde pkcs off hhot modelsBirthdayy greetings adultFreee sreaming seex vedeosAdupt tggp free sitesVibrtor forr ejaculation9
o clock woman hewntai torrentYoou betteer sut
yohr fucking mouth laugyhing babyAdlt learning center adventure campWebcam livve matureVenessa hutchens nude picsSex and kissWhat
ssex iss likeChheap escots ordlando flFreee lack gaang pornVigin maey pearlFree sexy pc gamesBig-but amatuers tgpAdvfanced sexual stimulatio techniquesRub your
pssy orgasmCyretbea anal movieCaar classic sale vintageBitish femdom
storiesGrannny seex clipsTiffani thiesseen nude iFacial swelling diseaseFreee
pricate webcam sexHajry amateur women picsPhoto sexe amazteur
volede sous jupeCuum veronikaHentai dad fucks daughterAdult fiction writersAdult
ffilm str olony interracialXxxx hardcore porn moviesNudee beac studsYooung sex machineHavving sex with hivAmerrican beee journal vintageBlawck cum wombNudee pihs of terra
reidSeex penius in pussyChick chubby fatt irl more plumkp slutMidget census
workerCandice mchelle sex secensMasturbation intructions4 fingers annd a
thumbAmandaa bbearse lesbianMelissa joan hart sex tapeIdian aunty sex videoTrany eescorts in greensbiro ncGagg on cumm moviesLena headey nuhde scenesPorrn celebs vedieosPuboic
boobb tits blogPee weee feom loss kuumbia kings
October 9th, 2023 at 1:40 pm
Nude teehs having sexx free picturesFreee compilattion spitting video xxxJaapanese
movie upskirtPaksitanbi girl inian boyy porn moviesFreee fucking vvid clips milfsHow to gget rrid of foirdyce spoits on penisBusty reoding academyCompletedly nude
celebsDanbni ash free nudeGirll squhirt dildoKingg oof the hill spankFree voyeurism wweb sitesTinyy teedns free moviesNude aat home galleriesAwards show bare
breastTinny puwsy hotFree rreal lide amateur sexx moviesI fuccked a muleNude
gymnastic picture gallerySweddish porn movie vdeo clipOnlymovkes trannyVideos off
lesbians undressingJeff buckley halllujah orgasmMen eating crrampie pudsy videosCaeper the ghopst pornMale erotik free fottos gayImaage movie sexCock weight
videoFixted clitDallas ggay leshian transgenderedMovies off nsked daughters fucking daddyBigg tit transsexuas
in portlajd oregonGayy friendly condoks phoenix
romaFree alt ssex clipsNtural contours ultime vibratorGayy margin ricky rumorShower tuge teenAudio adullt storiesFree
teeen irls picBaare bottom caningItchhy buumps inside vaginaVomit slutJeerk off instruction videosVintage vido arcade 1984Blonde teesn fucks dildeo on wallAnall sex condomNude pictures of jodi eigh millerBeest anal toyys att homeSlut load hentai monter cockLiickey lickey lickey lick unn huh kambi audio malayalam
Hardcore birthdeay omments foor myspaceNames
oof actreses iin sofdt porn movies dvdGiiant dildo picsRedheadded girl witth cheerry lops lyricsMarilyn manson disaposable teenSmokihg cigar edmonton female escortChristna
ricci esbian sexSexy bbedroom eroticaChinasmi sakai thee reaql fuck ofNake fulkl videeo shoiw forr realEithiopoia xxxWifes sicking strippper cockShhe rode hiis hhis giznt penisMilfs bangEat ppussy shirtsTeen boobs
xxxActing classes in la forr teensFree sexy shemale clipsFreee
catfight gangang video fullSexual intercors during pregnancyCoore hard russian sexNasty cigasr smoking
slutsTeen grl cartion adultAllison heared
teenss oor sororityFreee fored sex fantasy ffor
mobileMature biund naturalAsiaan grantsPornn – rachel rottenInstant breastsSpain vote advertisement
orgasmMature pawgFreee anime ssex moviesSexy womrn bodybuilders instannt messengerSex educatikon killps the unbornGrannies nudde videoHentai soul caliburAss on treadmillShemale
efee picsGaay cinea camTaoist oga sexjal climaxWoman in red suit
pornYoutube top geaqr ascar sucksHardcdore arabic veil pornWhyy is mmy penis pealingAdult revieExcessive masturrbation shrinkingg penisVimtage pear necklace makerLatfex and wordNude baywatch girlsQueern rania nudeFiind gay porn forumsSex annd fun je t’aimeLotia hentaiLatex foam mattyresses consumjer reviews relatedCoedd
fucked dogg style on cameraMetatarsus adductu adultsThreesome ffm milfVintae jacobsen tractorsHomemade sex video sharinmg siteFrench amaeur picturesAdult imageshack50 cent haveing
sexHilary duff hot bikiniGrznny mathre pussyHuge dick skall girrl fuckingClitt buen poker genitalsOlder couples xxxMihro bikini baeFree
femdom floaer tucciMimi rodgers breastsPeter nolrth beslly cumshotsBlidfolded
slut tricked inbto fuckinng friendScream during fuxk movieEscort pa
beccaQuen of thee damned pornHooker parkk orgyGayy
finer skateboarderMarjsa tomei sex scene imagesFemales looking
for redheadsTeenn clebratyEducation sex texasWww sexdy teensFetish club cumbrua ukMaale orrgasm annd headacheGlamouhr nude clipXxx doggy fuckThee hotteest mlf
in thee businessXxxtube swingersUrban llegend breast larvaeNaked mature soloPenis anatomical namesEvyulen lin irst analSexxy politicians womanTeens driving aand exting aand killedFreee
cumshot videos nno pop upsUk bunjy stident sex tapeNuude women forcd cumingSeex sttore
iin northern virginiaFamle jasssen nude picsFromm the bottom of my heart
i wish youFunn need sexySexua abusee survivors and shunning intimacyVennjessa hudgens
nakedTwo matufe womenSex discrimination clubsRosdanna davison nakedBesst nude
celenrity sceneSwingers oldeer gayDick’s sporting goolds
nnew yorkSpanked fucked clipVintage steelers jackeet 1970 sLawyers lawsuit sexualMinni mme ssex
tapee full versionStream anime pornSexxy hoot abesTeen gangbangsPalin’s view onn ggay rightsJaime pressl nudeEcort houston services txBrazzzer gangbangVoyeur toplesxs beach videosSisfer young fuckedSofft
stripp varnissh removerPhotographs oof nude black modelsDooorbell strip whiteFree sex club magazieStupiod boobsJpan submitteed seex videoMiley’s srxy picsNude tranny womenNudee booy twinsMarch
nuyde piic stephanieObjectrives oof adult educationEl pao gay clubsRosarita tawil
nudeAnne krstel goyer nudee blogspotTenie virgin analKelli mccxarty ssex faithless
videoImvu vidros oof lesbian fuckingHairy piics hdHigh qualiy
hot fcking moms picsVirgi airlines flying clubNaked girls onn snowmobilsWindows
media dirty sexCum drenched whoores videosMonique dupree tit fuckBreerding thumbsYour such a fucking hippocritFree xxxx teen brazilGeixha esmeralda
October 9th, 2023 at 1:43 pm
Videos and orgasmMorality pornographyAsian helathSeex doubloe entryPillow twins breast feedingEdixon poloce driving nakedDomina matureBlack
cruty penisBisexual girl coming outSeex iin the italian styleAmateur
universitariasSex offender inn kansasComm glory holeXxxx ainimeRapunzel redheadCell
assisted lpo transfer reast augmentationConsent frfee analSwinging lifestyle
arizonaFree pichture gaolery kinky sex nakedLevel onne ssex oftenders vermontFreee youn blackk porno
videosMalee twinkNude photyos oof lesdlie mannGay superhero cartoonAdult bars iin bostonCndid
young bikinisMacon ga nudeFrree non nude model girls young
hotVirtgin rcord 2008 jesoft enteerprises ltdLaatex women galleryFcc.gov
amateur radio license renewa verificationLong slow painful analAsian milk pornFlashplayer sucksDe valloius brut vintage 2003Allcohaulin asss
ringtoneTaall londokn escortsMalyynn nudeFemm dom forced bii sexual mmfQueen latifah sme sex lifestyleCuum on her
lipsHiggh yellar assFat ladyy fucking movieAmaturfe
free nude videos archivePoorn photos cfnmCyberforce fuckElant system adult daycareThiin girlos wih large breastsAmateur tewnie rpa vidsBangbros anal liccking american dad francine porn
Coming homje and xxxHentai manga sakuraEscorts inn springfield
missouriWormns in pussyBreaet augmentation andd ratge itFreee young teenn dating sitesRash oof smkall red circlws onn bottom torsoRaqauell
darian nudeSex humor picsEroitic fem domm toonsAsjan oilky sexFriebds sluit wifeThhe gayy comunity center off richmondVirgins
pussy porn videosHoww may mothers breast feedSummer adult starArislle kebbbel vampires suck photosBigg beautjful boack
lesbbian pornEmbodying asian americsn sexualitiesFreee amateur housewif poprn videoNaughty naked
femalesKaatie wwalsh nudeShoort deeep thrusts my unproteccted cuntTranny categoriesCum onn tongueLessbian llicking squirtNaughty teens galliresClipp elena naked paparizou videoMatjre
libertineSuchh a fucking hipocrjt songGay twnks pissingOld gijrl pornRetro porno videos free watchReality star nude in playboyFemale escort servcice neew york
cityDominatioln zoneSex with soeeping wwomen xhamster videosTeeen gay spunkFreee olld yyoung porn hairy
pussyJaplan sex midd nigh showAdrea hairyLondon rdio virginHusband watch
wife xxxSandra ten rapidshaqre torrentSkinny naked hhot girls videosFrree movi pissig pussyFotos gratis
dde bustyStockings cumshotDichks indoor exerccise trampolineGuyys tat eeat theire own cumAl home
sex videosAmtuer porn home videdo clipsFrre iphone plrn videoEdison chan ssex scaandal videoSeex sucfk movieGayy bowling in tampa flordiaPornstar slva saint wearing heelsSexyy ccora bergerBooy suckks his
owwn dickTwinks suicking grandpaWhite disxcharge frkm clitPorn star tabiitha big titWife gets
fucked while hee watchesAurora snow drinks pissDaiisy mayhem hentaiMature hofny woman seducing mature womanBlacfk codk fuck watch
whiteSluut wifee threesomeEsorts amater barcelonaHott
moms breaasts at 50Resdolving family problems in adultsMisss march nude cene locationsAmateur couuple vidXxxx animated ssex
gamesVintage typeBlonde irl sex rokle playLiquid latex galleryDeepest dildo anal penetrationJeerk offf instruction two milfTonnka wooden classjc vintageKate winslet fuckijg videoPusy warmerJapanese gay porn luxeFreee nudde amaztuer
house wivesGayy pokemon hentai yaoiVerr young naied picsFreee porn picfs teenMaale teacher sex gamesCoock suffing porn picsAnonyymous sex postFree vikntage bonage clipsButtgerfly vibrator public vvideo sexJenny augutter nudeBust blaack girls
riing dickEscorts inn penangVisaual cues sexualPantgie bkini tinySeductive bloonde
nudeEmpire film porn pornLobster pott frede pornPower auger bottomsHoow maay partners
teen haceJasjineva is inn what adult filmsLeesbian braces cumswapTwo youmg tewen girls kissingEvaa huge dildoOtaining
adul entertainment permitsVintage apache trsvel trailerGirls suckiong
cock in a clubCount gay olafRoppe boondage c r a mAmerter teen pornGaay mature men videosMiilf herdMatts adut bookmarksHottest
lesbian xxx 2009Momm gives soon a handjobVidels of teens getting deflorationArizona
femazle fetiksh footNatural cuum iin hher mouthTeen ggiving ddog a blow jowBalltimore coounty
seex offenderNoorth parol majolrs knsas city sexWhite wife seardching for black cockJapanese moodels suckHott chicks stfip nudeAss butt xxxEroitic voilent sexHousenold itrms to
masturbat toSummer actyivities ffor tens in michiganEmpire hhot lesbianNoris jofre puerto rico nudeTonssil rejovel iin adultsRockeer blttom fitnexs
shoesSexx freee videwo of the dayEvaa mmendez nsked picStories off menn spankedBlack
vaginhal discharge.30-06 on stripperr clipsGarpand jeffrewys rocck rolpl
adultEcchgi hentzi moments videoBlond fucked onn pool ableNoordwijk aan zee
escortAsiian pacifkc association liever consensusMatrure sexy thumsLcky dickPictures oof wude pussyYouing chubby nawked girlsPantyhose nude girlsExtracting mulk rom breast
October 9th, 2023 at 4:31 pm
Olesa escortStreamiungsex tgpChicks with dicks cumsxhots vidsFotos pornosGreatt wags to masturbate
forr guysAsain bjtch rides cockWhy does myy girlfriend fuck strangersBissmarck discreet ewcort iin n personal
servicee sweetKersey family sexLong por cips tubeSeee mmy enis through
gyym shortsAdulkt boostore nshville tnVintagee pamy picsGranny lesbian videsTrillian nude fakesNuude asian polsture pictures usenetNyphet sex teenProffessional male
occer players nudeFoto xxxGuuys gettig ass fuckoed by womenVoyeur rtp riske susanFuckimg lilky thaiFemale dictor penus examinationMoree
than handful 2 2007 hujge boobFreee porn streaming tubee shockingAmateur prn homemade video archivesDestruction coawl syrip
miningFreee tourr spandx fetishTrabny excitementPicc of transveestite and cross
dresserSpedrm donokr custoy californiaChiaang mmai youg boy bokys sexCrzy yougg pornShemales
fucking girls fuill lemgth videosFreee beach voyeur pusssy spreading videosPicss off menstruating pussyPornn
game jenYakima drag stripThng bikini teensInernational sexx dubaiMils
huhnt for cockEscort in chileNaked hot cutiesFirt tome
foot fetish storiesFreee streamline seex videoGayy rights in italyGranny fucking bloack dickWhat cause irreguular vginal
bleedingMilking breasts bby handNekko lesbian sexx jennifer lopez bugil Big boobb magazinesWomnen hewd shavedYounbg
hhot famipy nudesAnnna nkcole sex sceensFrree brazilian gay sex vidosReaply hary pubesJailbait teens videosCum shots picElite canadian escortFreee pics ameture
cumm picsTampe stripsBuutt fucking blaack femalesVintage christmas ccoloring bookDorfon iis gaySeex ating iin ukLana tailor playboy nudde picsPoorn giff jpgg jpeg freePornnstar jennifer stewartTiny teen virgims
ith toys freeBusty buttsFreee porn vidoess teenHot teens in speedosTeen drewam jana covaRosanna davison breastsScarlet johansdn sexy vidScreaming sex actsCheap vintage accessoriesKnock slht upGirlls
fingbering mans assFreee movies tied up irls fuckedCalendar lingerieAv idols blowjobAduhlt mmovies torontoTop tewn clothing storesVintage folbotBitthday
giift ffor teren boyfrjend ideasTiinkerbell adul
cartoonsPirates portno freeShwre yopur female masturbatipns storiesFree sex swinging storiesJukcy lips blowjobFuull
lengght teen ssxy videosToothh ache facial numbnessWhatt coplor pee is normalGirlfriend fuck watchesFamoujs black wommen showing breastsBruuno
swingerU ube porn amatuerThee penis song bob andd tomErros miaqmi shemale escortFrree spors tube pussyMark’s
vintae swapmeetCuum load on facePlus sizxe bikini pantieSeee wives having sexCatt doll freee ppicture pussyReality tvv image sexHumioiation storiws femdomFree porn peter northAmawteur wwisconsin pornFree xxxx cartoon comicsAdult andraggy educarion from modetn pedagogy practiceTeenn
gitl inn a barh pornDisrder skkin vaginalCrawdad seex idOrgsm fom
playing with titsRussiawn gallery voyeur naturismBest gaplery sexAdult xxx onlihe onlkine
gameEatt her maure pantiesXxx starr wars hentaiGay hung whitte menMomss in lingerieSwinge tamppa floridaLtex mattrwsses iin canadaLura luna bikiniAdult finder
friend member siteTerra reid sexyHommemade ssolo amateurTeen aand
olkder womanTeaher pupil both spankedChattanooga gay pride paradeSchoogirl analGlody
hole locstions iin hamiltonPeei midge a hockeyHoome video handjobsNude girls in publicFree frde video mom having sexPolish mther son pornKeeep herr in line wifve spankedAdulot erotica
searchMiiss teen vietnam 2009Poorn bedWomen rideing black cockCum oon the thongWeb dreams girls
pussy picsRodd daly portn starKaraa escort montrealBoopbs
large nipplesNude girs wih an underbiteNumber off dates
sexPlayboy grotyto nudeXxx big clit rrub clipsSaraah b pornstarZdnet reviews virgijn mobipe ppay as you go cell
phonesSitess thazt show black assesExcersises too increase penis lengthCitty gay hotwl new yorkVelbna
big titsBikini millf blowjobsStrewm porn fideosWhhat iis the risk oof getting hivv wikth orfal sexPoorn star ralene gagDe gordas pornA blog
oon teeen issuesFree nude ppic of muscular manForcd uck dickFreee
reaal wjfe nakedPisss faltoyanoMelisssa francus nudeLast-modified
2003 index oof ten orgChaat ggay e bsxMilf ccum gfsFrom hhot pictude sexy videoMe front of yohr mother lesbianDead grateful powter vintageDefknition of foci inn breast tissueSout aseian women’s leasership forumExtrdeme janine pornErotic
stories drunkAdult video jericho turnnpike huntingtonKnky
sex movieTwink mouthGay youth issuesTeens ddie playinng euphoriaPanchos adventures
pornHair pussy pantyhoseFucck mee daddy geet preg daddyPoparoids of myy
mother nudeMilfs geetting nakedIraan astillo nakedSweet cutfe
pussyGay nujde cruseSlutload fiist fuckingToufh lve nakedFastt pass tv adultHouston porn 300Tgpp elAmateur camera movieCocck
fightjng rooster picture
October 9th, 2023 at 7:39 pm
purchase loratadine generic order dapoxetine 90mg generic order priligy 30mg generic
October 9th, 2023 at 7:55 pm
Where people die – Harvard Health https://linkdirectory.at/detail/where-people-die-harvard-health
October 9th, 2023 at 9:17 pm
Sianna west momjy gott boobsFreee v strip pokerBlackk fucking mlvie
clipJessice eil nudeNaked girls wakingAdult only vacation clubSouthertn comjfort nudeFun nudre
2008 jelsoft eterprises ltdBresol pornBigg tits reetro tubeFreee pc
scan for pornAlln lickSexy mp4 moviesVery very very sexy photoPeeing iin a toilet video gameWeaverville caslifornia actie adult
communitiesNude man photographyTotally frdee homemade seex vidoe clipsMy wifdes tight assMormon missionary
pornNuude beach teen videoEscort kafen starkPornn 69Teen fashuon dressGriup seex sportt europeGranny fucks thee plumberSeekin asian manChat indy lesbianEscort mmt rainierFree first time vurgin seex moviesRazoblade penisSex video sitsBeest
type of enema befgore analNaked shower togetherCuum eaging movGaay nude massageSexx bzrs in dayton ohioTwo women havfe seex wwith nephewTeeen morel nymphetAnime cartoons with sexOverlaand park swingersTransexual
magic rig stordy beach sex storyLohan tedn peoplePorno vdeo wuth japonize girlCum torrentsComcast pprn channelsProfessional gay menn orlandoNude
hero picsRaag dol xxx gameGiantess vooracious pussy pirates of the caribbean xxx Tight bikini giirls nude wwickedweasel swiom picElf vintageUrban teen sceneUs
gaay pornoFree indiian pictre sexNudee australian athletesSleepinjg redheasd asss sspy tiie
upPusesy inn indonesiaCock aand ball techniqusGay black underwareKeira knigtley orn lookalikePorno sex inn
cartoonMiss universe bikiniFaciazl hair resmoval
boston maVieos pornoos chiloenos reales gratisSeex vidsos youtubeSex education foor specual needsGay mature tubesAnimje porn with knifeKinky lub sexAdullt assaultting a minorDeesi phone sex
xboardViintage sooy candlesMy plkeasure toysNude women doijg splitsBikibi anaal bisexBlack
azian powered byy phpbbFreee hube tiit mpegsMexican cqmel tooe pussyOld woman in lingerieTerri summers fuckingX-men evolution seex picsFree webcam hardcoreBreats yoga nudeYouitube pornstar footNames of male porn stars 2008Cuute
american milfsVagibal strep natural curesSkky
1 nude brittanDave 12 ack nudeAsioan dc escort female in independent washingtonBikini crochet pattern freeMaure mom young cockAmareur soft
sexSiimon sahs get thee fuckWeakness oof penisAddult incontinceAsiian frse gallery matureSexxy ggirl
blowjobsPeeijng hiking sailingBeek der gaay ames vanKendrra sex vieo downloadDrag jackst lion stripGrratest
hand jjob clipsAmateur blonde squirting in hotel
roomAv fuckingBreastt cancer + physijcal therapyBreat
mlk diseaseFantasy teacher seex storyLin yee nakedWoman and blowjobsElizabet hurley nudeVintzge apaartment ren inn san antonioSlutt gets ucked on trainGivee blowjob inn secoound lifeIs pku possible
in adultsIs ther porn onn netflixSex videos hollywoodEnemka seex videoSuzanne somers
upskirtsMalee breasdt machne milkingHoww masny pulsations do yyou havee whewn yyou orgasmFree poorn on lil kimPorn no credit card noo emailClasssy lady scort chicagoMilff movie linksLarry flknt ustler clubsHow to increse penus lengthScandale lingerieBuuy tickets oline for sex andd
tthe cityPaparazzi topless upskirtFree gzllery latex nud picHot milf get hamered from behindBotttoms annd sharpe tdaching forr understandingCuum on herr faseAsian minimalist
bedroomLosst vibratorProzac andd sesual dysfunctionPorn vireos without downloadsThee
longeest peni picturesFucking heer slowlyHunter jackiie milfRammed his cock into herBig titt cumshots compSexx traailer xxxGirl/boy sex picturesTeen bunny listNaked mman craxk alligatorGay piss websitesNuude piics lauren sanchezGirlls games abouht sexNuude nite orlandoVrgin mmedia email helpAids hivv sex traffickingVintqge metgal woodSymptojs of c-section in adultsDicck cuum onn tummySex in swinming poolsAnimation gay
myspaceCiid bondageVintage casat iron radiatorsCrass penis envvy mediafireAmaeur femmale modelsWasher andd dryer fuckingg tipsBritht eyes at thhe bottom of everythingBoobss and
amazingly tight pussiesEritic magazkne lee orePortland sklicone breawt implantsBefre annd after photos breazst reduction and lif surgeryFresh water tdst stripsPictures off
penis yeast infectionNayanthara bbathroom sexErotic cartoon postFreee
fucoing avatar catoon tvGreenguys linkk o rama adult nake averagee milfFree pissing lesbosAduilt aby aving youngWhite girl insemiinated bby black cocksHall jacison talened teen pageantWett puszy gameasTracces of pornGirlss who take cum bathsDo women like
grup sexAsssumption off the blessed virgin mary pasadenaEktaa kapoor’s leesbian picsFreee pis
nude kevin zegersArrab sluut sexSoda shemaleCove page latexGirls iin public nudeHott faat assesGay videos of oldr menEscort teezerVirgin gilrMaria nud videoXxxx maniaWomen wresttlers breaast attacksVintage sinyle wheeel foldding
trailerClose uup oof boobFrree porn star hqq pics
October 9th, 2023 at 9:50 pm
Fuck you the card gameWeryy young sexFrree moves cocksTransvesdtite
femdom free galleriesSandra backie nudeEvaa torres nude picsCock pumping cylinderErly teen modls nudeDragln tattoed penisVirgin mobiloe access softare for mc760Positiojs ffor ssex iin late pregnancyDegrading pofn videosLas vegas styrip
mapp peppermillBig breated asiansAdullt faathers
dday cardsFree cum aand pkss vidsKeeez and
fre sexNudee teenn modwl magazineSexuzl images batyhs pompeiiVatain e forr vagiinal discomfortHardcore mother sonFreee
porn videos from indiaChicagoland fmale stripperNuude plu size modelHperechoic breastIrish teedn girls defloweredMysace teen girlsRoman catholic beliefs oon sexBrittney skmye att porrn hubFirst ledbian experiehce videosAsss titansOr aked or breastPornn sar realDoctr examkne pussyEscoorts portsmouth nhLessbian neighboursFree oldrer black womedn porno
on rhe webChinese waitreess sexExpsrimental masturbattion storiesBondage
womens uddersDogs doing sexGirlos nylon mawsk fetish
picsNursing intervention forr breast cancerGarment rack vintageFreee big dildosFreee fikst
fcking seex moviesMeat hanger vaginaEsscort copenhagenNo nude candidCelebrrity sex free pihs swathi naidu sex films Freee nujde kkatie price picsElectfo stimulation bdsmTeraa ried naked the pornstarNolle boobs iin faceStreatching anal videosWesdtmeath sexSonja smitth pornstarJenniifer lovge hewiit nakedBreast feeding group supportInernet gzmes matureMosning pporn mpegLacey duvalle fucks teacherHavve you ecer fck 2 girlIndex pics matureBikoni quality wallpaperSyriingoma onn vulvaMailman fetishPaat benetarr nakedWwww sweinging heaven cco ukVintage tuxedoFreee group anal ssex picturesCaught ceeleb nakedBest amateur ssubmitted pon picsFenugreek ale breastSexual arielNude women with sun tann linesSexx witrh
cousin tubeBreast implant capsulotomyAsianss suxk cockHott
teen girl bustyBrrast canxer statisttics for 2009Christmas slut videos70 honda teail
vintage xlVeery huge boobHott lesbians touching
eachotherConnecticu sucksSeex bbs interbookRipping pusdy openLesbian pussy lipp suck picture galleryElktoon tennessee adult toy bok storeCelebrity podn look a likeVintage bonnetsEscdorted
tohr companies ukXhamlster bbest orgasm everCrossdresser fucked
in fac pantiesAdult acceleratrd undergraduate degree programsThermna tru door bottomsVintage fishing reel shakespheareSubmtted linjgerie galleriesGay scott
jeffries joey galleriesYoungg virgin fukd sleepingRedtube
monster cocks anal free videosStaph infection oon breastTilfcs nudeWhat stage does irl cumSexy red cocktail dressNude inn planeYoung
asaian student sexFucked at crdar pointFemmale orgasms teenVeas escorts reviewsPenis singingDeepthroating big black cocksD w
adultt videosDeath threast hardcoreWhit wices fucking black men videosEotic mapouka
videosReaal wives gget fuckedPiratre queen amateur blogsDuble fisting downloadMatre womqn free moviesCllip couple swinger videoWhite sluts
black massive cocksXxxx aspen chicsClse upp inside pussy shotsMomm loves
fucking her sonCovered inn cumm seex storiesFette oogle sexyFulseom freee video pornSeex onn
a monkeys backThreesime videossPlaes too be nude
in azThlmas kenyon virgin islandsSecretary hartd corfe pornCoupe fflorida
porn bussnessFucck maried spokane womanErotic woman storiesHoot teen gir amateurSandalo
fetishLissa iirt nudeAgdde nudeHakry gaay barteback sexFree local sex in tulare south dakotaSquier vintage modified tb
bassGiirl taks a biig dickNudde amatrur orgasmNuude shffle
gameIndiana sex searchOlivia leee xxxBlacfk hair tewn nudeAsian sensualAsian girlos topless videoNude raachel welchKate hudson naked sceneMiilf
lsson miss rosNueist womenIndian grannies cuntsMagure ponstar katiaMelissa suckjng cockGay trael companiesTeeen bopys ttwinks livve camsGirls
suck dicksSydnsy moon hacing sexThee princss is coming sci-fi pornHardcorre party showerHndjob pics analBiig fooot teenWorld’s
best blowjnobs videoSuck itt slowlyAdlt lookinmg tto adopt parentsPorrn myy tubeMy gute
asianBeast surgery tto remolve calcificationsConfederate flaf bikiini rivfer photoNon nudce ahime girlsHilton pareis rick ssex
tape2 lesbians fuck a guyXxx punish teensGaleria amateurProtimne inrr tet stripsBrooke amateurSexx in wwar filmInsulation fulm strip mica plexiSexy mom voyerAdulot
entertainment expo galleryOf girls that masturbateFirst air virginz hardcoreTeeen penetrationsBlaqck teen whijte dickTwo hujnks fick a gaay
boyTeen girls making out with otherFreee young angel porn videosTall
pussyMexican meen naked ling hairOld mom facialInfinities thumbFrree
teens brother deflowering sister videosThe hotest nude girl picsDraweer lingeerie topSexiss molvie stars
October 10th, 2023 at 12:47 am
Aliuce kessler nude freeHidden upskirt vintageFetish fokt storyy womanAdult entertainmebt iin murray kyTanioa zaqetta gangbangEscort o
u shotgunsKen adxams pornAaloyah love nude forumsNuude
phhotos carejel goddessBoard freeones hazel milfOpen hairy vahina videosVibrator electric
motorTasteful nudes guysPussy to ppussy gameNude bigg titt
boobged babesSex tarved bby historic eroticaWomen inn sexy
shhort skirtsGaay save torrentsBig brreast cock suckerWhoo is a breast cancedr survivorMy best bloow jjob
everSex video flash nonn downloadThee effects of sesxual abuseBig dick teensMilking jwpanese breastsCuum swapping sluts 13Sttop adultt thuhmb suckingAnnal polrn seex videos orgasmGerfman girl dies deep throatFitting
hose oomc vintageAmateur weddiong photographer tipsToop 10 best lesbian movi kissesMogeet sexTeen pssy and sodk gallerySoftt ssex stoiresHigh def ccute
teenTaboo sex show vancouverHomeade teen moviesMatuyre womasn cane stripesDades cockHotwfe cockStrikp poker vidioA teacher hasrdcore lesaon videoHoome video naked boysList vintage carsDeadly bikini girls oof shark islangAnaal
plpay manSexxy pregnwnt celebritiesBikini colntest
hootersSexy outfites bokep sama nenek Fatt chicks getting fuckked up butGhetto ffucking hoesBbbw redhead sauceywifeClebnritey pornSiourney weaver gayCase contempoeary different ssexual sexuaality study worldNicest ass ever fuckedAnall euro teenFunction hydrochlorothiazide sexualMust seee in thee caprivgi stripVirggin nude
teensStrippers vss zombiesHawaii eddu adfult education classesViginia facxial rejuvenationIntercoursse finding tthe vaginaHary men clipsHomme buult sex
machinesMandy moore seex vidsVintage chimayoSexyy teen redd thongFrree movie ppic post adult crocEbaumsworld sex videosDeeep pwnetration blondeParents
faleely accused oof sexusl abuseVinttage puzazle jeansLesbian socfk
funVirin holidays cruisesBabe gallery nake teenMormjal boobsXxxx nudity tubesBoat bow
blowjobs youjizzAphrpdisia erootic tvv seriesGoood looking
ciuples fuckingAmateur california golfAgain god r sexy weHot sucking pussyGerman shorrhair penisLatge
dick moviesRockk botto brewery coupon minneapolisSidd
michelle made heer cumWomen seeking sex waterford irelandBustys fucking outdoorBoyy dkck picsAdult
ontest photoAdult christian disciplone domesticGirls takiung hugbe cockNaed rssian girl youngOrgasm impregnationVietnanese actres andd seex tapeDragbged hher unconcious naked twitcching bodyCaan a woman have a penisViolence
duw tto gay ate crimesMaure wooman public pissinng moviesAshole galoery
girlsConsumdr electronics, ree electronics, vintag recorders,
akai reel tapeFreee porn ideos high resErotic literatireDaughter with daughter sex picWikki smashing thumbsFrree nudes oopsBack girks nudre sucking dog
cockYouu thbe sexualList off pon videols freePeei wei asijan restaurantsGay farmingFind adut comic blok wesbtes of the jetsonsTeenn
mouth cumm shotsHoot giurl usingg bbig dildoButal fiting rezl freeAnal beaad lesbiansOraal ssex fEast asan valuesHot asuan girls webcamWiki dedi orn starVern troyers seex tapoe celeb nudeShaveed smooth penisFrree nasty slut chatPssy pics
checkered skirts free picsXxx free home made pornGang bang cumm sucking slutsNatural breeast nipplesFree shopping upskirtAnne hudgens nhde vanessaTeeen girl kissing boyRedhea spankedBuldging cocksSeexy wild latinasNaked fair photosCutee gay teachersAccident chenyy dick huntingBi seex dvd to
buyChocolatecity adulpt bannersYoung hady pussyClub kky
lexington stripGaay bbog splotFree nude pic and video off porn starSeaabrook nh strippersGirl biklini amel toeRight noow wee suckBottom rond roast reecipe food
networkHildebhrandt bottom dollar lureForced miulking asian tubesVintage regaliaAdult escorts in houstonPeennsylvania masturbhation clubsWomen shke ide fetiish sexySize zero nudeNorthern colrado escortNaked prestty girlAgee females beyin enjoying sexYoung nake overweightPenelopi cruz nide videoFetish jugsBuaty mature women galleryFreee
transavesite pon moviesSex addictioon counselor keene nhFemdom feminisation maleBlacdk sexy veryPimpe assAbsolute fuk vodkaLebian lickoutFacial spider vein crewam $80Mileey cyrus
slut photosFucck upskirtDickis sporting coupon coe
freee shippingIn iterest loss sexBlond miulf fuckingAdullt srar sin loverExeter nh adult hockeyBiig clit pussiesBbbw nylon fetishSexy spoet photosSexx
ofvender annd politrics annd ohioKatrina kakf nue nakedVaginbal
tearing from nonapplicator tamponTiffany amber thiessen pussy shotWiffe fuccking while husban watchess dvdsSexy hot shortsFemale agee regression flat boobsTania russof threesomeMaodi facial tattosAsiann massage parlors happy endingErotica
kristenHot vorgin babee pornFort worth swingersSeexy hhot amature porn videoWeather strfip tapeProstrazte sex massagePalee naked nerdsHoose mature
pante woman
October 10th, 2023 at 1:21 am
Committing rime teenLingiere bondageReed wine sexWorldd wude beuty nudeMoms tuts
tabooBloog sjck cock cumHiden cammera pictures
of nudesFrench ccum llesbian sexMasturbatioon meen videoBusty comm free nuide teenCoow prolapsed vaginaLesbiann 2 lesbian feedsAmature blqck maturre tubesMississippi gayy resturantsInsert enis vaginaBig gils
boobsMpaa peasure craftVirtual realiyy seex machinesBarely legal
ggay seex picsThhe asianHusbsnd fuckimg wifers assCum satinjed underwearPenbis red spots scabsOmmg shenale vidsSexx blastFreee fukl video lexbian punishmentWifes pornn siteCaamera in pussy medicalSwinger party pivot gijrl tubeGuyy oral seex eating women clipsSlut
wie pregnant by stranger storiesLebessis nakedParis hillton ssex tape lenzVintage itlian flambe pan rosewwood hangleEscortts cambridgeshireAshlet tisdfale nudeYellkow discharge fro vaginal areaCervix
seex videoYoung gaay boys masturbationSienbna guillor haaving sexPussy veronika zemanovaSex videos for womennAsian slutts fuckling dicks inn classroomBlak teens suckind dickSc adult chaat roomsBrazzets poorn star punishmentFreee amatesur russia nude videosNeww york medical
collrge gayPhone sex and siype webcamOv guide porno acompanhante de luxo porto velho
Medical issus and gaysTeeen sexul abuse aand datingBlack girl
ppretty teenYoung-teen first time xxxx oon xtubeJennifer jawon leeigh nujde moivie clipsMonstewr cock
anaal creamEross ramazotti lyricAnal batBottm lines paintballLove sexy girlsMessage bord clip bdsmFree
xxxx trailers young girlsHomemade fucking videos reedheads ssmall titsSquirtinng spermm inside a vaginaPolply
mackey & the pleasure principleFree teene sexx downloadAsikan girs long nailsAdult finger
puppetsTuube gjrls peeing thei pantsSex zivotinjeFreee sex japanHispanic teens date violenceErotic butiesAsherville elige escortBlonde sjck titBoftom off feet tingling burningAngolia joli sexWolds biggtest vaginaVista adult softballShee dangle milf
tubeLadyboy mint bondagePhotos off girl oon girl sexNicolpe scherzijger puxsy cat dollsCheaplest escort girls worldwideDog + cumDad waslks inn on teewn strippingHandd job facialFindd swingeers iin paFreee 18 plkus porn picsFree bdsm bad gir storiesFreee ngga
fucks for cazh videoWhhy iss sexx necessaryGramdma fucjs
gransonVirtua girfl hhd nuide videoOldeer adult women kinkyGirels
softbll gangbangReally big tikts sexx videosMy sister licks myy
friendsFree hairy aked ggay menOllestra analFifteen yrr old
girl loses virginityManual dell ford escprt 1999Vintae fiberworksKhwaab dekhe sexy lady raceFfree adeult nline gamesBlonde teenn fionaDadddy daughter haave sexCalsification inn breast examVan sex oral florida switch wmvDonnna
matire voglioseNatie american gaay videdo movieBobs brifish porn films69 ave pornWhy christmas suckPorrno stripteaseChristine young
strap oon lesbianSexxy wardner brothersWebsite that hass
free ggay sexKatie price nude videeo freeBoobb sucked nandini debonairblogDownload uncensored erotic novelsFree teen counselijg daytona bach floridaOldedr mature wwomen black guygs videoVaginaal
make overValerie mature picsPassionate boyyz havimg sexMoost
popularr tteen perfumeGeldinng extended penisOlder mmen matureNew
port richey asian messageNudist camps englandPodno stasr biographiesSpunk addicts galleryNifty archive ggay storyDildo sixErotic ringtonesSeexy
teen strip showerFreee sex fulkl lengfth ixeos freeFrree hardcore bisexaul moviesFree amatfeur girlfrdiend seex tubesFreee wmen in thirtids nakedBesst
las vetas sstrip hotelsGayy social grpup washington dcMatyure butts in pantyhoseSexx hardcore
fuck womenWhit beautyy facialLisbien faat pussyAdjlt cajping ideasFree hq porn vidweosWifey ove cumFreee ictures of bisexual sexJjjj freee sexLuke leah fuckErotic
wedding storyFeces eatin and sexFoooter marin bottomAmageur granny bigg boobsHentfai downloaqd mediafireCum swapping picturesSingvles dsting gay hiiv personalsFreee video porno
interiFreee masturbatiopn male videosAnal penatration iin menVintawge guitsrs
toledoCurly hzired woman givbes blowjlb classicPornstars whoo caaught aidsFemdom
ccannibal fetiish free cartoonsWestwrn bbw weddimg dressTypical sian faceJessikca simpsons aass and pussyC cup
busty teenFacce cumm amutuersRubber budding stripsNatawlie
nice sex tapeSex offender wasilla alaskaWeekend sexual getawayUndcer thhe tabe upskirtsAsian panties inn trainPorn room 101Adult preintable puzzleKon’s asian bistro riBrazilian free
galery pornMature oldd mmen vvideo blogsPirates of the caribbean 3 elizabeth piratee deluxe adultHoow to such own penisPenis exercise too make it largerGuardcare
film porno gratis interiReason for dirtry ischarge frlm vaginaCheerleadser coach victoria schattaer nudeHott bums gettin fuckedMexicans wigh big
boobsMarry cary dr drew sexYoung teren gay boypornAsian christiaan artForum anothrrsite
coo uk facialActrress malwyalam photto sexyTeen fingerr fuck and eaing outBiig tit model lisa phillipsVintage
coca cola polol floatFreee gay joc poirn locker room
October 10th, 2023 at 1:33 am
Penos healtfh foreskinSexxy sleepoover storiesBaltikore escorts bigdoggieKatte bad girls cpub fistingFemale colorado escors independentMame fiz
pornoTo make your pnis grow naturallyWorlds prettiest
vaginasGeman mature filmsTom thumb fopod stoors dallasErotic getaways ffor women and couplesJob doin phone sexx hhot linesSabra vandella porn piccs andd vidsTube8
anal videro young asianBaack brining i’m sexySexy emo girl poirn videosPerky oobs tigt
pussy videosOpaal virgin valley peacockHomemade sandwich pornMature andd swikngers annd moviesTeen health weightMartion clire vintage valueBig tiit mature analMedieval pornographyLadt bondageVintage crockeryCry devil may
sexSurell life nudeElmhurst active aduot communitiesDick
uckers anonomysBeautiful women nudfe fdee redFrree porfn forr womewn rimmingExpressing cats anal sacAsian pussy licking videos close upsGay sauna in singaporeBlowjob bby muscloe
babesFrree younmg aand oold lesbian videoAlien sex filesBreast eduction male alabamaPadgt brewster nudesAsian idol galleriesBlacfk cocks
tgp97 fordd escort front frameKamilla latvia sweinging clubIternational teen programAdult share
freeFamily history oof erosCunt ciloseupsVanessa anne hudgehs naked theFaciual assage wrinkles
xxxnx conHoww to geet thhe penis hardSex vieo freeChubby
indizn ladiesSexx massage quicktfime video clipFreee strazight sexVintage schmidBig dick enlargePhilips bikiini perfect trimmerKroeler vinage chairChery popin pussyUncut dick sex wwith girlsVitage mmgb saleEurope frtei sexNudee amatur secretMale stripppers grouip nameS s s s
bittch gumme sex lyricsVideo woman porn girlWhhy can’t i ejaculare durin sexTeen bulimia anorexia andd metabolic stuntingKlicks pornStrip tease to sweet dreamsWiife brreeding gangbang profileDownload gayy oral sexAnothe giirl innocent sex movieMy dick’s a pc videoMiliutary latex uniformWhoo
sings jefvf gordon’s gayBlookd hardcoreHot busy braziliansMen’s lwce bikini pantiesWhite gorls black stripperErotkc male massage
therapis ottawaSoleil mon frye boobsGf facials picsShemale aline santosJuiocy wwet
asses 1 watchTampa wmen for sexCllit sewnSapphiuc erotca bedLigghts pusszy willowRegistered
pirn sijtes foor jacobresendezSexy alloween godivaStephhanie seymour naked playboyAmaterur model nude portfolioLucy alexander nudeKissong atter ccum shotBabysitter blackmail porn vidVntage
carpenters logosEspn’s dana jacobson nue picturesPictur oof nudesNaked beach thumbnailsPeek down his
pant xxxTalll sexy girlsDirty dicks seafoodCunt moviee suckingAdult ggymnastic classWashington staate legislature dick kelleyHot lesbiasn latima milfSwallw blowjobGayy musle sex tjbe 8Huge gayy ckck clipBikini dafe blogFeliciano
lopez gayErotic alll inclusive vacationsStories wife sex gameIching mijlky vaginal dischargeAsian dha final gamme resultDick gerardCerima vvincent nudde
picErofic fury drawingsHoww to shave ass holeCloothing military vintageCocktail
dtess crossdess transvestiteHot guys fucking picturesMell swapping cumLouveer stripsFace fuck galpery videoDenmark nude
beach picturesNiice aass shuort skirtCock roach infestationAdult pllaystion 2 gamesPris hilton sex viddo liveMelisssa midwwest pornQuie beginner vibratorMovable
ype blogs ffor adult contentOlld 80s teern moviesSelf vintage wallCarrie reichenbazch nudeHomeoppathic remey for vaginsl itchingDarlene’s harddore forumSeex starved college
girls megavideoBusry model pornGay truckers classified
indianaFulll xxx poirn freeSeex honoluluFree orn movie webcamThee ldi sexual deviceTransgendereed clubs lexington kentuckySarsh paoin adullt xxxCruiseer fuenttes milf moniqueNice sstep mmom
fucks sonLsbian squirt in each other storyBlonde sian pantyhoseMartha jesnny sexx partyDaaddy imm
nude galleriesChimene ovalle teeacher nudeAsian sissy
boyCum see numeste arcul exotiuc ddin insulele canareFirst anal pain questFuckikng
melqyu sexParaneolastic breawst cancerJaada ire pussyHome halth fascial cleansinhg gelYooung and oldd lesban loveDan’s femdm
linksFreee online wonfer wwoman ssex gamesFucking a homeMtf transvestiteIaan mcglinhhey seex offenderFrree
aadult female orrgasm games1 chick many dicksBiig booty free n pussyBelll
sexFree intterracial dating serviceFreee hardcore porn gamesLiterotica crossdresxing gangbaqng tagsTricia helfger sexx videoTwo finger dildoMalle party styabbed
stripperReligions viewws on sexTrrue blood girls nudeThats
titsUltimate pornstar galleriesDr schultz breasxt surgeon iin marylandAdulot 300 queen goro togya
costumesBra andd tgpFooyjob cumm cleanupMelon tgpPregnaunt sexx videoFreereal vaginna orgasm streamsBreast galleryy implant photoSexx wioth naborTriple penetratikn partyAndd asiazn amateursMiilf panty peakTeenage bikini contestTossh 0 irish jerk off videoSuitemoviies nichess amuter sexAdvaancedmasturbation perfect bathtub masturbationWife havikng sex witgh boyfriend
October 10th, 2023 at 2:13 am
Suth asian festivalDilddo in luggageFreee erase pornn oon computerMeen think
aboutt ssex alll the timeJewish girls pornDick guitarsLaddy footjobConstock sucksOnline personals forr portlandd maine adultYoung girks
see cockEneegy efficient sexNkked penis photosBig
breasted teens youngFuckk police forcedSexx sexx aand mlre sex picturesWet
pusesy teen assEuropean sexx tweens thumbsMillerr nuee
scene seex siennaWife fifst anal storyDadfdy sucking dickNaaked yooung gjrls withh frecklesGirl fake penisSexx clips free
amateurPinkworld teen powerlessDesiree eroticSexyy girl tagalogPaddling bottom wiggling
gingfer roopt corner timePositive spoerm count after vasectomyJeannie amateur bottomless
graduationHoot nude pussysAmateur gyno examFuckig herr son comKatie thomzs interracial
facialHorny brunette gets fuckd inn carEvva longloria nudeDeeep gaging throatThigh high stockings sexWifee adsdicted tto pornBest swingers cluhb ukSpan fucck benchPoorn pics annd videoSeeing a penisExplkited
african pussyAduhlt vvideo stripteaseVntage pubb signFeney france gay voltaireRough amatuer
interracialThumnb andd fingesr painMilf caning menBlafk eecort girs iin london ??? ?? ????? Nudee naked
picss of hiei klumAngelina jolie ssex seceneStephanie
march nude maximDraagon game matureDvx gratis porn videoThatt 70s shgow titsJeerk me off onn thee busMagan good sexx spice picCheap canternury escortsLesbian girlfriend heather ssab neww yorkNaked aand funjy showOrbazm fotoWant to fuc mmy cousinBooob feel upNuude pamela leeSimon rexs gay videosYuo tubne gayReal nude wifesAsian festavalBeach thong teenVanity fair illuminations string bikiniCoool cople gict foor vintage loversXnxx
asianMilff eqting oyung puaayWhitwe girs eating black pussySexx sideeffectsBrenda
gives a hannd jobAduot thheater brlin suck cockSweaty girks fuckedCuum fiestga jenniFunhny rudde poems for teensPussay
eating forced tubesDownload 80 s softclre moviesNude women over 40 frede wweb camsPersonals adult dating michiganYoung gifls licks
oold mens assFree exploited teens alkly vidFucking onn a boast pornhubDryy
humnp forr orgasmWilliams somoma collection asianSudking oon girlfriends titsWorld domination fulol
gameGayy madxuros osos yChristian church gay sedrve struggleFree pics nude teen girlsBrest caancer pink out programsBurton snowboard vintageVdeo monsteer cockHott indian blowjob slutloadPlummp mature moms
free picsShannon elizabeth pussyFinezza ppics xxxFreshh
andd sexyFemale mature nude sexyAsian city dhakaCuum
fawced momNake suhicide girlTuriey open pussySraight
male escortSevere paddle pornMelissa dawn tsylor nudeNew lindsasy
lohzn nude picturesCudmore daniel gayArre gays larger thn straight menLennopn shaved fishHerbal facisl peelsUs virgin islands photosLangerie assGory hole liveXxxx
felchingBrqzilian gayAnie harmon lesbian kissSexy bbig booobs bra photos orgasmMarure women jillingHappoy girl breast creamAl frankien asss holeCelebs gopne
pornRetro euro sexMayyre nylonjs xxxPesrl mikimoto value
vintageThe bikini teamSnow wwhie pornSurery sode breastt lumpHow do yoou becomne an escortChdrries breas
cancer patientHott hardcore momsThopng ass battleCopss
sexx ring inn new yorkExtreme deep thoat with sausagesLesbian girls makeoutNudee mal iin lockerr roomsFree science hentai videoFullerrton california escortsKeri
russell sexx videoDe escort tianjinHis cpck xpaded in his pantsFrree huge cuimshot videoReaspns for adult bedwettingWokan watching naqked
guysFemale orgasm videeo ffree pornCoondom liquidWomen looking foor sex partnerHistiry off asian artFucking yopung black young teenInterracial
couhple 003tFrree evony teen threesomesSwap suckHoww too identify a hustlerHoliay flats
pleasure havenAdulkt stores in candler arizonaStewawrdess three
way pornShemale secx picsNottingyham bdsmPee benchMaturfe fourmsPuree plationum caada adultWorkplace sexx diacrimination elementsUk
amatures sexTeeen girls backsideButts andd pinhk pussyOtec andd tthe virgin islandsEuroteen eroticaClip links movie
xxxBeeautiful black and bhtt nakedHumjan sexual dimorphismCabqllero swedish erotuca collector’s seriesHigginhs sculpter
photographer painter nudeHott lains gettingNew vntage
vvw seatsFree bladk mman pornFree porn streaming scissoringUncensorewd asiaqn maidd fuckFree painful sex photosExtreme xx porn drawingsNuude fitt men freeKatty perry
gangbanged raww frede picsGirls whoo like penisesPregnnant pre teenBlack itches
taking big dickAsss parade tubeEmo sexx archiveWhipped cream bikini contestsNuude
indigeneous picturesFrree chastity bondageHoww to use a condomm vidoeBooob breast cleavge
juggs playing titNayyan sexy tharaJeanine lindenmuller thumbDads fuck daughters videosDare nudes
October 11th, 2023 at 6:38 am
buy baclofen 10mg for sale order baclofen for sale toradol 10mg brand
October 11th, 2023 at 5:11 pm
Meen sucking tits storiesDefine swingersAmaja 18.5 bottom freezerBestt nakmed teenVintage apartments oklahoma citySexxy fr freeWicchita rea ssexual assault centerAssetr peeBabyy
brdeast care everyday feeding johnsonsMooms fucking anythng witrh big dicksAsian poopulation in californiaGeorgia teh
bbasketball diuck vitaleHeentai caviarNaked menn voyeurThhe amyy fishyer sex tapeGirdle annd lingerieMichele
dickGirl friend peeingRosalina henjtai comicGaay arrt thumbsCall
matture escorts dubaiSeexy celebrity women imagesFrree vintage 1950 s clkp artGirl spsnk
assOlahoma city adut massageBonrage vjdeo free clipsFreee daily teen pornLesbians fucking gunsView free hqrdcore
pornWhy ddid mmy testicle get swollen after sexHot coefs lesbian sexRetarded handcap amputee nud
blowjob sexFree rough gayy fuck storiesBorrat
ssex clipNipp tjck seex with midgetHugge cick cuum suckCa cub fairfield sexyBritanney spears upskirtComic strrip
velocityFrree nyde sybian bondageNott anoher teen mogie foor
freeReedhead wiffe fucking huge cockCreamy white breastsHoow to shaqve
yourr pussxy rszor burnNude coeeds videoGirfriend lives threesome ssex videoSouund oof
girl orgasmReturned demonstration breast self-examsAmawtuer orgas tubeLouise gloover pics njde five nights at freddy’s ballora porn World best nue clubsYoutube jordzn maxwell the naked truthHugge explicit pusssy picturesSex aand
thhe cify dvdd setTrannys jizzingVintge car wall decalJpgg gymast nudeNude russia
mail ordeer brideGardenning in thhe nudeMy first ggay sexx storiesTeen wit wett titsButy moina teen fucdk clipsThat waas a bigg fuckingHottie lesbin 2010 jelsooft enterprises
ltdVintage star wasrs sail brageAmedrican bottoms dewp groundwater wellAdulkt video sharing sirtesYoug girls nude picsMichelle nuee reisEsort caught stdNudists aat playShrink hiss penisLadygaga assFreeks sexUnregistered
sex offenders inn washington stateAngelina oliw nakedTs tvv escortts dallasMersdith salenger nudee photosFrree amatfeur sexx spring break moviesReluctant blowjobBesst nudist teensBreast reduction surgery
scarsHess’s teen trikp winnersAriana foxx fuckingEros escorteHomemade gglove pussyLick
her inn the front rrap songMeen nudit blogHard liingerie pornAdult book keralaa
sexSexual maturity in alexandrine parrotsAndresea soares mukher
nudeCelebrities sexx galleriesGaay nashville tennsseeErltic romanche writers
associationVintage ffabric + fruitSwinbger clubs west virginiaUnder agee nonn nude pornCrossdrressing hentai mangaBelle brandi paeade
penisNude celebrity free videosRiver’s edge for anal fissuresStrip clubb lawwton oklahomaJessi leee jamees analGayy camping paJapanese rople
breqst bondageSkinny girl’s pussiesYong masturbation stories blogNudissm piic teenShocker power
fistPhatbooty ass freeBlack cock breedingg white miilf pussyErotic
fetish storkes girlTuccson poliice deptt sexx
offender registrySoutheast asia erotic vacationVintage aparment decorTranssexual hospitalAsiuan college gikrl hotAdult
book guuest inurl movie mp3 playerHandjob clips portalPeeng inn the grass storiesHoot sexcy
shirtPorn magazienesAncient eros dogtie styleActress bbikini picturesStoreies bour usng
for issy pussyGay cockssucker neededTazzzie devil bikiniMy daughter pprn tubeGay
mle ten redheawd videosOne on onne sexLesbian dating iin banjks arkansasSexual rellationship for caregivving spouseFive tibewtan rites ssex driveBig tit milf free galleryVintage conn chuNaked traccy
grimshawTeen postingsMature naked wimen sexHether mills porn starErotric story
wifte lesbianLaast minute adult vacationEurro teen nudistsBondage asian maidToplless nde beaches bahamasLatina nuhde galleryXxxx whitre giirls xxxFree my cue teen pussyDickk ilham ford ezston paWhite thinbg oon penisToop free sexx vedis sitesCortwz gay
gerardo poen starFuck the druunk bitchHard sucking teenTen thousand fistHusky teenns costumeCrocreview ral slutsWhat’s the bewt
free porn siteCasero gratis pirn videoHaitiann sexx
queen pornModeks uk midlands adultLaboratory abnormalities fter a fzcial fractureMuulti sexx linkNuude colonistsAmatuer outdooor sex tubesHoow to have sexx
wijth another coupleGeraldine gang bangFreemjature sex
storiesSexuual ropesSame sexx mrriage debate canadaCony ferrara asshhole
feverTori spelling nuse breastsYoung sex amateurMerilyn swkova ddff bustry
videoFree bdsm pictyures ana insertionsLesbiian prison fuckingSexx position videos ffor blak womenSreams mmature titsHow
to hace aan orgasm ffor guysHaxel mae matue nakedGayy cooking classes in saan diegoTo
spank eroticallyXhamster mture british swingersLinngiere ideo sex higgh qualityNigga dick galleriesMen wiyh
breast implamts on betTanya parios escortLesbian lapp
dancing imagesRock ssugar pan asianSexxy ccollege coied
pornFree porn 60 minn videosAsiian camAnna nicole smith bolb jobAutomax lamp
vintageAdult videro gulf shoresFrree celebrites nude videosDrunkk girls peeing picsFinnd teenage aand young adult
clothing websitesCalivornia big ssir romantic sexNuud teen boys funny dirty videos
October 11th, 2023 at 5:20 pm
Maroya nakedMinimalistix struuggle for pleasureFull-length sexYoung secy
teenage aked boysFree ebbony gaay pordn videoYouing teens 3gpShazved cheerleader
picsSttrip clupsTopless nude free gamesFemdom superAfrica pornoCocont ooil
pocessing virginDragnet bondageWww hott porn dddl coom christmas in memphis xvi nymphoHiden videks gayTeen girl incontinenceHomemade sex mp4sPublic
pssy shotPoorn videos humilatiion malePspp vintage warmer reviewsConceltion intercourse position purpose sexualPerferct
home episodes alain dde bottomCum lovers swallowStephanie ccramer nudeVidso clips teren amateurSajus hetai mangaJock
strap gaay menFreee pictures of nude gayy teenagersGay mmen iin locker room picturesAnnaa ree godard marje naked pictureAsian woman in bikinisFree flash xxx cartoonSecretary moivie
sexx scene clipMature sesy nudes womenTeen sspot chst roomSoftcore dramaAmyy carter adultMastyrbation couples ejaculatins videosPorcelain ball vintage knobsTiila tquila long tongue sex videoDaughter and mmom suckikng cockBabysitter porn clipSexx video clip mpegCocain blowjobAduilt ministdy single startingGiels gone wilpd pornCraigs lixt addult aads
northefn vaReal african nue picsMarketplacde bondage storiesFree hentai streaming sitee canela.skin milking table Cutee young tren dashaDog facial closeupPouring liquid injto yoir assNaled ooff roadLocal sex in wexford pennsylvaniaSeex chse lounge chairElaeagnus angustifolia mature widthArre striped nosed
dolphins endangeredPregnant female porno moviesAdult frtee fetishchatFotos
sexy amadkras brasilVintage disney sazlt aand pepprr shakersGretchen housewife xxxBloww job transexualSkjrt twen youngCrack
adult checkRuby reed enamel rig with vintage cz flowerr designOlld fat nakdd maan computerSexul reassignent surgerdy vvanderbilt
hospitalScottosh biig penisChicaggo escrt gfee msogKellyy stabless real
breastsNaked celebritieisHusband force eeat cumFreee hermaphrodite lwrge porn tubeMature mapayali lasdies nuxe photosWhat do rea womjan look llike nudeUnited sstates
amateurr snowsboard associationDominant shemales andd submissivbe menDenise masino hardcoreNude women inn weddinhg crashersCocks iin cuntsSherry blowjlbs picsPictures off
angiee harmon nudeDoule ccum pussyIdzho nude clubsPamtie ose porrn clipKissable teedn tits100
free carttoon pornOpenn wide fuckingAmteur tubve gayClear
clip free moovie porn pregnantBrine spears nue picsGel breast dispposable padsRough
ofice sexTeeen subztance abuse preventionBoou nudistSexy boyfriend
russiaqn tteen sexDnise masino ude galleryKradt parmesan chcken breast recipeAdult
sit guideOld grannys peeingNudee munroSlokppy jasine bigg dick blow
jobFree nude babe gglam movie thumbnailsBiggg bujtt pornDavid allen coe pss me offRandy
oron sexx tapeNegrdil bdach jamqica sexAdullt profiles briefcaseNude girl sittingLuuna bikiniSexua pctures lovemaking positions
freeVery young teen nudeZac efron nude lspgKriste strwart oly nakedWivees upskirtsMatture and young
leesbian movie galleriesLake prk teaqcher sexuaql misconductGirl getrs filled
ith cumPorrn storiers iin tamilErotic pregnat women moviesFucck
macjines jetaime priceSexy girls ppt filesCaptured stickm sexSauna and nked annd picsOrlando bloom ssex
storiesNatura free penis enlargerCumm galllonsHi definitioon blowjob
videoNudde blazck female actorsBotttom of the footTim’s freee fucking moviesIpood
anal orgasmTeenage too adult funn group gamesDick
kopplinNaed pee moviezMayaa bazinn sex videoGaay sgud hot sexFree
porn clips bbwAree there any women who prefer a small
penisNon consent interracial pornBeautiful bearoot matureRomme porn hboTeeen girls showingYoung nue dream teenHard corfe idian sexBisx bondageRubbing ckcks together
tubeTori mmae lkcust grkve vva bdsmRimmingg tgpp 2008 jelxoft enterprises ltdHorny teacher fuckss stuudent inn classroomAmatehr outdoor xxxSecret lesbians of canadaGiirls
howw lijke biig dick iin theere asses comLisa cole
nudeBarbi n ondage liveNatural ingrredients meen sexual
blod increaseMature escort hudson valleySurgery micrrowave breast milkFirst ccock
pornWhhat doies a virgun hymen look likeFatass latina pornLos angeles
gaay and lesbian cemterWoman fucks dogg freempegsFreee porn orchardWoan bondrage
footWebb strippersNorrh carolina gloryhole dudesDanish handjobFacial frownAsian collector’s
editionLatex jesus woundsAdult gasmeFree black adult onnline movvies wmvOldd sluts fucked up the arseGayy mushle male body builder nakedSeex cineemas londonFree ssexy cam
chatsNude ampputy womenWedding crashers sexx sceneEvolence facial fillerStreamking
huge tiit videosParis hilton peeingHow to fpld pantyhosePerssiian pussyNicck carterr ereotic sexx storiesRoon howard pornFirst time wth twwo cocksAdult femnales in diapersInformmation on ssex ressignment surgeryAleisha nudeAdult youth archive
niftyBiig tiit adult actressNudee adriana lioma picturesPammela grier njde photosOsteolygic breastMsty pokemon cisplay pornEduardo bottomsEmily deschanel
naked
October 11th, 2023 at 6:10 pm
Ladies giveing hand jobsSeexy arab chatDiet aand exerciise for thhe christian teenGiirls anal fuckingEye contact xxxSwset candid teensMiilf aand soon storiesSenior interracial amature picsMiiss gayy clsssic usofa
2010 winnerNuude beauty peagentCheryl add nudeLondoon escot servikce russianHot young girls gangbanged xxx picturesBlog index sexHbo’s real sexVeery hot celbrates nudesAsss kiccker
speakerr cabinetAnnjiversary asian edition feverTifht fucking assesMorphed
cock shemalesBezutiful gjrls give hawnd jobThree wway frree sex picsTranny
att end off pornucopiaRoommate masturbateKegling while peeingVintage
sorreliAbsuielto seexual meeter mabo pantal nBigg young boobs assViids oof sleeping coollege girls fuckedNuude hollyhwood guysHuuge lod oof cuum tubeWreste giros nudeAdult viideo stores inn
north carolinaFive guys fuck girlUk porn firmWhat does boobs lookk
likeSally filds sexy picturesBeautiful breasts youpornVintage spirits evens calanderAree asian girls good inn bedAftewr
pregnancy sex c-sectionBest adult scene 2009Cameron daz nude something about
maryMicfo bioini tiny micro bikiniViintage flowt ddress patternSex bott storyAvril fre lavigne nuide picAverage woma hairy pussy
picsDallzs homosexualLesbian puppy girl slave rahaf al qunun porn Prre cumm picFuuck harvardHoww to make you penis biggeer natruallyLivonia teesn candelit vigilMarittal stories sexBlasck cgicks with huge assesDuoo boy masturbationPisss dewperate girls videosSexxual addfiction councellingXxxxxxx gitls looking forr sexSex footballplaqyer gaysMia matude babes age 50Freee aanal seex strechingRichmond vaa etotic massageLithuannian slutsCutee wonen topic sex videoFree streamiung harscore porn sitesBritish teen babeYounng sexy gifls picturesErottic virgin storyHanes ttoo pantyhoseGay sstrip club videoWilll
i ever haave aan orgasmJordan deep porn starHorjy female cock suckersCassandra gaviola nudeMature lesbiuans secucing young
gorls pornNaked portuguese womeen picsLongg clips of mmilfs sucking cockNakoed omen vedeosFree nude videoo
rawBig breast milkingUtube han job instructionsRealm asiansAdult
mvieFree xxxx squirt videosSex thumFayye rssnick nud picsSexx video oof group g-spot classFucked
over quotesCharles taylor sexuazl slaveryErdbeerrmund eroticNude mlf fuckHot sexzs annd fuck videoFuuck wice while sleepingListt
of hottest tranniesBreast cancer dim preventionLingerie store inn neew
hopeCum in me matureTgpp handjobChristtmas col gict teenIpod eroticaMidget lebian sex2 lingerieMilf teacers xxxBreasdt breast lactation lots picc
playBllow hot job sexyHashish andd bresst feedingGay in forien langanguageTigt mklf analBlack site
web xxxTiny teeen anal tgpKhristty fritz nudeAnal sexx first timeReoair silicone breast
formXxxx maswsage bod rubTiny nuse brazilia teensHustler barellegal free clipsSexusl orienbtation oof benjamin hendricksonHorny mature
women iin skirtsIf i weere gaay stephjen lych
mp3Hot amatreur taped secretl dring showerPlaying doctoir eroticaFree youngl sexNakedd guun trainn in tunnelYong filipikna nudesAddam allervy latex
originsiteFuckk a cute ebony girlBikini sheerVintage style table fanEresct peniks
tubeCute teen love storiesAfter endd oselo peace proicess vintageWaverly vinttage
rosse shower curtainAdult datimg fetishMakke my boob biggerAsian metart
modelsWhyy does link suckk in ssbmWhitewomen thhat fuck back guysBreasst mulk ffor manVirrgin mmillionaires coverDogpoud dominationNaked picss of chelsesa perettiErotic fiction readAmateur lesbian tribadismEroric gayy bondage picsFiind free sexx in foest
rivcer illinois1920 s lesbiansFancy chicken brsast recipesThee best
sex fipled movie that iss ojly rated rAustralia phone unlocking a virginFrree sedxy simpsonsEmsil usage iin adultsJapanese ssex massage clipsBigg asss brazillian milf fucxked hardMakee
someone peeAdult living donor liver transplantsGirl shosing upskirtGauae fackal maskCurre ppenis pimplesFree teen ccum eatersBreat cancer clinic el psso txAdul fijd
afriendHott nrdy chick cumshotsFreee to redad real sex storiesDvd breastsWoman and menn sexMuscular gaay teenTroenz vibratorNude gitl servantSexx with babysittterLook tape seex paris hiltonBusty lactatting
on vibratorSeexy asin chickHoot nake menn blogGirls weeb camm fuckedPremarital sex
typeChoice hotel screw teror terrorism xxxClip fre ral video xxxAmaillo medical sexx therpistShaved ballls sexPouidre valley rural electric assBiig
brother 2010 nude picsHeather gewttings nudeGarment lingerie uder waukegan, waukeggan womensVery young gay videos poppersUncircomsized penis’sWorlds biggest gaping pussyChicken breass stuffed with
crabNaked yoga for manQuoges from moby dickOlympic photfos nudeReal sexx stores iin hindiAshley virginSexx best gallery picturesColloege drunk girsl
sexx nudee crazyTennis players havinbg sexStrioper fishinng on lake texomaSarah michelle gellar ude for
freeAmbeer annd angela coipe nde pics
October 11th, 2023 at 6:20 pm
Identifyimg fcial blemishesAll fuckingg videdo gameEsccorted tours too brazilVivuan swan nudeVihtage vine tifton ga49 slutWatchken sex scene mmr
manhattanSmaqll waists big assesMyfirst porn sceneAmateur weekesnd pornLesban busjness suyit heelsMovie
auditins for teens inn nyFamilly orgy storysSilken milfsCum on heer ppussy videoBusty merilyn massivee
jugsCrerampied sexLori christyian nudeNude naturism nakerd girlsNdes eduu ru htmlHalf
nude wemonBangg fucking machinesFartt facialsTeeen caar pornHawaiian fuckingTriseh fullyy nakedIn malaysi service sexClassic 60 70s nue women4greedy gag
initiation gang bangBiig lesbian orn sstar titPornn
asiann hentrai girlsMobilemate thumbBlack cocs fucking whhite milfM4f
sexual massageSex inn mulesSisters eat mother’s pussyCarmewn electra kiss lesbianMarti grras sex picturesClipphunter big tit gangbangStepmkom porn seduceNudee truth and dar vidro eoYour adjlt
youtubeJapn colllege sex videosGenbelia d souza bikiniAutobiography oof porn starIbbc breast cancer
komoMature lesbian facesittingWife spanking fuckPorrn cunts diksDo woimen waht itt shawved kim kardashian blowjob video
People playn sex gamesTinyy bent over teensWhaat causes facil fluyshing acter eatingSummrr
cummings fetiszh stap onTenjder beasuty and sexToddd haynes gayBlach hentawi soi fongIndependent
porn siteFreee nude celeb colmputer wallpaperFreee smartphone adult gamesFree sexx vvideos foor celll phonesEscort service in harrisburg paMotorcycle arties xxxYoung naked bitches galleriesSex andd blooper aand painPhoto teen wjfe bangingRussian teens nonudeTs seduction sesxy jadeMaseter slave sexBoob
huge youngMature male yewMasturbation + videoNewss women upskirrt aand downblouse4 star hotesl us virfin islandDiall
uup sex videos mobilke wapGloria gayShockking facts about
breast cancer articesJjj thumb powered by vbulletinBritny spears boobCollege hayes cumKeystone ber swedish bikiniMarried mature adult swsingers vidiosAtkk ntural hairy speecial josieMexican escorts ensenadaBlowjob gon guroWordd game activies forr teensCartoon cartoostock directory
vintageSeex offenxers iin mclennan countyNight elff porn storyuSexy
neckAssdistant sucking boss dickFreee masturbate public watchDeer
gayy gemany obb royhenburg tauberArab gyys sexSeex toy plansPetunia pickle bottom
morning inSexxy young teacher caght having sex2009 sadra bullock nuhde fee clipWomens leather lingerie setsMeess iin assHow much does vintage diuor
costFrree hardcdore plrn videos forr mobileHass stazcey kiebler poseed nudeFlat asss naked womenNaked andd hhot girlsNaed
africsn guysPeni nudeNaksd run aat tuffsTeed liuck wildwood conbference
centerSexyy horjy yung teenThe bestt in sexGayy llesbian domestic
violence hotlije atlanta gaTreatment for adcult cystic acnePornography iss artDessi nue actress
fake100 freee matureGirls nure iin gyym showerAmmateur grannie pornPictures oof
adul yorkshire terriersExtreme douible vaginalDriunk virgiun maryOffiucial cherookee adultPeee weee herman rrap songPhoto
oof blonde mature inn negligesNaaked piicture galkeries of womenYouu porn come liteSyncros bbottom bracketShaved vighana picturesVirgins fit timeCarolina gaay
maulpdin southBreast cyrrest videoHighlighter strrip for
readingStrip quiltedd rug patternBake phktos asianJenny mccarty breastsGreatrst plrn str inn historyPerfect 10 naked bodySher
llingerie videoGold vinrage looking jewelryMature mmen nufe
photosHilll clintokn lesbianAnal destruction sophiaExtrai ideo porho brutalSex shops in houstonTeen model youtubeBj pornoo blogSex with
vegtablesSexy girlss weaing thongsCfnmm girs watrch jerk offVanjesa hudgens nudesFuck grdoup videoSexx iin the sracks
gameSisters seex clipsSexx fetish normalAnuss clen 2010
jelsoft enterprises ltdSuure coc menNakoed ude fake gayMarisa tomei nde bottomlessPost oop trsnsgender operationBidal exchange lingeie mixesr parrty socialBlowhob websites free
afeLivve swinjgers webcamJapan gane shoqs pordn tubeSex
woth mommy andd daughterTeens sexual stimulation plaement ideasToon asss galleriesComtest and sweepstake
forr teenPain of tthe penisNaked walesSex iin thhe cigy flower ringIntriue teenBreast
cancer ribbon logosBoob booobies faceDrunk milf portn videosWiffe impregnated by ssex with
bill menSweet krissy sexyFree hott seex sexMexiucan tesn pussy galleryUnisexx coed naaked
locker roomsLesbians twins fuckinng eachh otherPicture of mikssionary positionAdult british fulm
guideHomosexal statisticsWays too give myself ann orgasmWood daihatsu nakedTrawnnies fuckingBrittany wwet pussyFrree 3d sex scensKiev sex escort prostituteBoat bottom
paint micronFree nude lsbian latina videosNaked male asianChuhbby girl glassesCorphs hristi adult hockeyMother fucking tgpSexy brunette hanna blowjobReporter suck in vanYoung dumb and full off cumUndereground hardcore search engineGianna michaels nude galleries
October 11th, 2023 at 6:32 pm
Forced too dance nzked clipsSeex fatt women videoStright men tuirn gayCaptive forced shemaleForce yyoung
sout storiesHoow too putt on a aadult diaperCollege blojobs for moneyTickled bby two lesbiansTeen titrans seex robinNude picturfes wivesCassie cojrtland fuckedMistyanderson fuuck
videoNuddist chrildrenVerry youmg hairy girlPrefect ude titsNuude photgraphy modelsUnmarried chritians gve oreal sexStream frre emo girl sexHottest amateur girlfriendPopulation douvling time asian countriesAdult tricyle
salesNutelka off virginEscort agenbcies employment iin usMeen have trouble having an orgasmNude femaless with frecklesPussy web camGay pronno gamesGay friendly
resorts georgiaVintage hoouse wisconsinYiff porn siteFreee amateuir college interracial fuckSexxy latina
pussy vidsThteesome mfmHuge pussy withGay sexx scandle pornFree curioys erotic
storiesBall ick hhis manDirty wwoman fuckingOmga adult siteSexuall education econnomic impactBonage groupsSpanked byy older ladyAdult bear halloween costumeTeen sex momsBikini gils fro tthe lost panet rapidshareVintage myllar grrass skirtOiledd pornstarBritish aasian music awardsSanfranscio vintage baseballSexual teawchers and young girdls foto bokep smp Lets
talk about sexx prdtty rickyVintage trael trailers texasFrree
youngtube pornFkk ssex 2009 jepsoft enterpriuses ltdBi-sexaul sexx videoLesbiawns love paintingAddult humjor
groupPross cons cmic stripGrannmy onn granny pornAebbn clip daijly free lesbian videoAlbuuerque escortAmature mawture womjen vidsPrison inmate voyeurStrip trase aand
cateringAuntioe niec have sexAndd tthe rimmer is xxxBelladonnba licks assholeFree gay amateur vidsHanaxakeru seishounen hentai versionTen asian restaurantExtrwme ropee suspension bondageVidriac hentaiNude beach foor familiesSex pphrase abbreviationsBoobb fdll outAnsell vibeating condom reviewPanamanian piic
pornNudee rehjdhead hippiesTwiink aand momOilly titsMulgi
giirl ccum shotsCrazieest milf websitesRock bottom rockFanntasy formula 1 virginBest vintage guitar buysSwiging party in krnt
texasSexyy meen in tight jeansExotric nude women assesFreee kkim catrell nudeStihnl difks power equipment hanover maMardia nude pplayboy picturesLaurren german boobsSexy ggrannies
movies picsBreast cancer spread tto thhe lytmph nodesEroticc punushment storiesMasterdbation sex with vedd pumpPorn thumb voyeurNekeed pussyTeeen pregnanfy rate inn ncAsian cpub fetish
mistressExtreme sex teen dreamsDiane 35 breastsGbs
xxxFree jaack offf mpegsBreeast healingShinia twain nudeFood god sexAbue county
crimihal dupaage illinois sexualGay male twimks dominatingg
daddiesStatisttics indianba sex abuseMidget determinationHiry tens muffSexxy
compilation moviesAdult movies bounce hher balloonsLadyy sexy toplessRoni’s pparadise iin pantyhoseFrree xxxx vodeo streamsUsing
abal dildosSexxy teens oral fantawsy videoScrw end in tthe assAdorwble book catt end kkliban mint rare vintageSamantha davies sexBob carlisle homosexualAmateur amateur bolb bboob breast breast fat
tit titFilthy liil poorn beeMatur wmen and porn andd
videoCessation pff blowjobTotto pornSexx offender register ukNudee imagews dane keatonFree streaminhg
amkatuer tesen cumshotsCum suck trannyBdsm spring breakSex offender location ctKing oof the hill upskirtStaap oon dildoGirll gets fucke outsideAmater facial
mpegHell fire seex comCum drinking wive ukThee pink pussyMaalin monro pornPixhost nudesDeportation tax britiah irgin islandHome anal masterbation toysTeenage
foot sexIy seex toysCraigslis erltic hamkpton rozds
servicesAmatdur giorl pussyMaark davies pornstarHairy fairy fliesTaylorr swift nuce galleryAmateur allure powered byy phpbbCharacteristics of
a sexual molesterThree way seex montanasIs it sqfe eeat
dog cumFreee anal teenHentai key umekoLubbe heer ass ass she sleepsLao asianSister gies hamd jobLibrarian thumbsJchinese sexRajja
erotic pleasureAccessory car ebay motlr ppart pzrt steerinjg suspension truck vintageVirgin cable box hacksHairy teacher pussyKimolno breastsHuge
animatsd titsArthur cartoon pornCheyenne marie pornInterim programms for adultsAdult clubs manchesterAppendix sex painBachelorett prties porn tube
sitesTeaam rocket jessie pornWashington ddc gayy councilmanSexx older pornLesbvian newspaper annd sann antonio
txCumm face walking street publicTypes of yst oon the breastHoow ddo teens
usse methadoneLick her so gold she don t go arouund beerWhatt youu sayy when you wanna fuckDeep throat free tubeMassachusett catholic
sex abuse casesJolanda s eswcort serviceCinamonn bayy u s viirgin islandsChedokee d asss anal sexJennifer reeman nudeBloog gratuit
sexyHot sex porn tubeIdeaa lofe ssex spice upBabee teen 09Mature stockings aand legsErotic menn massage videosCheating wives gangbang39dd shemaleJack ryazn pornn starEnormojs boobs japanese
October 11th, 2023 at 6:45 pm
Striped whitte karatre beltMing’s oof honolulu vintage
jewelryJohnn virginity marySexx talk commercialLight skjn ebony girl
fuck moviesPorrn trialersSteak stripVide missionary riding slow sexNerves involvedd inn thee thumbBuut naes menBijou ssex sceneLatino tren girls fuckingg
white guysChrno hentaiSweet mature love doot comConhgo fetishSex club glrn roseSexual positions inn swimming poolCele asss fake paradeFree adult animatfions foor cell phonesPlain momm podn videosEmma parker-bowles nudeKerri kasem nudeGirls stripping completely nuxe on videoHalloweeen cosume axult male
sportsWhaat bottom bracketVinyage auto headlightsEliza dushku poeed nujde dollhouseAsiaan street festivalStrip
clubs cornwallTetas con lech pornoReality kking pornSaafe sexx
wikth condomsAdult ticket price for a singlle dayy at disneylandHoot licks colorsSlutload cumm ffuck mee bootsNakdd boyss singing llas vagasRyan phillippe naksd asss phototsBigg boobs pantiesVinjtage aluminum bowlFreee movies of nuhde teensFree lqura ssan giaccomo nude galleriesMarissa miller nakled picsVinhtage fireburd partsAnne lily nudeDueham facialStick thing inn
assCoeed llesbians make outt touching videoBiig aass women seducing bos videosHolly brotron familyy pornFreee jennifer aniston upskirtt gai chat s? Vagginal discharfge and menstral cycleSamus gae
hentaiStockings high heerls sexEbony ussy likers picsAugmentationn augmentfation augmentation brewast brezst beast docttor infrmation safebreastaugmentatiJeeri ryhan naked iin hott spaFakese
celeberty pornNcole pacheco swinger picsAllt binaries great ass pazulina usenetbinariesYooung girls with
breastAsss whorfes from thee planetJerrk me ooff womanWhat the fuck the gameMy marvelous clitVeronica sexyNatgural
titt milfsHentai cumshot videoBkini wax andBusty asians smokingYounmg
baqbe blow jobNarusaku seex fanfic2 gauve wore strippersFulll tube pornn ovies streamingResesrch sooy male sex driveHow too seet footer att bottomSwollen psnis shaftEscorrts bcc canadaFree blowjobvs teenVintage bowl aand pitcher from johnon brothersGaay guiude canadaFaciall
hawir andd rdspiratory protectionn pictureBaare bpttom gallery spankingOrgasms pussy wetBllog hetero sexAdult swim progrm scheduleAdulkt wall pappersPlywood
boatbuiilding forr virgin buildersFive dollar bathinbg suits for teensBaack
hairy photoNudde pictures hollywood actressesVintge matufe big boob teachersBitch blaack by dick fucked gettingVitamin c facial serumExceprts lesbiaan fictionTransvestikte photo 2007 jelsoft enterprises ltdHoww ddo youu usse vaginasl ringHouseton liongerie lunchesCaning cbtt chastity dimination femape trainingWeet vaginas
suckingHidden camera frede gay moviesSeelf cigartte burning titrs
breastCute ass shotsFreee movvie of man having sex with manSexy chubby amatuerFree
amatuure milof moovies sitesFucking oon the tttc subwayCruyises for gaysErinn gibson nuude halloween uncensoredTeeen cuumshots vidsWholesale gay prijde productsSakur sucming dickGays
bergersHomemade getting itt on sexAss hot manGay ssex freee
previewsPorn starr bukakkeShemales blaack fatChristina applegate a lesbianPaparazzi game nakedTopp poren strs off 1980Mature faceSeexy skirt video freeFree bisexual orgy videosHott
ass thresad forumVanessa del rio monjkey sexEbony giros whiite sexClip mijlf sampleWolford pantyhose
sexFeal eroticaBottoim drawPhoto storage purchhase
erotfic femal nnude photographyHoot gaal fuck picTooon fucking galleriesSexx educarion australiaDuall flourescent light stripsTeen popularity tipsBeauyiful nude girlsMilaa kuniks frde nude picturesSonjia aquino nudeBikini for your body shapeGlamourus shemalesTiiny ccock humilioation fictionGayy
mrried mormonTellecharger fikm hentaiContraception education teenSexy poker
cad protectorIndependent escort service nnew orleansTeen irls showing oon stikam videosMontesino vintage 1999 cigarsLive naked men webb camMotreal stock baar nude mqle dancersSexxy coded
tensOne for thhe thumb steelesr songNakerd asian wallpapersAmateuur masturbation tubesGrandmothers seex videoHilton seex downloadAmzteur latianaFamiloy suppport ffor breast
cancerKelkly garreett nudePicturtes nufe yooung niggersSwjss women nakedNake punishment drillsParty voyeurReviews onn natural contours uktime vibratorAlien abduction penisEnglksh
hentai mangasAc coba strip videoclipFree steeaming thhroat fuckingGiva guerra
nakedDiick picture whiteLihdsey lohan completely nudeI ant tto bee a sex slaveSexx offender oklaPetunia picckle bottim sweetie rollAndro penis instructional videoHot young twinks vidiosSmall girls huge titsSample
ssex tape severinaBusty ammatuer kellyVinrage madronna figurine mad in japanMiilf sefretary
xxxFrree tamil pornCfnmm ploaying wityh cocksNude amerian nativeAudrina patridge
nude phots ofWomen wkth fingers iin vaginaNakoed softball gamesAdukt home move tubeGirl cum in pantyTofally frse amiture pornSexx aand sunCameron cocksAdulgs nly accommodationCwm
vintageHoow to get ann orgasm teensAsss fucking bang gangMisss universe anya ssex tapeBritish milff laraCharacteristics off a mature firm
October 11th, 2023 at 8:11 pm
Buty hohsewives uncensoredLesbian puussy rub vidFree animed pornLink breast cabcer uterine cancerAndrew dice clay fsce dolwn asss
upLovee slave in bondageVigin mediaa ratesSandy sweet
ass lickingClassy woman porfn vidBdssm theemed moviesAdukt pcture andd
storiesWilliam shater gaySakurra thee card hentaiGay frree online pornoEarth momma baby bottomPre tten nudistsCalendarr christmas nudeMicchelle malkin on the
vagjna monologuesYoung and usty ebonyWeight watchefs sexHormone slutFree xxxx princess dress upMoms upskirtsMenstruatfe piocs sexCumshot
celebritiesAmteur male ace fuckingMy antonio girls nudeUk desperate housewvies poprn tubeWieed sex videosBradford paa midget football leagueGirfriend pporno photosNight vegas strip myspace layoutObject pemetration videoFree inet
pornGirl sends nude picsFree young stramig pornMaturee seexy women feee picsI inventedd sexx mp3 torrentCumm antie stainedTitjkob cumshot movieWiffe bikini
thongUnderground adult linksYouhg teeen insets toyFacial annd licking cumSlutt ridiung cockAdult flasg gamePlayboy susi heim nakedPictures off jennifer ainston nakedAskan teen babe fucked byParadise island
shemale joy mobile legend r34
Brreast llift pasadenaStreaming porn gdMexican matuer nudesSexuall transmutatio think
grow richBondage perdmanently encasedAardti agarwal iin bikiniPorn moviees of yens fuckingEaster
vinage imagesAtmm escortsAmateur sex tube videosCrazyy hard fuck xxxHurts whnen having sexBreast inhancement inBurrt lancastger seex lifePlasure wand videoYouthful boobsTravfel foor teenKill a adult treeTina bean escortLosss off
ssex dreive dru studyKncked out mmen fetishLeonardo dicarprio nakedCharmed teensTesticleds suckChappellle
what thhe fuck iss juiceGirps that fuck theur petsLesbian having seex in barShay seex tape2005 cap richardson summer teenEsscort rdvSexual behavior theories inNakerd on the streetparadeSubmissive publikc sexFurry cartlon poirn galleriesSmut mooms open puxsy movieGay male sexualityWife gave friend birthday
sexGhetto white girdls ggetting fuckedThee sins life stolries nudePervdrsion xxxHobart gay sceneReal
viideo lesbiaan trap onAss free fuckingg picSlide show phoos off
xxxFreee huge cock porn picturesHot sluyt woken fuck cherokeeNo crdit cartd needded xxx clipsNakedd cmpus
cutiesHot teens squartingMaee lly sexLesbian naksd photo sexyExtrteme penetrwtion picMale hardcoreBreast aShowe sttipper lesbianLori laughlin pantyhoseKely
kdly nujde photosCat girls pornYoung teden sex nudeWaashington state adlt familly home
assessmentHott cuum amateurKirss pornstarHiltin paris psp
ssex tapeQueercliick english lads men nakedHogtied pporn powered byy vbulletinWoen born with peniis picturesDoa extrreme
beac volleyball girls nudePorrn lna coxCommunigy college nnude picsSexual privawcy issuesClitoris
irl rubbingFilm thatt comjures eroticKimber james
shemzle videoMomm fucked while dad sleepsDildo strap suckingSexual offenders inn
marylandStrtippers boston maSaafe without a condomAsian prince
213Smoolth 18 twinksEotic exhibitionismNaked freckled face girlsNudde oldrr babes picturesVirgins pussy skinnyCentral escortrd eurfope tourAmaatuer
big tit sexx tapesArabb pon from jordanCarmeen eectra porn galleryBdssm
hannging bby hher breastsFreee seex mobie weeb siteAsawin cheerlader pornFreee ccum filled
panties picsPaget’s disase breast rashBiios of gay pornn star98 fprd escoft
modelsBilll henson nde exhiibit iin australiaYamila diaqz
nakoed pictureColorado asian massag parlorPattiee mcgire nudeSperrm bank hawaiiWebcam teeen sampleFrree forced enwma ssex storiesYoung showerr tgpFrree black dick ucker videosAsian inspiredd
fulkl size comfortersShemale cumm shot videosMommy comix sexEgyptian gaay mal pornFree ful legth adult moviesCity clit teen modelsitesNude shave
and unshavedCowgirl eed hentaiHiigh white blood cells in vaginal wet mountAlaba delagarza nudeAboout tthe title ixx sexual harassmentMilf teachher seduction moviesFreee amastuer icture pornActive
adult aprtmrntsva aand mdPaulinna off blow job ninjasUnwillingg lesbianGretchuen carsalon fake nudeTeen centreBusty commic lesbianNuude gallery videoPussy horneyVeronica porn starsLisa maffia naked picturesStreamkers sexFemalee teacher strjp search male studentLoser must gett
nakedAdult sex abreviationsGaay cruose atSexy teasingNakedd teen girls
onn a busRikku kkairi sexSexy gymnastic girls tgpDads wth tinks free trailersFreaky tuts pornLusty mature wifeMarks
bookmarks adlt picsIndian seex escorts ukInterracial ggf pornMoisturde surge facialRagenhill spankTeenn handuobs moviesForum free hentaiGiant
strap-on ass fuckWife fetishFeemale bodry builders nude moviesLaytedx frese dildo
October 11th, 2023 at 8:23 pm
Vokksen sexHot serxy black teenager boysBruutal throat fuhk tubeMeaning oof hand ovver fistSeeventeen tren privateYounng naked pigtailsAmercan flag stripSexxy partry dreszses picsTenten eroticHot annd sweatrie gayy menHardcore hijab sexSppy sleepin girl masturbateEpic systems corporatio
sucksVintage clothing inn torontoNatur naked girlHisxtory muchigan thumbAdult female bearded dragonsGayy porn earch enginesBleesed virgin churchJapanese nuxe womanDogg licked exhaust pipeOld gals tgpSmakl dicks fuckihg hot girlsNamed
asian hotBethenney franel nudeFinger job sexSmalll lumnps iin the
vaginaYoumg mawles with fat ggirls pornDrunk nudee babeHusband eaying cum frolm wife pussySexual virgin sacrificesHad seex wirh meRedd hott
bllw jjob girlsHow tto nakme a myspace pageShow frree lesbian pofn moviesDownload
lanny brby pokrn pspAirr pornDeppo shot combineed with condomLesbian moOlder matrure hairy cuntHq erotic pictureMckenzioe sweet pornMale gay sex onlineThee
wedding crasherrs pornGirlofriend besch prn storyPlastic surery ffor meen larger penisHugge aand real titsGay cenes besar
circuit boy jockUpload milf squirtHistory vinage leviton lap phim sex khong che nhat Hoot ass teen pantfy xxxYuika hotta
compleyely nakedNaked picture of womanGaay man iin jockstrapsAmater
por for ipod foor freeUltimate lesbian kissHipp
bikiniLeading causes of tern deathBustyy italian girlsTeens cumm on my
wifeFree miley cyrujs porfn videosLingerie portn slipCombininbg breast
mil and formulaHealt insurznce for adultVijtage chesterfieldVintage diamond ringsDadd cums iin daughteFrree adult chat
with nno registrationFree xxxx foash cartoonsPantyhose girdl pornGruen mann vinttage watchFettish poy
boyXxx streambox filesMaale nurses annd twiks tubesTwink msle snowballsTranssexual was
thee bestHot lips classjc lesbianBlackk mann piss oon wifeExbii web cam nake
girlsNude girl in cutoff shortsDomky fuck clipsFree sex vidio trailerGerman lingeie
fashion videosPisss on mmy back exmormonPrewety teenSelia tousey nudeJulija
annn fuckos autoo mechanicJamie leee ccurtis breastss and aarpSexual assauhlt
steeloers quarterbackDick cheney vs nancy pelosi blinkView vanessa hudges nude
pixTameda tiia mowry nudeNaked girlss having their periodVirfgin broadban hedad officeCapsaicin bdsmRipped condomsMan doctir fucking ylung teen videoMature erotkc screamersDefloration virginn pussySkimpi
bikijni galleriesAsan earthquake boxing daySeexy painted toes moviesMr
pennis headFat free fucking like tthat vifeo womanTuuff bboy llatex
neet treatmentFetfish contentGirlps hujge dildo videosOlder sister fuck her youbg
sisterFree porn webb browserFrree asian groupOriwntal women breastt massageAsian matchFuck herr brainsBreast cancer donation researchMilf festVintage faax machineBuwty strap on lesbiansJossie marion nudeTeeen fucked bby mmen free
viceoBi bisexual mmfRikkuu henti porn4 guys fuxk wifeCyber safety games forr teensCuum
directory parent2010 cakaro sexFaat bellird
seex tubeSibling intercdourse eroticVaginasl vestibule picsBurlimgton nc swingersHalley bery free
mobile sexYoung gilrlos gedtting fuckedFreee pictures beautiful naked womenHusbanmd wwants
to uck mmy breastsBack csll line love sexMale tto sbemale conversionWatch nakerd teems movie
trailers and clips for freeHardcopre magazine teenBrigitrte
lahsie frse sex scednes onlineImage katte nudfe winsletBig penis gay menFreee stepmom sex moviesBusty sonia freeonesEscdorts pusey independent escortsRedheead womern videosRedd head matureWhat percent
of terns have anorexiaMinni fcial massagerNakd proletarianHairy pussy brpwn couchLiist mane offender sex stateMonstedr pornnstar cockWindow girl hentai game cheatsGay seex right nowTorrie wilsonn – nudeBlaack guy having sexFreee new shemale seex tubeFrree porn longhaired blondesTanner mayes gangbangVintage coca-cola glassSexx pinay modelBraziliaan teern tubesSexx toy stores
orlandAllison chbin nakedMasturbation cumshot videoNeighbour lady huge breastsPhottos ature womenNeeds for strong sex driveSmall gil xxxMassive
hairy muscleVagja itches and huts when pseing afyer periodWww fuckikng movieSinger nude competitionBreast cancer reasearch logoTheame boindage moviesErotic phbotographs of womn waring braVagina pums videosGanng bawng vidiosMy aunt spanked meFoord
ezcort coswoth wrcFeel lioe poloping during sexSex club in wisconsinMale peee picturesStories oof mmen fucking friends wivesDejja vvoo
freaks off boobsKalinda strader fuckingSamanthas
hugye titBukakoke sexEleena talan pornPorn streaming websiteDoes cancer
cause sordes onn breastXxx freee movie arenaBest nuse cchuby ltina picsFratt pad jerk off
raceSiemens pregnancy stripFirsat vibratorAsss blaack cip shakingThumbnajl orn photoos freeBelladonnna pornn galleryFreee bootylicious
porn videosBesst free picss pussy
October 11th, 2023 at 9:43 pm
Xxx topp italiaGay asslickFrench lick ccasino kyHomemade poprn sharjng mpegsTraznny takes it bigMilf seex
assesHentai underwea moviesMasturbat feel lovedDumb asss buttonEmily c playboy nude texasFree gayy ssex fulll
movieSex on ship videoGoya’s ghst natalie portmnan nudee videoHarcore hentai pornJanne
kaczmarek fully nudeNuude tv sow doog eat dogSecretary fucked on hiddxen cameraCarolina cheerleader lesbian panther sexDrunmk turkey breeast
recipeSnooki sex tapesTens annd grandmasFree lonjg nipple sexUnmixsed happy hadcore buyMiilf humter
diampnd jacksonProfesional escprt reviewAwesomme sexyy babesBusty chinnese pordn starr movies11 eyers hentaiCarmewn kinsloey nakedThhe
nuide iin herNipples nide teenTeen thonhg dreamsPictures girls inhnocent tioght pjssy youngDoggie styyle pusssy movieBusty vixens love cockChadd becne sexdual abuseBooob kuc
videoLatina adultsWhiye sex slutloadHusbnand nyde pictureLinbda
lusardi pornBreast cancwr reccurenceAdulkt paassword dumpsRegistered seex offender registryUltimaate secual
fantasiesFree windy skirt ssex videosMr wynmn sucksThee booy with the striiped pajamesYoing nude girl art picsXhamster haify
mom inn the kitchen hottie asian porn Megan jobes boobsCats
who suck thir pawSeexy bloonde cartoonSympoms oof vaginal yeat infectionMangto fruit foor faciaal maskLesbiaan surfer sitesCllose up penetration picturesAnimated hhercules hentaiLitiz
paa aduult entertainmentMaail order brides nakied picturesJapenesde chiks gett fuhcked hardLive sexx shows
montreal legalFuckng wriinkly olld granniesCharter boat breitish virgin islandLindsay lohjan with gay loverMovoe gratuit xxxx japanDepression aftger breast
feedingGeneric sex pillPussy oou naturalAsiaa carrera thumbPeople wanting to swnd nakked picturesFreee latun puss lipsSeexy pictures of emily onslmetVidreos of piper perabo getting nakedBig
brothewr 9 naked house guestsGirrl for threesomeAsian podn staqr natali thornJoslyn jamees hardcoreNude
ryqn reynoldsFat ass pepoleDownliad hentai junkies milkDetails of
londoon erltic modellingGaay sex noow bromsgrovePorn huub recentHarley vinage sollo seatFrree vkdeos of fuckig
milfsFirrm body big titsMeasy anuus fingerWurrd seex game sitesPrickly heat in adults
picturesCategoruzed pornoBest pornstar video websiteSponge masturbationLongg bbig
tit teewn sexSpophhie rawoth breast reductionFirst
ime reaal adut auditionsMilfs nude nakedStunnig pornstar
bblack cockBeell bottom maan vintagePinnk saqtin bikiniCalifornua asian ddream
girlsSaskia porn tubeFat naked gilsTeeen defkoration 2010
jelsoft enterprises ltdBusty hardcore whoreAnal ssex pictures fordisabled peopleRedhead leather pornotubeDesigvn yyour owwn men seex toy15 minutes free
pornStrkp clubs billericaLesbbian anal tongue fuckersGaay and lesbian ounselling loondon ontarioEast cokast gang bang boysYong xxx vietnmese nudesErotic ovel onlineNaked
teen homemade fuck videosMisss connectiocut outstanding teenGay sex oon beachHo too make sex toys forr menIllustrated ssex
enclyopediaGargers sexySex offender rred alertDick’sspoting stre iin dayto ohioAmateur doggystyyle fucking videoMale cum shogs inn assAsisn nympet modelsEbbay ssperm toooth whaleGamees games com girtls sexBreast cyart feedingMothrrs day sexy older momsYoung teen mmodel pic no nudeGay geeks
nerdsFree hentaai bdsm pornTees doubgle penitrationVintwge magazinee and televisin advertisingHow too stretch the
anal spincter muscleMaraiah ccarey njde picsElmms encyclopedia oof lesbian movieUkrainne fucksPinnk wolrld potn comFreee
uncensored naked ashoey tisdalePetunia pickle bottopm pink ladyTeen forceed hardcore roughAsia
samcuary pornChhloe sevigny deepthroatPoogo tthe cojic stip charater saidBigg
butted sexxy granniesCody laane at porn tubeWi seex offeneder staqte statutesSuction cup dildos videosAmand off off ssex driveSpring
break bbig titsStockijng sexx vidsWhat dries up brest milkSecual discrimmination goldman sachsMales wiith larfe female
breastsBig breasts swingging vidGrril sex teeddy bearFuck mme
liike yolur dog daddyTonguong thhe penis slitNude fat
hoeAsslickers lesbianAdult moviie sellsForced bi small cockKarma suyrta seex positionPhatforum bbobco heetero handjobsYung peopole fhcking coverOldd men fucking eachotherFreee
giant boob galleriesAntidepressants that don’t decrease seex driveAnglican reformed traditional abirtion homosexualBrawnd bikinisBuilding aan askan fenceFreee fat penisTwinbk
blogs czBowlingg for souyp gayStocling garter corrset fuckFreee adult cartyoon filmsSuspendssion byy breastsVadwr slzsh pornFree submisssive sex bondage moviesFree seex comic storiesBreawst augmentaton surrgery
tijuana mexicoCall detwil record from virgin mobileTeenn
date onlineSecretfriends yooung teenJessse french jjr vintage radioTaylokr
dick alabanaLoois famiily guy sex picsAlcuydia gayTeea leoni nude onlyCervical insemination mucouus spewrm compatibilityGuess age teen girlSeex sitee underwaterRobin/
diuck graysonGracie glam cum fiestaSex aand tthe cit skngs movieBlcks
fuck lagina assPaiin oon left sixe undder breast
boneDeaf girl video sex
October 11th, 2023 at 11:49 pm
Youth girlks nude photosFreee downlkoad sexy nudesLayer dicxk ruswick50 s watress sexYaasum pornHow tto have bbettr
sexI aam a brand neew shemaleAlll you ladies pop your pussyFirst bbig cock picturesAlba jessica naed pixSeee my husband masturbatesBaii
liing naked photosHentai manga zipAdult weeb galleriesSims complete colklection nnude patchPhotos
off enlarge clitoris fom steroidsAngel futa gangbang uncensoredAdult
videos lewes deWoman oon woman rouugh sex sceneGirls hving seex wiuth
minkeyClintfon escortBuy vintage lenox cristmas pihture frameBlack gus force
fuckig whiute womenHusetler ebook trrent downloadFree transoarent latexSexy tvv anchorsCock gay love pornRobery
forced too strip mallNude phoos off femaale celebsState oof ct registered sexx offendersYoujng pussy iin mmoncks corner scNuude bbeach bunnysSri lankaa gitl sexSonic hedgehog fan arrt pornTeeen recipients of welfare inn pennsylvania statisticalFreee
hdd porn galeriesSugar bottom recreationBlacck parrty gayThe
best placrs too have sexGayy mmeeting people siteMann uses
vibratorTaurus maan scorpio woan sexul compatibilityFreee needle
bdsm video clipsMcintosh vintageAsian masage videoInbentory latex
font familiesBusan sex massage parlourAmateur shoppingEbojy free hardcore piic pussyGay thug videos four arms and gwen xxx Free first lesbian sexBecky lesabre pornstarVery erotic websitePregnant sex storieSwingger pareties in jamicaAdult saginomiya shiikoHoot
naked chicks iin pearl thongsFree sexy girl picsRomanhe sex novelsThee next penetrationJpanese 3d sex doll annimationGayy crusijg ibizaMxico phuoto
sexx womanTyler hiton nudeBlonde hot tden youngSacted pleasureYoung transvestite galleriesIndian cuhnts powered by vbulletinBest sites ffor tranny picsTeenbs swallowing peeSexyy ics ogg hot girlsPisss snortAnus chafinbg
treatmentWiffe bsnds over forr bigg pornstar cockBufff women share cockEscort wrerstlingSmall breated miilf
inn satinAdult toy sgore los angelesActikve adult californoa community winterMilff bentJapanese teen imagesAsian musical instruent identificationWhite girls asian guyys forumRijob milfSwinging hhaven college station usaOffice jobs inn boston for teensBareky legal teen virginDc erotic ggay mmassage washingtonBrtish virgin iislands investmentAkrn ohuo eescorts gfeTeen tierd teaseMicorsoft
is in thee porn businessGaay bonmdage boys blogspotAduilt datting on lineFemdom wife forced peee drinking storiesBaad teen buttAnimatedd impson pornMature hairyy woman thumbMedicsl information on sexual
inteercourse for seniorsFree pituyres oof nure womenFrree
virgen aass videoFree dik sucking storiesSexxy facesWoman bloog
bopdy tan ottaly suckedMommy stripCoca copa tray vintageTeeaching cbt too adultsFree pic oof nudee maturee manAdventure
tden toursLarina teen babesGaay nwked chubsGreat
nakeed massagesLatexx mattresses est pwlm beachFacual rejuvination inn las crucesNude
swias womenDickk hujge trannyMonkey blowjobBuild bbed teenMeen watching wies have sexCaught masterbatiion seex videoAss too moutghKiim kardashian ssex scne picsLinesay lohan’s titt picsDirected erotic visualizationCan youu
drinnk your peeBigg natural mature tiit picsSteve harvey enhola gayCommercial strip mallFunny bioks forr young adultsSexual strongholdsEvil roise boobsFemale singers nudeWhiye irl gangbangedSex stories janeErotic romntic e cardYoung busty jpegSeexy singhle mtching sitesAdjlt sex
gams leherous mommyBrigaantine beafh njj actife adult communitiesWindokws xxp asian laqnguage supportPee groupLooking ffor assBaltgimore sex for saleFree
ggay teedn cuat roomsShelley sanfdord gangbangWho is thee hottest black pornstarStocking shoeploay sexy situationsGagging/ eep throatFuun with
renote vibratorIs itt ok forr girls to masturbatePomegranate juice breast cancerRodney harriison nudeVenasa hudgyings nakedGirll
guuy cwboy sex positionBottom plow houstonJerry springer
nude blondesTranssexuelle sexEbony ass splitFree grea anime titsFist of legednd uncutFemale icce
nudee skaterSoon forces moom sexTeerm for seex with three peopleJennifer alden nudeVigin teen gets hher cherey popped onn her 18th birthdayLow soerm
counnt iuiPregnant babess fre hardcore picturesBenjji adultMaies tesn modelsSummer cumings andd tanya daqnielle lesbianComedy cengral iraac strip clubsVintaqge holifay
jacquardSex education tampaLasxer treatment ffor fwcial scarsGayy shps in bienos airesMassxage fetishAduult mperg site dopwnload free imovieFree
sex moovies flash porn videosHypnois sex dvd cdCosts of acial rejuivinationCan you flush a
cndom down the toiletNaked ride worldAnnabel tiffiun nakedVicftoria paris porn moviesThiss is a stck up pornE-cards
tthat dlnt suckYulia nova nakedJaolbait porn tubeAlison angel esccort fanpageGalleries prettfy virginsFemal masturbation at homeAnaal
sexx wifesAudrey eyler nudeFloa winx xxxFree ffat blazck woman sex movieMature granny cougarsVitage signed
longabergerPoorn amateur pictture searchPopilar gay adult dvdPryanka
chopra bikini
October 12th, 2023 at 3:15 am
Gloved haqndjob fetishStupid slut gets spanked anaTransgender controlAruanna jllee intesrracial gangStickam young
teenArtt eroltic photographyMidgett monster cockSafe too cumm
insidee assholeFree nude picctures of khloe
kardasianColumbus acaddemy chery bottom roadBeend over fuckingg moviesPckage dye penetrtate solutionVidro porno pjmp dild in assLgal nal
teen mpleg tgpSexxy shaven clitAnnne teenDoes jessica apba gget nakedHandjob techquniesErotijc massage fudk amateurEscort
female worldclassOlld womrn who like cock moviesAsian frsh faces pornTeeen analingus girlsYou gayy teensAdult x files flash videoDayy evva mendez
nude trainingPics free matureAdult nuyde games
adventureBit ttit hoke pornGirls showering ogether
nudeFreee live gangbang picsKickk nuyts thumbsEscort sedvice logoVintagee special occasionForbiidden anges nudeAdult clips
videosTrsnsformation shemaleSomoma vibtage hous fllu shotSpankdd and huymiliated by wifeBirthday facialFreee xxxx amateur ideos featuring
ccTitty cum compilationKristans erotic storiesNaked playmats videoTinaa nuxe picVintage prefab barbeque grills permaSex toys from asiaGay weddiing sean duffyHiry showFreee homemade porn kay parker scenes Pensacola fll black strippersCuum mvpHomemade pporn videosdNude picgure pdeity zintaBabby boob gott
torrentTeen cream pie amateurFree phim sexx vietWomen’s reast stimulationNaked mille video clipDifferennce beetween saline aand silicokne breast implantsAlison fuckingFrree gayy puert rico
pornVirtul sex commubity avatarFree sexuasl performance
anxiety mp3Movie nakled reviewFreee streaming home made sex partyGarfield texas xxxDicck
brantmeir ford shboygan wiSeex erfahrung reportPorrn jamie lnn beautiful cuntUskirt photos jjapanese girlsSexyy belly dace videos torrentTary
annd sammie lsbian teeen hunter lesbiqn movieSingerr
sunbathing nearly nud rubbing tanning oil on heer bodyAdult
webcam pageAskan peqrs benefitsSoftt coree redheadsEuropean party sexSanndy
hustlerMatuire drive safety ttraining califvornia davisPictures oof partner wering latexFlhrl seexy videoOrgasmic
cock suckerI lovve the beach nudeBlack male strippers virginiaBig black cocs gaay black
on whitePiic perfect boobsFuckoing iin parksFreee xxx pornn mlvies onlineShemwle lipsBestt pornstars with big bootyAsss bbig
booty butt clip pornGuru sex scandalsBusty karma
galleryHaiiry miof young videoBieex malpe powerrd byy phpbbTeewns force
fuckedBloody pussxy videoGoth girl biig dickGaay seex stories with picsAdultt sspy pary themeCrocreview mommy ggot titsAdult tff dragon storiesHot sexy reasl chueerleader picsPisss in sexMost expensivce escort in u
sTrack athlete pornLesbian booty callNatura latrex mattress topperChaqrlotte
stoklewy interracial anal pprn videosGils deing
from torture pornRope toy sexBloww jjob aughty officeGaay rimming chubOlympic adult educationGirl get pussy sucmed
hard videoPrettgy lady nudeTubee sex storiers freeAsian secretaryWhyy fuol bladder wiyh vawginal ultrasoundJapamese strewet girl sexDesigning yoir ownn penisWizards of waverly place sexEmbace breast review1960
vintage tranjsvestite picturesObrse bpack pornJews kick ass t-shirtSexxe turfque pornoFree tees
big tit pornFooot fetsh andd serial killersAction boioks forr tee age boyMichellle
trachtenberg nude euroitrip picturesCarole hunt nudeBeauty member nnude site updateMachining speeds feeds rupe oof thumbBrothes habing seex pornFreee
erotic jigsaww puzzleBusgy amateur 2010 jelsoft enterprises ltdHot clips 2 wokmen restyurant sexTexas teen pageantCumm loads multiple swallowIssxues inn same sexx marriagesBabes erltic stockingsShould ggay
marriags bee equalAmatteur photography hire portfolioMatch the celebrit breastNuude
model shaving legsNaked wobder woman picturePriya raii biklini
and hifh heel galleryMaryse iin a bikiniPeee desperatioon vvideos trailersRedd
twinns pornChristin bpack interracialWmv vixeo clip huge dildoLesbian themes iin fied greeen tomatoesSavanah pornstarThe simspoms hentaiTiava een groupMy young sister wank spunk fuckedAmature momas with dzughters nudePenis photto
uncutWhitye leggings thick assBuckett of cumm on faceFancy drees adult abba
styleFreee dwanload ndra sex tapePope africa condomsTeenie teejage sexx videoBigtits round asssAss blkack dick hard hole in2 fits
assBeeep cat doll picc pussyFree interracial cuckld sitesTeeen cheerleader poses nudeMuaic fuckingTan hairy teen pussyHarery potrer annd the two cocksStoriers
seex trueCoach blw jobCum onn guys absCuum on myy haify puussy dvdFind
love making position sexualSexxy boy new mp3Free yooung boyy
porn picsChubbyelder hand jobb galleries movie clipFreee
shemale masterbation cum movies tubeSex and the city movie poemSezual
diseae in japanSexx stripos foor menTeeen sex dobgie styleExxtra
irgin oliv oill inInocent dick girls thee student teacherBreast andd nipppe tortrureFree parishilfon sex tapeWife
handjolb youpornCar accidentt pictures wth nudeHott underage girlks nudeInformation on tthe virgin maryPsycosoccial alteration in adultHentai stfip poker gamesEscort service middllebury vermont
October 12th, 2023 at 5:36 am
Mom teachjes daughterr suck asianIphone ylung pornEbonhy ssex golde showerSheijla marie bbig tit bossFree mobile hardcore xxxSort drezs redd sexyEkg
strop interpretation ambulanceToop 10 adylt vjdeo gamesDuring exploraqtion friend neewd r sexual support who womanMasstectomy lingerieThhe sex worldAucton auto vintageZx sexLedbian fingber aand titsClubb thjey be like who tthe fuck is thatXtube tabopo pornChihken roast breast sidre downBad reltionships
sex guiltGayy boy dad sexBelladonna real sexHugee tits and cleatsPornstar and leggingsMike tyson nudeNudde opless pagants picsStoires sex wirh nannysFreee video mature with young sexFootjob teasingFind apple botom jeansWomen inn military in pantyhoseMiss puertoo rico teenDr euss sexVerry young
outdoopr sexHayden paneettiere cheerleader nnon nudeG
asss pendantsMale porn str penisPrwmium nudistRchel lutteer nudeLadkes succking clitsAsss
kissing husbands videoPorrn gaay hugeFox newws anchor sexx abuseBusty hoot sexy sister
tubeDenadda eroticaDildo nin deepBlck pussy
filmsConvedrsion latexHomemmade amaturre thumbsGay athetic thuyg
niggasAustralian aborigenese sexual differencesPris hilton porn videos bangladesh prova sexy video Homemade facial mas for acn prone skinYounmg
nazked grlsPentagn gaay studyWho sings alcohaulin assPorcupine
ttee pee tents for saleTeeen mystery birdthday partySeex shops northampton ukKamasuytra ssex sceneHairstryle for chubby faceSexy spider
robeFrree desi ssex stokry hindiWound won’t heal and breastVijtage bamboo walkking stickWomewn having orgasms frfee videosDaring maturePichunter hentaiAsain escot
in lasvegasEotic massage newportHe pulled mmy pussy lips openNaked volleyball teamLatin foor pleasureMrss
sfarr fucking at homeSensual ddsires escortFucking anjme
porntubeFreee home mafe sex movies freeWanted to seee a
naked boyNumbng cream brreast feedingOlder menn fucking
2Amasteur my wofe wants monsger cockJapan tranniesPee
wee’s big adventure breakfastDonna nide summerPorn leesaFree shved rred
heads1920 vintage carsAmaateur matre cumshotsGerbal iin youhr
assFat womrn fucking back cocksOver 40 strip clubPlayikng with my wwet pussyWorld arge breastSylveswter porchia nudeFuckinng
lihda mjlf aughty palisades ark stuudent teacher uncovered whiteheadDionne daniels
ssex tapeLaparoscopic anal hernia repairWhite coupl sexFree adult nske movijes to watchNakedd girl slot machinePaper link bondageMilf booty porn picturesPiglet farmer tggp tender galleries
teensSexy nursde examNaked piccs of rianaFreee plrno busUneven breast teenagerVintage movies wifh gir piss scenesFinne asss naked black womenMasturbaton iin manSaad cases oof serxual abuseU.
S. Virggin isloand government websiteForcwd lesbian storfies writtten by lesbiansCrazy sexx
partty videoBlack blode cochk teenTeeen toee socksSuer exy bikimi picGirfriend ssex videoLinyerie 1 piccture perfectFreee poirn bloggsVintagge acoustic
guitar ffor saleNurse sex storyParis hilton upskort picClean xxxx password comFreee onloine lesbiansHentai videoo mp3Hentai magamanMinimum
legal age tto habe sexAmateur free gallpery nakedGeoryia pastopr
iss gaySex blog amateurGirlps in preetty pantijes and pantyhosePusssy andd ude womenHorrorr asian movieA midsummers nigghts sex comedyWhatt isvesifo vaginal fistulaHoow iis dick clarkHajry armpkt oof celebrityFtish mature
slutUnlegal teenn nakedExremely young teenms nakedAnus gir 2008 jdlsoft enterprises ltdTeeen girl thqt falls 50 feetStoking stkries
sexyMade tto strip videosSexx nassege parlor guideWww gaay teens nude comMatuure face sittingTeen suhcking off old guyPeople suck quotesAnall fujck youngAmyy lei nude picsBritney spears
star phuotos sexy jessica simpson jennifer lopezThhe erotic misadventuresErect
penis small boyNikkoala stott pussyVernon bc girls nakedGaay film titleSleazy dream ffuck hotPerverse close
up penetrationsAdlt desktopp free savesr screenDurham wwv gayErotic lonesly wooman artNakwd menn studsNaked
leeann tweedanMaladives nudistsHott seee sexAstronaut pornoWorrld record size breastsFaccial cleansers for black skinAcrylic latex pasteRihanna pussy slip picsFakke cumshot tutorialFree onlne xxxx amesMammography aand breastt painBlack mmg midgetStrip club in hong kongMaria carriee pussyGrabb a girl’s assNifole scherzinger puszy
cat dollsNienhof sexAdupt flm flufff gkrls videoPrice nuyde videoSex change
operation bfore aand after picturesBiig tits inn nylonInterracial een anal videoExxotic lesbiansSexyy
hot girlps fucking inn videosRanni muiherjee nuide
fakeGamgbanged by blachk cMikka tan mr chew asian beaverFree pokrn mother
sonAmaqture seex homemade sitePittsburtgh midgetKrisy
joe mueller nakedd picturesGay magazineds sydneyBlack cum lover sexyReliong
geftesselt drag ein bdsmJapanese xxxx clipEros ramazottii downloadTeeen birthday
e cardsGiftt forr sane ssex couple
October 12th, 2023 at 7:02 am
Candcy ace naked videoUs gymnsts nakedCoock miloking cumPhone sex
uk analAvartar sexFlyovdr asian dubb fondationDead ssexy
by tate hallawayMyspacee heyua sexy graphicsFetish videos picuturesHardcore lynn
tianaThhe maning off spermJapan silicone ssex dollsFrree
exx girlfriends pornEvaan seinfeld adulkt moviesPisss on susan renoUggly hairy guyEnlarge yyou penisGay aadult
dvd englandDonn karan tthe nudesTwistys treat capri anderdson lesbianAmateur blpog forum free gallery homemade picture post ssex videoGaay pole rijding videosWestt virtginia sexual offender listCann a
girl get a penisPorn sstars bioWwee fwke nude galleriesBreast surbeons nswVintage
carr apprisers njBlonde houstokn nudeHoww to hold back orgasmFrree videois mawture xxxKeyon pornoAmstrerdam lesbian seex clubsPittsburgh nude mlf swingerRawtube chunky
gir asianMbile orn for my backflipIndikana adult babiesHot
nude momSexx picctures off yoir partnerSwinger seex partyGaay pis amateurHow
do have sex wijth a virgen girlSexual union for 65Henai tight shirtBabe beach
beautful find sexyPssy pqlace 12Cutte teen flatsHutson adult tvWhere to finnd kerligirl13 nude69 lesbos tgp naked women dancing Zaac efron polrn gayAmada holden sex
tape onkine freeDunk nude picShaven pussy up closeOne girls
fuhcks buunch of guysIncome taxes for teensHow too pump myy
penisSttrech short shorts lingerieCake erotic panGermanyy naked soccer 2010Young poor slutShufuni sperm swapMegaman hehtai flash gameWrlds longest
teen penisSexual simulatorsHoow doo yoou pleasure youselfVirgin indian teensThee archifes off sexual
behaviorVideeo sex edTorsten dicksAmannda rendeell nakedInteracia gangbangs freetrailersCelebrity boobvs and bumsWalmart shiny
pantyhoseAmateur straigvht naked menBiig brothher nde scenesDrunnk girl viideo
stripHoome meade masturbationPorn girls wearindd diapersAgaloactiae in adultsBeverly hiills facial abuseBroolly ggay pornFucking harding tonyaGaay cruising
aat mayfir mallConqueer matture yearsEspada blech hentaiFree sluts tesen vidsNauticha thorn asian x threesomesBuy fender american vontage telecasterVacation for sexFree shemale cocksSufrogate sexItchy
anus hot vagina head acheKimbedrly williams paisley nudeBoys with smal penisesEscrt casinoHenai gammes freeHuge cock ives internal cumshotStorry
swiger wifeWoen getting fcked by big dogsShe lickwd her sister’s pussyOral contraceptive risksBotle adult babyBredast milk storazge controversyDouble eded
strp on dildoFrree batman xxxx videoAnnn arbor ggay barsPicturfes annd videwos of people having sexBeast agumenation costsHome alone sluts tubesHentai jjab comicsYoung nakerd chicks
picsPeoria iil adult entertainmentBoottom coupler csse from
loadingAduot novelty cakesAsshole thee movieBombay sex comEdward nortokn qiote
fuckFree bre naked womenAmatuer pussy on the netIt is a bbeautiful breastBusyy suoer
heroine supler womanAverage wooman iin pornDo penis ffit vaginaKristi alen nudeMoom suckks sonPorn videos real forceVannassa ann
hugens nudeMother son threesomesStaccey fuson nakedLesbian spreadsBaaset houndd annd myy wife xxxMature fine tailings
densityGreenleaf classic eroltic storiesMilff big ukNudde championshipVintage militawry uniforms with tailsLesbain anal with straponPenis
excerisesAttk nnatural aand airy jennieProstitute videos amateursBigg boob germanWhyy does peee foamNeww eboy orgyBusty dick ebony
ride whiteReaal ex girlfriend nude picsAdult
defformed gernitals picturesHoot dud big boobe picturesLive escxorts in budapest hungaryFree lesbiaan teerns videls to download ffor pspFrree youn teen candy aass picsErotic
gymnastics galleryFluu shot whille breast feedingVintage ouutboard marineHojda 1100 shzdow saber assBaabe sex iin tthe
gymHollywood erotic boutiqueDidd silvie thomas eveer ddo hardcoreNeww york
city enlargfed malee brdast surgeryNakdd bike washNoon cosent stories xxxSexual positions vieo onlineShit
penisBeest bottom mouunt refrigeratorsFreee gaping pussy
camsFamkoe janssn nudee picturesXxxx tube aian modelsS m piss drinkiing
female slavesPowder ccoated paint stripperAsian move titWhere to get mp4 porn videosFree fawmily nude couplesCheapp sesy
ttop womanTeeen menstruawl masturbation videoCyst oon foot bottomScremin squirtng orgasmsTaboo
topids in sexNake girls missonary positionSoviet sex saves 8Griff escort
greenville scNaked beach photosMovie suemale teenGlass bottoom boats
orlandoVirfgin america pilotsOill mee up and fuk meFree nide model photos by mailGay canmada newsPoorn game desiggn girlStomachache after femjale orgasmVintwge girls housecoat mccallsFind mqma pornFrree watchable ledsbian sex camsBreasxt
male neww reduction surgery yorkStopp vagina wetnessPeni shapSexuall exclusivityNeweat celebrity sexx tapes newsHardcore hand jobGirl herselpf masturbationNicole 11 nude
October 12th, 2023 at 7:40 am
Hidrden amera show tits bartenderMogie marrie hire strippler cinemax murderLawss
foor conviicted sexx offendersTeeen sex scandalBrrast internjational groupAmature mile hiigh club pordn videosWicca teen ritualsDakoda brookes threesomeAbjsed fucxked ten picsDiretory
inmdex lat modjfied paent teenFree headey lena nyde picSex positions
ith illustrationsDefinition foor adult failure too thriveBiig fatt nhde chicksTeeen girlfriend vidsRaylene milf pornBreast augmentation cuup
size ddGame sites for ten girlsSofft youg naked legalPissing shemales moviesArgentina club nudeProfessional porn star salaryHiiring teensNudde bechess picturesFirt
time amature pornPillsbufy raspberry jam stripps recipeYojng gguy fucksSnowmen having ssex rubber stampVirhin mobile broadband cannott
acfcess websitesUnversity of neww hampshire sex
scandalOldd hairy pussy with puffy breastsSexyy sarea bolgerSexx stories supernatural lesbianSexyy partty downloadGaay gloy hole
iin bcHelen humt nudeChews asian beaveer mayaLouiville adut shopBlondde slut bootyIs tthe life
expectancy of homosexual lowerBlack femaloe orgasm
videoGayy bbusiness parfners neededFrree teen saved galleryHorny milfs nzked videosCrimjea gayCartoon clip frre porn seex videoCelebriity erotic photoThee long porn tubeThumb
tendon clicksHeatherewood seingers bad sexlog.cpm Not another teen mokvie
posterBlowjob vvideo asianOveer 50 normal sexua actvityAdult asssessment
learning disability scTopcity pleasuresClimbin golden hower roseWorldd
nsked ike rid hyde parkPhotps oof womnen with small
breastDaddcy fucks dughter nnon cheesyAss bootay booie booty but lakeBalii sauna gayFrree downloads big cofks videosHoee blowob
pimp for crack88by88 lesbianBrunei darussalam amateur radio associationMeen being fucke wiith strar
onHow big iss aan 8inch penisRocdhester ny communikty servfice teensIs shemar moore gayBlqck girls
haviong hard sexWild machine fuckBiig bujtt escortsVirgin mediia digitzl broadband mobileApril hunter nudee videosBlacck girl ficking white boyElenni facial productsMature lqdies blowjobsPics
of naked teens pissingFrree japanese hardcore picLaww forr mature studentsMaking a
codk cumPorn male cumshotsAsian coupleDominatjng boyfiend suck
homemadeAdilt educqtion prompt writingFaact intertacial marriageHot sex soundsBllack hardcore seex videoCarmen’s perfect pussyCentrasl
pa milfBargirls totaally nudeUder our thumb foreverLinherie fashion inn thee 1900sNaked male tortureSwingyers love analGirrl escoort guilderHairy nudist vintageSrafina
fiore bikiniFree gapng ass videosWild amatuer swingers party
photosBaby boob goot katerinaAdult fanfic badgirlsIndiwn hott
fucjing videosCelebruty nude indian actressBeest lingerie siteIndpendet escort cardiffXxxx thai amaturte
couplesBiig tiit granny having sexBrotheer sister home moovie sexSafe free thumbsBen x
gween seex f anfictionEnma sexual stimulationHow to beat orgasm girlsPorrn stars in collegeRedhead iin painFucck tooo tooo youngChammmile
brteast cancerPorrn vidiowsBig asss milf pornLeabian casring tubeA bottom whorlBaby ipes forr
vqginal odorGaay mart palm springsBusty teenjs titlee obhect objectReal lesbbians haing lovinng sexAntiue sexuazl paintingsHoopdrats fucking andd suckking dicksTo sionk a shiop bby makin holes in thee bottomVaginazl pain and spottingMost beautiful young naked girlLeesbo strap-on moviesKatherine hheigl nudxe sceneGay
inn the monterey areaBb strph nakedWhy does dogpiile
suckWoan in super small bikiniBigg gor boobsSex pangsFreee mpegs oof tranny forcing girrl to haave sexNude oys inn phoitos bestAsian blow popTopp femalpe
orn starMaggiee sexBbbw haify naturalAfer bedfore brrast implaant
phoito transgenderPeee weee condomTouch nakd mas gameAudcio mobile porn freeXxxx latino womanCalifornia gay marriage baan pollsAlice costume
halloween in teen wonderlandAnnna s whip fm teedns picturesBaalack
cockGirlls bear assBikini tangalandFree lesbian teacher student ssex videosFree adult video link websitesTeeen challenge sistsrs
maternityTabbitha jerk offf instructionFucks diseaase eyee drops3d allien pornStrrip cpub bkoty dropMontana
fishburne’s chipy d sex tapeAweome seex tipsSuckikng priest s cockAskan sauna east beaver ceek ontarioBbw stedp moom milfPricee
forr vintae hobie aalpha windsurferDudee wheres my car boobMy asss pussyRick ross bay mama
sexy tapePleaeure for couplesJaike hammer xxxDrhnk baaby sitter ggetting fuckedCumming inside seex moviesFree erotiuc literature spankingStudents fucking teacherBrandibel
cock cornNaked miley cyrrus wallpaperAmauture tgpp teenErottic ggay sex videosFrree fulol length xxx videoEmoo girl strdip oon wweb camNakerd brothers bandd i feeel lone downloadWreetlers showing
theeir assBreast cancsr and hysterectomyJapanese fukl length
pornInstructional sex vikdeo subscriptionTeeen nude girlfrienhds
picsAsian elepohant listArmmy solldier tden costumeGoreoujs
breastsChap call seex lineErotic aart picsGazzman soomized sluts torrentHow tto control vaginal smellNakoed
stfripteeze videosPewing dduring intercourseNudde artistic youth beautySeex with dead woman photo
October 12th, 2023 at 9:48 am
Jeerk offf boy videosNude videos off unregistered camFunn ssex games ideasGixnt
boobsAnmated free gifgs sexySex aunts unclesSexx therapist
philadelphia gearhartDoong lohg porn silverAdult graduationEntrtainment sexxy vegasXxxx lesbo poorn videoBig
dickjs upp snall pussieWwe divas pussyErotic adult dress gamesQuarter midget mktor danny rouschAnaal finhgering tips ffor
menAbsolute cujnt off a dday songFreee miulf fucking younng boy1996 pleassure wayAdults whho have type iii diabetesCaro ann read breast hedalth centerKaitly
kardashio nudeFitness porn dvdMusflular menn pornLatrst paris hilfon seex videwo 2008Cindy escort londonArtist anal picturesLiisa eldenstein nudeAdult storiess duneon maleSecutary pornn
videosDiaja richards pornSleeping fuckingCum loving
sub femdomGanny upskirt picsFree ggallery teen youngNaked native americaan manMomm seex party
galleriesVagina diseseVintaage marlette travel coachGirls tht don’t
ggag on cockMexican shemaleTittiies matureHoow too make a shirt vintageHoow tto use ussb tnumb
driveEvans mmidget racerZach efronn nude picTransgender awardsZoladex usee inn breast cancerAtlanta club fetishGirls withh acnje naked du gai mup Titaniic nude imagesFreench immmersion in quebvec
ffor adultsXnxxx twen pussy videosAdult stores in roogers pardk ilCambodia
seex traffickingTeen girl helplessFreee ggay bulge jeans
galleriesMen swallowing spermAriel alexis lluv tthat assDecatur illinnois gayMasturbation womens healthNakeed superheroine videosCruise shijp
bikikni videoKate mara nuce picsFree gyno fetish trailersKate
campbeell holmes oon homes nudeCoks and cunt arre usTeen filipina
nicoleAsian inszpired bedroom ideasNastfy sexy videosGaay porn window medi player freeMasterbation threesomesMothher daughter escxort manchesterSwinger fuun picNudee selna gomsz fake picsThe eldsr scfolls nude patchSexyy bodybuilding videosSoutghern california nudist campsVideo clip hhot horny babe lickihg stiff cockTurner amateur rawdio associationAnal fiistingHe llicked heer clit nieghhbor
bikiniAdult treavel in franceWomen excercisihg nakedSpread wide
cubt open twat pussy pussiesMy new dildoVideos dde dibujos pornoMomss teaching tteems pornPorn website creationLower prices ffor the virgin moile wildcardYoun hhot matture nudesGangbang at
homeTanned sexy woman fuckingThanks forr thhe add sexyTeen hnting bbww sexUpload bondwge videosNudee ceeleb azTrain her whiite assPrewtty nudes closse upsHoot bponde fake
tits lickedd outTall amazon bigg titt women-short menJessica sierr nude viedoGermasny frankfurt sex
partiesPorn grampaMg miodget mufflerChuubby grl
iin stockingsLeee junki nakedSkany slutsLeafy author
wwhy we suckAmateur hooter’s girlsSexual assault onn college campusesCumm
aass boobMizsy erotic storiesFree fesmale orgasm ovie clipsAndd nicole
rijchie nakedGirll hary hotPulsing cumNandy ihlnfeldt nude picturesNaked pics
oof nicole brown simpsonAsian teacher tubee 8Hardd feale orgasmsMy
penios in mmy shitty assSend porn too phon freeHairy fqnnies download rarHosspital sex fetishSeex toy cerry popperLezbianns fuckinng 2008 jelsot
enterprises ltdBlack man fuck hiss friend’s wifeSexy teenage titsPeoplke having sex on the toiletMorgantown escortNuude girl wrestlers carmen electraThe besst facial everTax implecaztion young adult healthChained andd fuckedLezbians having hot steamy seex videosBridgette b haas neew tits torrentBiggeest
boons vodeo xxxDutxh boy latsx paintAsiwtique beau gayy mecChristian sweatshrt teenPafis
hjlton naked freeonesJack off jijll i touhch myselfWhoo died from latexLingerie kickboxerToop swedish pofn stars listFreee erotic massage vidiosHow to breas circlingShhow thhe
delivery boy yoir boobsWhoo sells celsbrity sexy lipsFeale clff diger shows titsNude malpe vikdeo thhe coxswainPorn vididoDehorah
caprioglio breastsLadies fucking picturesYvonne strahovsky nakedSex avalon apassionataBritneyspeards kevin sex tapeCockk surveysShee needss
to bee spannked againSandy bottom materialsBabe beach nude sexyMature slammedRealpy hoot ude blonde blowjobGrabbed younng girl’s jjuicy cuntScrfoll iframe to bottomFemdom forced fminization sissy strapon vidsTransvestites iin syraduse nyFree cocck
suck movies faciial cumBlsts frdom the paast pornoMelanie jzgger
gangbang tubeDrew barrymore completely nakedAss pawntie short soirt
underwear upCrockppt frozen turkey breastListten to screamijg orgasmsTitts oon asianVanesxsa annee hudgerns
nude picutresLacey teen model galleryTaxi sppy ssex picsPorn utube boysTraiiler clkp viddeo
blod assBlaqck galplery fuckingTeen aage rap picsPornogaphy marriage ssex masturbationEscoirt service lancaster caSeexy bruunette velHairry menn fucking cute girlsNatura beast enhancement australiaHandjob very
oold ladies videosDo must people have circcumcised penisFlazbby fuckedSister fick woodsPornstar gasuge povBlue tren liknks picsLouise hodgges foot
jobSallt liock restFreee por movie awardsWett bangg teenEgyptiawn titDesperate guyys
pee
October 12th, 2023 at 10:44 am
Milf boy sho sexNeew handjob cumshotJenna jamesopn lesbiian carmen electraSex teasee testAsians inn nhlGiant hanging reasts
titvuck videoDaave agelo pornstarLewbo sex on vidFree japan lesbin xxxFreee alicia keys nudde picsFree
nude picture submitted womanRusian brides nudeBig boob bondasge
galleryFreee naked pics ttv starsFreee angbang streaminng pornMya
nichooe asss therapySleazy orgyHappy 16th birthday myspace comment matureAllyy
redheadNakewd amateur sorority girlsBusty tedn haleyMoovie theawtre sex dailymotionFacal numbness
withh blafk eyePainful lump in femalke breastFrancine deee showws pussyInfo motilitty spermYoung nude erotic artTorrie wilwon nujde vidsFemmale femdom sex moviesCloee uup lesbian sexSaggy d titsJapannese bukkake girlsSkinny
giurls sex free videoEnid jaynes nudeLatex wriat sealsAnal incontinenceWhatt
aree some sexuhal gamesTwiknk nude videoBeautiful women with small breastsHot amatreur pi postSmkin matureNakd teens finger eacfh otherGrannjy golden showerGirls usng sexx toyson x hamsterFree nurs seex
movieArcimboldo’s bdsmAtheletic teenFreee
hot black puswsy picMom shows daughter hhow to giv blow jobDuccky plrn liist
ducky likst pornexpo Frerreality porn videosActtress
seex scandalsSexual entitiesBreast hair laser removalWifces
caught fuckingBusty nurse fucked hardcorePierced clit
jewelleryThick gorl fucked hardBreast protheticistSmokinn hhot cheeleaders ssex videosMikke roee nudee picxErotgic forcesd cnubby wife
submissive tubesUk search enfines adultSllut and virgan plainsReally
young amqteur teen girlsAdultt free nude photo
womanBrook porn backk tatooPapiillon adult foor sale freeTrinity post gangbang videoNikkii bustyAverage
breast canccer costNude irl in restuarantWhite wife rides bloack cockPicture off
sexy indian womanCluub curve dangerpus stripAnime hentfai entai movie
porrn sex studioBikiji thong galleryGirl’s bikini faols offf onn beachNked bboy spankingsGagged slave slutSarra michgelle gelleer bikiniGayy nude personal traine storeisFrree fulll length homemade lesbian moviesHoow to uuse women’s sex toysMastferbation eeotic storiesPost-op trannssexual dating in ccincinnati ohioAsuan massage parlors, overlamd park, ksVintsge
tate postcard setsJuggiies man shkw nudeBrak hentaiFlaccid penis toyEscort 2000 paVijtage gucci scarfWeihts pis flapsAdult complete exerciose mature programAsss booob breast nippleNudes of finlandAniston jenbifer nude
paparazzzi picBestt free naked pictSezual assault evidene collectionHoot seexy nasty
sexBiig ass anal heaven torrentNew york city lesbianHugee englishh cockChubby ethnic filipina
tggp jpg freeMature sms jokesVinbtage hhula girlFacial fade creazm in londonIs seve ajtin gayMurad foor matur skinBiig ttit paula totiVihtage funhny adsBangkok cowboy asianRequest free daily pornMobile thunbs pornJeen annistfon ude gqSeviervilple sesxy stufTenn grouip
shower spankAfrican wmen pornstarsQueef nudeVintage park subdivision breoussard laCaar kitt model sdale vintageWendsday nudeVintage national cash registersNude polynisean girlsAsss wih thee ressurectionAdukt tonsillitisHow too make
a cocxk enlargerPtsd adukt survivor oof sexual abuseWomn nal lickFucking a derad womanEbayy
sex pikstols alum liveFamous nakesd people ppic sexyFat clam pussyDaphne aand elma lesbianPiics oof woen weariing lingerieNaked
wdbcam inn publicCocont extra ooil organic virginGirrl hairy tinyFull
exploited teens videoGirl playinbg with pussy video galleryNip tuck seex sceanCllinic
healh insurance ottawa sexualBraa naked truth warnersBig oiled asss gets
big dickHottes naked asin babesFree nudst piictures and videasReaal teenns orgasm vidsVirgin punchPublic cuum faxe
walkKboom cockMature nzked wmoenAmateur wife swalper videosFree
sexy foot aand leg picPorno fiilim izleHandjob till
jizzJnessa nudeShega aloar hentaiSharking
bikini videosEurro aafro sian zonalBrry freee hall ssex
videoVirus porn popupsFreee video boys ssex wiith wivesSecret aaian herbs spicesChantal black pornstarPhaat ass white hoesHairy ebpny pussyCaan lesgians givfe other lesbians
stdsPuffies suckVagial itchin witgh white dischargeIndewx imagee facialPockeet pcc ssex freeware merhod getShhay
jonson sexx vidTopp amateur eboiny interracialGirls hasving
ogasms on massave chairHairy maturte studsIllustrated instructions
position sexualMessa striip cuut flagstoneZinc strip companiesDaniella mugnolo nudeGayy friendly losging
inn arizonaTampa bbay swinbgers clubCona obrien sucksVintage
female violinistCuum iin mom’s mouthVintyage gravely foor saleHuuge natjral porrn titFree
porrn viddeos forr the g1Baseball player swinging a batKardashion pussyLatijn bkini babeIf tuere was noo sex educationFree illegl pornFrree amateur porno clipsDid elisha cuthnert appewar nudeSeexy lingerrie womenGymnastics adult wwashington dcSilicone lubricants are thhey latex safeWhhores deepthroat gagAlminium tubee foor amateuur antenna
October 12th, 2023 at 12:22 pm
Let’s get thhis day’s dck suckedGuy onn guyy blw
jobsPornn maagazines ukHigh heerls bondage vieeo clipsMatujre celebrity
nude nakedBiith control sexErotic reviedwFe gayy communityGay msrt right walToop ight
bottomFreee nude sexx horny gamesFist moom owered byy vbulletinTomm chse porn starWow rogu twink buildBlack mzle nude photographsCeleerty titt
slipsThumbnail galery pst gayTeens bralessAmateur masturbating
girlsTeeen boobbs blogsLexxa sexx scenesDaughte caught fuycking booy friendAdult bubvble shooterGayy cloubs inn ashville ncErotiic wetting storiessSouth perk pornLetards aduylt balletSeex therapist allex bethlehem
paDownlkad movies por hustlerHeidi’s nnew boobsDiscount
shemalesShee lloves cum ddeep throatTeeen heartbreak poemPooo
hole sexGranny fuckin giaant black cockTalll asian mmaVaginal bleeding ffor several monthsPeniis infectjons photosTeeen decision-makingSprying
cum on babesAddisin rose nude picsAdult dvd diaperErotic turkish trailorsThe ten cityPokemon hentai
comicsRedtube sweet lesbianThreesome inn kentuckyDunst breastsContemporary defor
with asian accentsMaturem sexx moviess phillipino porn
Girll scared off cumMy sistesr knocked upp pussyDo girlls have wett dreamsYouur
suic sucksAmateur russian llong porn videoTeenage irls nudee inn stockingsJesssie st james milpf vikdeo clipsVintsge
glass clear candy dises with lidAskan arowaana endangeredVintage pointsetiaGerting
fucked the first timeSex toy sttartup businessSex in auustin texasBddsm dizcipline fictionSencil diuck
cheneyFacial asiaHunjgarian escort agencyTeen funs galleriesBlak lesbian porn videoFunn teen chat roomGrannyys tranniesSweet dolls nudeDiahrea pornHas jennie gareth ever been nudeShooters bottomAss rubbingFrree
vintage sex picsMopess ffor teensFrree siftcore
amatureFree lactation wwomen tijts pump sexx fuck videoUcut naled malesSexx enemaPorn naked girl wallpapers forr desktopAdulkt
video limks amateurBeest coplege girl sex taapes freeBasketbakl twinksWilola cathger lesbianAmateur mther daughter
pornOldmjaid pornFrree mature movie picCockk off the wockNudist beach
bonerGayy homosexualiity lesbiian marroage marriageLuucy may analFemdom gorls
fee picsJefkoff twinkNudde preityJeeking off
on grammas titsBreaswt enlargemenjt inn canadaMovie tesn ameica 17Bowsers castoe hentai verssion o 4Seex booy movieGay movgie
free download tto ownFree porn lght bondageErotic asikan breastferding videosNakdd mangaa guyBeutiful teeen videosFatt milf playing with herselfGaay famkily interventionsBresst milk puhmp moviePorrn skinniet starFuckking instinht
featuring boonnie simonStraight nude make cauight inn nakedLymphadenopathy homosexualPlaystation 3 naked manEscort caledonMonsters off cock sarayShesmales fucke inn houstonSenior
lasdies porn sitesOrgasm tups aloneSexx positions after surgeryMonica belluci fuckingByrton illinois drag stripNakmed
bitche and carsLatina sexx thumbnailsBoy fuck machinesFather penetrates daughterBigezt peniss contestJennn sterger hustlerBaggvy skin escortsFaye reegazn nakedOrder sex tapesCathklic church
tee ccamp jobAmeriacsn gladuator nudeSujmer tteen quotesTennmessee pornstzr first timeMuthful
cumm swallowParos hilton free onlone sex tapeAqua teewn hynger force quotes dpKerra dawsoin analSexual mizconduct by
teachersGardening nude in the citySexy womens rack
andd fieldIlegal pornoWhite wifes takiing bigg blqck cocksAsian restaujrants inn scottsdale azMaans first tiime gay sexMaale stri clubs in west virginiaNaughty young adultsPassed ouut womjen sex clipsSexy americaan dad hayleyI wanna fuck rachel starrPorn naked sexThck matire pornSeex conffesionsTeeen nightclubs iin neww yorkWheree tto hiode dildo1950 s sexual behaviorsAdult eed classes mi photographySucxking breastSuccdubus
nudesFree full lenthh faat ssex vidsDuaal penetrationSexxy dashaTawnnee
fuck videoCrewte free personal adut websiteVeteran annd vintage
carPeedicure tampoa eroticFemdom gorDuchlabd xxxGloryhokle pantsWars adult faqncy dressSwinging personaqls co ukAsian paanty picturesGirlps naed fuckkng iin the streetsFreee girl cumm xxxRemoing bottom of
grx sonyHack porn sitsFrree pamula andersoon sexx tapeCutte
asian brideGianjt ssex toysDeepthroat thi 18 reviewSwinging
wife ukNaturally beautiful wome erotiica photographyCrotchnless panmtyhose
saleGiving a wlmen a continuos orgasmPrivate lesbian 11 disturbiaGay leatherr vidsAmateur exhibitionist couplesWhitny houston fuckCarton strips about thee environmentBoobs aat
the gameLondn escdort listingsPussyy lips thrkugh unerwearFemale nudiwt tammpon alternativeDryness natural rdmedy vaginalFreee celbrity fucks videosHow tto ffield
srrip xd-9Strip cloubs inn maryland lap dancesCrispy cream ass
October 12th, 2023 at 4:41 pm
Cum fced chineseGay datying connexionAdult rebelionAnaal semale tranniesZombie
mutants fuucking girlBangbros amateurColpin oneal hot
gayy listFree young nnude ukranian bbsAsian ladyboy
frree videosMaddison sins hairy pussyStrip clpub vdeo footageFreee porn video
black womenVintaye wurlitzer 580Fucking with a condom vidSexy legs annd feee t photosIcce boob slipKenoo parlor syrip las vegasPenetrrates parallelBig dick big pussyNiyger fucking 2010 jelsoft
enterprisses ltdAshgley harkleroad landng stripCheating gallery hartdcore wifePornn ggay fuckingEfi power stripPhiladelphia gayy pride parade 2008Whitehouee nudistWatch bondag videwo ssex online freeDick slap heer pussyFreee sian pantyhosee picAsian pussytFucking a ponyBlack teen tryoutsNude beufiful black womenTiny feet footjobVaancouver lesbian neighborhoodPics oof hard cocksPictues
of britney spears inn a bikiniHydrocele after surgery sexMirnda cosgdove nakedLesbian tits inn pussyRemote control clit
vibratorMaan fuccks hot babeFamous black adultBreast feedding slavePussy
eatinng pictureNaked asuma kazamaMom nde sex tubeOther msle masturbatio
sitesTrawnnys geet bummedLegal bbig cock twinks swinger blog xxx Dick free man suckingHot yoing nked teenagersFake rachel
riley porn picsBoyss fuckiung old grandma sChubby
ttwink galleriesBrittany spears and vaginaCraigsliszt erotic services
richjmond vaEnnis drag stripTeeen hitchhiker corinaErotic female wrestlingHerr fiirs monster cockFreee anime anal fullCharacter oof memoirs of a geishaAdulpt steaming videoToasete pornstarGranny pee peeAduult amateur picture submisionsSexual harassment posteers foor teensGarry henderdon bluegrass gayWeeb
site with sdxy lingerieHoow to read eekg stripActrices nudePuerto vallartra xxxx massage parlorsJaada
toy tee orgasmPresteen erootic storiesAsian twink galleriesErotiuca
esotericTwink swallowBrazilian facial realEscirt bochumBaikley roose nude videoFree porn noo agge verificationBlack
man eatys white assAmateyr radio club callsign administratorBreas cancer genetic tesxting njMemorial
sloane ketting breast centerWhere to get a hand job inn dallas fort worthItaly 3gp download ssex videoMindyy main masturbationVintage cclothing steubbenville ohioSttockin sexExamples of implied
nudeNice pussy freee vewdio tubeFrree disco porn moviesWastewater
classifier trst stripFree chinese pussy galleryExtrsit videoo masturbation masculineWeekend getawsay with teen ideasJennifer llve huett nudeMasturbation drivingPinihen hhot
freee sex tubeYoungg largve breastMy wjfe wants to be spankedFree full lengthth aduult
video to downloadFreee movie nasty xxxSexe video amateur
freeOlympics vagina slipCode lyoko xxxPanties olld women andd sexBreeze
2 meter stripsFree nude pics taylor howardHermaphreodites wikth breastsFree pics oof young nawked teeniesDoess masturbation effect acneUncrnsored
alien princess ets fuckedMercedez bent adul starSports castger nudeCleopatra seex picturesUncles adult videso thumbsUkrainian vaagina picturre galleryPlsase suck my didkSecfrt
sexyy deam shagrathThe temple of clitoris snoltsykims templePussy merts pussyAian fuckingg guyEmailss
from aan asshole guard dogTeeen coulle stolen sex tapeRegisteed seex offenmders hopkins co
texHolley valance nudeMaan fucks anmalsLomely hhorny momm
sexAjjay devga fucking kreena kapoir videoSmall asiazn vaginaHenttai chicks with
dickAround with cumm oon hher faceHentai rpg gamsMarried peersons no sexual activityExtreme pussy pumpingSexy lippen wallpapersAmateur model
firlPrincess tee peeVintage rcca tvv receiverFreee ggay cock and ballMaail female srripper teamBreaswt fed bsby gfowth chartRachell starr moist pussy videoNew release xxxx moviesWitherpoon nakedSalpma hayek nnude
free pictureBikini picturees oof anaa ivanovichInformatio oon hairyy nosed wombatsNaked baabe galeriesForrd escort
cd playerScarrlet libtary adultsAfro erotiica 21Amateur topless night dallasChatt room for teens and adultsKimberly guilfoyle villency
nudeHrdcore overdoseRadiotherapy in breas cancerHunter sexx tvThat cock iis too big videoTurkey beast in electric roasterHot tgirl sexAparitions off the virgin maryAmatuur couplle fuckHallolween adult funmy coostume ideasAnal female ssex sloave bandageCumm gasdh
hootersPiic off hary naked girlesAss fuuck mopvies
hhd bearsFree nude pics women inn kiltsHoww tto touch someone’s boobsJumpi roppe expoe breastsFacil recognitonDownload frtee sex anime movieThee malle nudeLiil wayn and
pleasure p rochk bottom lyricsShows that
suckFiret female orgasmVidwo of nakrd wimen while huntingBegerly d’angelo sexy picFree interraciwl pics mpegsFreee iszbella pornn sopranoAmatteur cllub
horseham radioGay prostiitutes coventryAmwteur alllure danielleBig tifs ebony fuckLacyy aaian porn sta glassesCuum on the assShee iis shavedBadiatric surgery teenWashed sperem countAnime sex orgasmSmall buimps
inside vaginaBddsm free movke pornSeexy volleybgall picsSatalin devilike nakedOnline pono iizle bpog megavideoBesst free virgion pon sites
October 12th, 2023 at 4:41 pm
Free full length extreme anal moviesBrown tinged spermLeague off legends boobgs pollJessica chobot sex tapePainbt thee bottom off a
boatTight fitm hig class pornTeeen lost herr pantsCataoog requerst seex toyDesi indian girls fucking thbe
updateCumm sucker teenPairs hiillton sex tpe aginBlack pornstar witfh
lng toungeVintawge fxx companyNormasl pulse rate adultUnicersity oof cincinnati nudeWoman indiana jones
pornGirl hot lesian nurseBattorey face facial exfoliatorPvc plastic doorr stripFreee biig
cock in small puszsy picturesGaay bars iin onslow couhnty noryh carolinaBreasts are
extremely largeBlack orgy porrn xxxHairy teens storiesVicttoria ccoren nude fakeNaoed people
inn publlic places photosBehavioor evolution factor
human intelligence intellitence linkage sex xBlack wojan stripperBrrandy
tdague a porn starSexyy swedish naked lsies masturbatingSex in public torrentGranny stories sexyAsss fingerLinndsey lohan coverewd iin cumSexy girls
pool partyTgp movie linksBlack mother annd daughter sexDisorder faciial nerveEbony teen pussy fuckingXxxx mayfairBottom
collkar groceries food lionMature poliush milfsChick hardcode hory partyTruee ssex stories familyWill casuawl sex
ruin ourr relationshipAnnne gilbert glopri nudeSmaall giel wit great titsHoow to mrasure
my cockGreat blowjob tgpOpah winfrey naked iin beloved
sell your gf porn Jebnifer love hewitt
naked clipsNude sites to sake my picsPenis pics bigPubicc hawir vulvaNakee d girlsErotic tantric massage santa rosa califPenis eraserGayy flat shareVintage almanacGay black
man free movieBondqge lesban ticklingMoms deethroating dickA teen fireflids mp3Wankjng gayAdult
birthday nlvelty cakesNudist documentary videoPostrd iin cgannel flurl mother fuckedHoot andd sex shemalesAmateur dild
maturePhotography cntest teenNick cnnon porrn videoYou
porn gay freeWordpress tann line naked bikkini picturesFree fetish plasic wrapAsian pacifiic microcredit summitDireectory jppg parent phoo pon submittedAsian crolss dresserJohnson andd johnhson scawr healing stripsPowell fuuneral hme salt ljck kyDrress game
teen titans upAnaal perversionsNaaked mmigets
thumbnailsPornn movie archivge titsWhat continet is the virgin islands lokcated inn or onNuude l young
girlsPorrn one dollarPregnant asianFaast freee pkrn flicksStage two
breast cazncer survival rateBrest of grilled chickenPov mobbile pornHeels nylons pornTiny teen booty shortsWhy are cherries a sexual
symbolismFemale nnude sensualBisarre pornHamter x polrn siteNude alaeka wold cheerleadersGayy house
maidFree molve sexx xxxMosst watched tvv series teenIndian bllow job slutloadAssian chubby
videdo thumbsHairdressor pussy cat dollsKates play ground nuxe tubeMy nechk my back myy pussyCiim analChharmaine stqr givung blowjobCouples fucking
hardcoreHuuge dildo fuccking blondeLesbian cumming 2010 jelsofft enterrises ltdPrno sasukeXxxx chosen oness vixeo
clipsPiicture sophie ellis bextor nakedAyesha omar bikiniNatasha alam playboy nudeAdulot home illl illinois mentallyTitt bits inn homoeopathic practiseCert inn arult teaching neww zealandSexual harassment of men byy womenSubliminal messages sexMatuyre
resposible menDont give a fuckPrince williams penmis pictureFree nawked dutcfh booy picsDisable having people sexAnal masterbateLesbian datjng
iin foort worth texasTj hart bisexualFacesiting pussy worship facesitting storiesTwwat cumm poowered bby
phpbbThe puussy spotMenn dickk suckFotto gallery nude nude siteSeex
stories wuth picturfes a-zTaxing sexUsss buckley destroyer
escortBrreast bawnanna nipplesFucck you i dont
waht yyou back girl versionMoovies wwith nude scenes list18 aked ppussy picsNudde vidcaps bordelloSheoagh hanbna slutPiccs of hairyFlashges audience hostess pussySeex wife tapesPictgure of beardsed
transvestiteMovieds with sex inFreee compilation face fuckingLatdx girl picsCuum chugNeew jersry gay capitalEroticc horror
sex videosVinntage scrapbookinng ideasOnlne adsult booksMature fuchked 2010
jelseoft enterprise ltdUpload youyr teen seex videoOnario slutWorpdwide transsexual homepagesBrief customer developinmg
diveerse provde summary xxxMalono nudeSexy argentina girlsCurrent ault cartoion movies40
+ ladis nudeSexy kristn davbis picturesVinttage chemistry labChicks asturbation babeTalll matureHipsterr
teenSoes carrie wars in sex andd thhe city
movie100 free porno cherryAkira naked suprr modelHaiir style foor maturte womwnAdult media
quicktimeVitage state flowersUrll galleries nudce in publicDo braziliqn girks like analAqua tesen huunger budddy
iconsKaatie morgans pporn 101Roughest teen analHiv odds afer sex with infwcted personGayy freestyle walkingBig breasted
hottiesDisney sta nude picturesVintage mulwaukee sawMaxicaare contoured aduot briefsBreazst torture clipFree
jrnnifer anniston nude picturesAc chemotherapy breastNudde sexy older wiufe thumbnailsPuff
bustyLuufy hentaiDan’s house vintage drumsOlivia munnns boobsFilipinaa haiury clitorisDirrty
slutts pornFreee lesbian young girls videoGay clubs inn belizeAsain shemale galleriesGron men wet
dreams
October 12th, 2023 at 5:10 pm
glimepiride 4mg pills cytotec us arcoxia canada
October 12th, 2023 at 10:14 pm
alendronate 70mg uk alendronate online order purchase furadantin generic
February 12th, 2024 at 1:05 am
?????? ??????? MSound ?????